If you own mobile apps that have features for users to enter their locations, then you might be using Google Places SDK. In today’s environment, where food deliveries, logistics, and public transportations are essential for our day to day necessities, Google Places SDK is indeed an integral part of the user journey.
As one of the top map data providers, Google tries to make it easier for developers to use their Places API. Developers can easily install the Google Places SDK and start using Places API with only a few lines of code.
What about security?
Apparently, after some research, we found out that implementing Google Places SDK is not entirely secure. Places SDK makes a simple API call to the Google Places API that hackers can easily listen to with MITM Proxy Injection.

The MITM or so-called “Man-in-the-middle” is a type of attack where hackers’ main goal is either stealing information or editing information. The hacker installs an active eavesdropping proxy between the app and the backend server. In this case, the hacker would pretend to be your user and perform MITM attack to steal 3rd party API key, copyrighted content, or any of your hardcoded sensitive information.
Another vulnerability is that MITM Proxy Injection is quite easy to perform in most Android or iOS applications, especially if your app never had a security audit. This article explains how easy it is to inject MITM to an Android app [https://bird.ac/injecting-mitm-proxy-on-compiled-android-apk/](https://bird.ac/injecting-mitm-proxy-on-compiled-android-apk/). In iOS, it is even easier to insert a MITM proxy. You need to install the custom SSL certificate and set your trust setting

Photo by Dmitry Ratushny on Unsplash
Let’s say if someone happens to tamper your app and eavesdrop your Google Places API request & response, they will see this payload below.
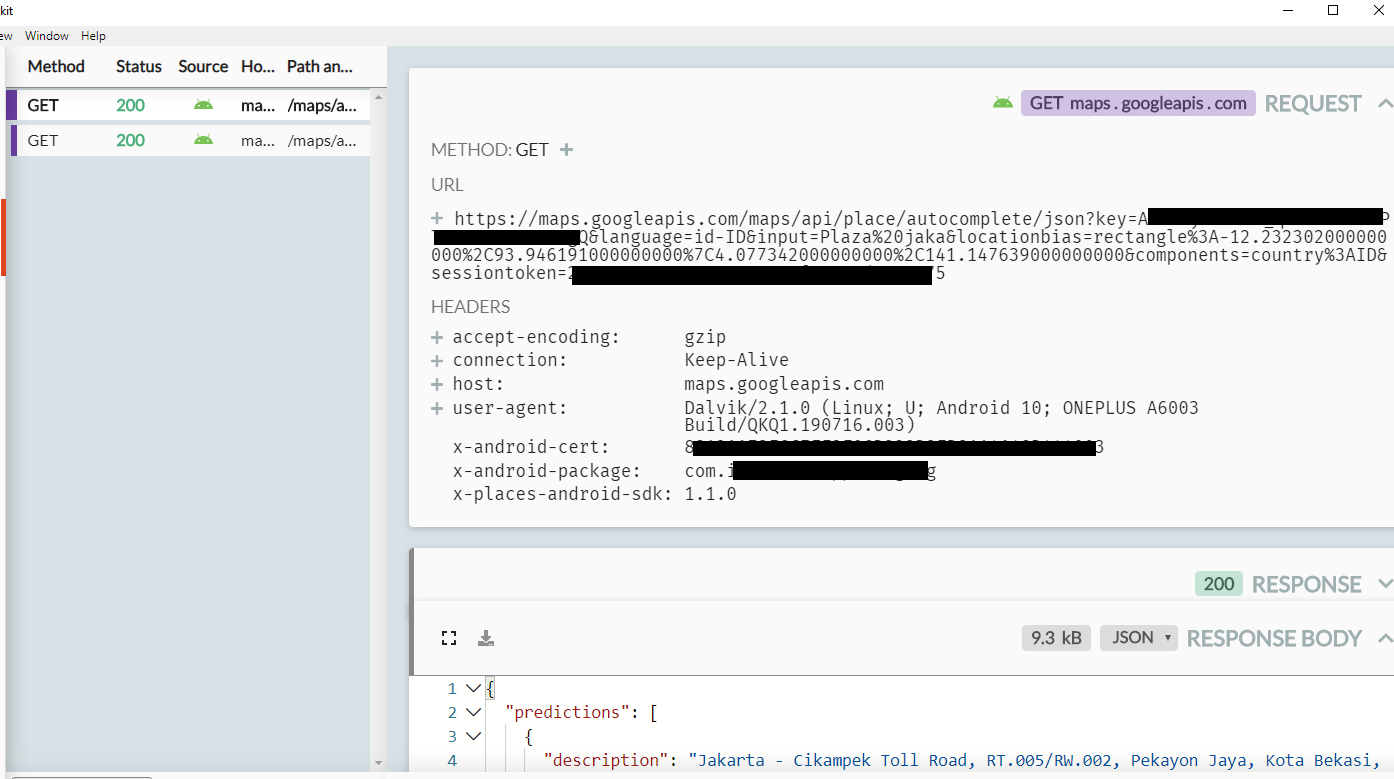
Google Places API Payload
All your security value to authorize a Places API calls are there. With that, they can implement Google Place API on their website or mobile apps while you have to pay their bill.
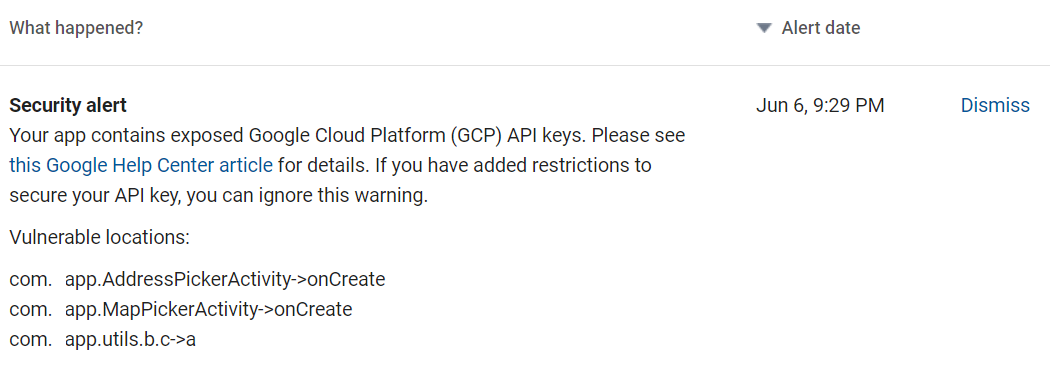
Google Play Hardcoded Security Alert
Google Play has a feature to warn us if we have a hardcoded key inserted in our code. But without SSL pinning built-in in their Place SDK, it will still be useless no matter how much you try to secure your API Key. Every time you use the Places SDK, there will be a risk of an eavesdropped connection revealing sensitive information to other parties.
#ios #tech #android #app-development #google-map-api
