Introduction
As a pentester developing new skills in different areas is very important as you might miss something crucial from one approach. Android pentesting is one of them, but it requires a dedicated environment and I will explain how to setup an easy one. So let’s begin!
Table of contents:
- Setup android emulator (Genymotion)
- Configure Burp Suite CA certificate on device
- Frida to bypass SSL pinning
- Bytecode Viewer (for static analysis)
Before installing emulator, I would recommend to install any Linux based distro or Santoku, which is especially designed for mobile pentesting. Installing Santoku is out of scope in this write-up, but you can follow up this guide to setup.
1. Genymotion
When starting out learning, android emulators are the great way to get experience with a variety of devices having different API levels without costing much and free version of Genymotion provides exactly that with great User Experience and easy to configure nature.
_Note: VirtualBox is used as a core by genymotion to virtualize Android operating systems. So please install VirtualBox in your system in order to proceed: _link
Genymotion requires user registration to use its dashboard and for that first you need to create an account: link
After completing your registration process download its installer from hereand install it in your host computer.
## Make it executable
$- chmod +x genymotion-<version>-linux_x64.bin
## Specify your path, here i am installing in user's home directory
$- ./genymotion-<version>-linux_x64.bin -d ~/
Once Genymotion get install now you can sign in using your credentials specified in the registration process and use its dashboard which looks like shown in Figure 1.
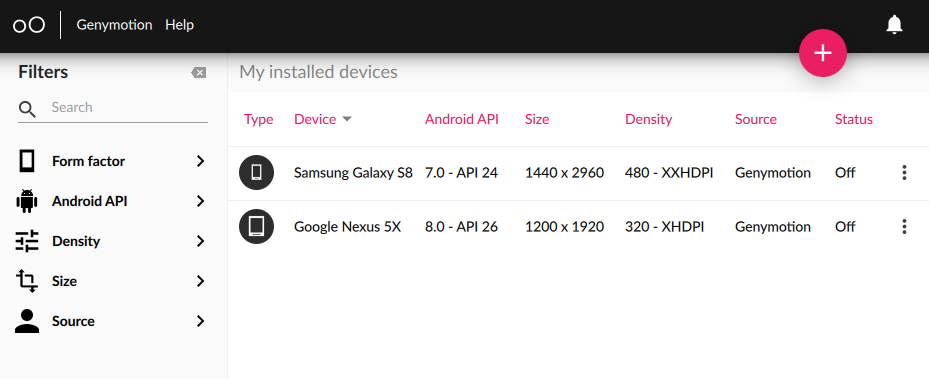
Figure 1. Genymotion Dashboard
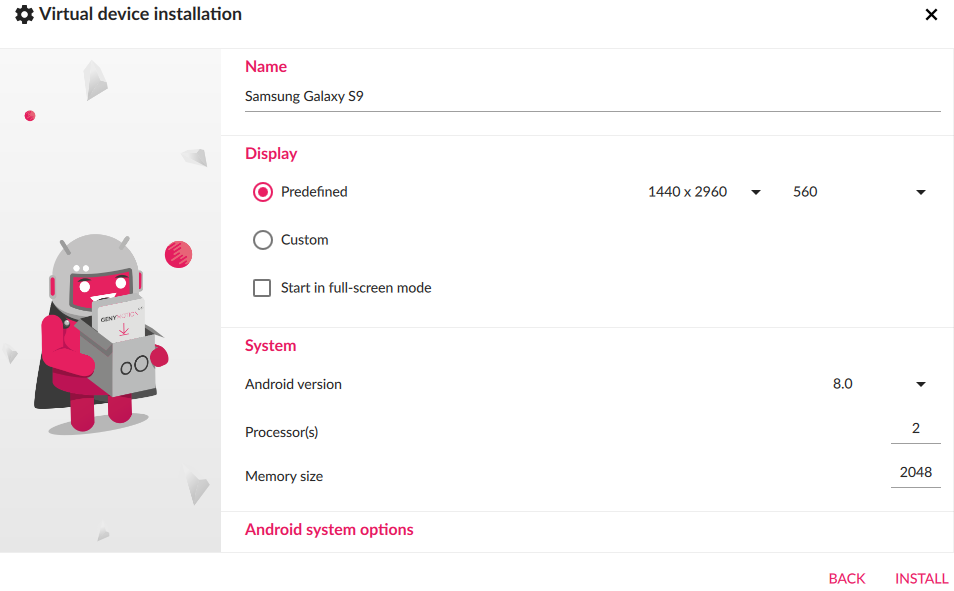
Here I’ve installed two devices already, but you can install a new device by clicking on plus icon at the top right corner and selecting your desired template and for this example I will install Samsung Galaxy S9 (8.0 — API 26)
#android #cybersecurity #pentesting #bug-bounty
