According to a Netcraft’s study of the secured (SSL/TLS) sites they monitor, 95% of them are vulnerable to a simple man-in-the-middle attack because they didn’t correctly implement HTTP Strict Transport Security (HSTS), a widely-supported security feature that prevents unencrypted HTTP connections to a server.
Let’s see why it’s happening and how we can make your website secure, again.
What is HTTP Strict Transport Security (HSTS)?
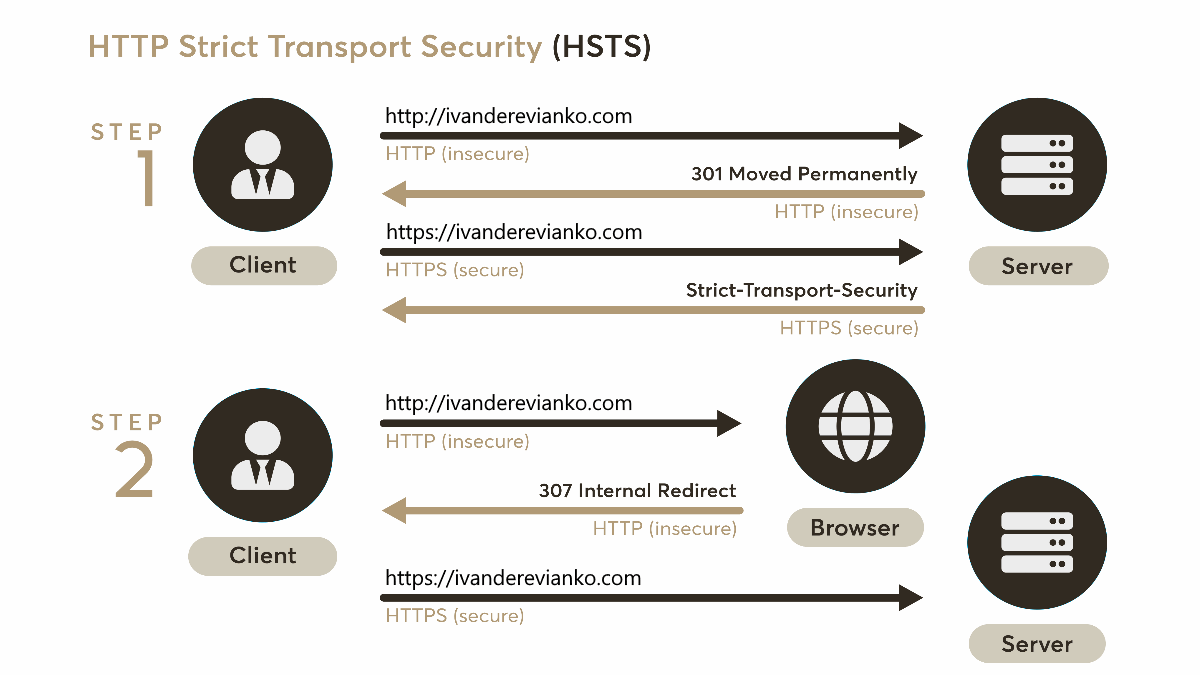
HSTS is a web security policy (RFC 6797) mechanism developed to protect websites against protocol downgrade attacks and cookie hijacking (wiki). When someone enters a website URL in the browser without http:// or https:// prefix or follows the http:// link, the initial request to the webserver is sent unencrypted. A correctly configured webserver should immediately redirect the user to the secured URL. Unfortunately, an attacker can set a man-in-the-middle (MITM) attack to intercept the first HTTP request.
HSTS is designed to help with this potential vulnerability by instructing the browser to always use a secured HTTPS connection to access the webserver (even if the user manually enters URL with the http:// prefix).
To enable this policy, a website should send the following HTTP response header:
Strict-Transport-Security: max-age=31536000
When a browser receives this header from a secured website, it will access this website using HTTPS (SSL or TLS) for the next max-age seconds.
You can also specify this policy for all subdomains by including includeSubDomains directive to the response:
Strict-Transport-Security: max-age=31536000; includeSubDomains
#how to #security