Connect your serverless architecture on GCP using Cloud Functions to your MongoDB Atlas database using network peering and private clouds
Serverless functions are great, and Google Cloud Function makes them really easy to spin up. However, given the fact that they are serverless, security can pose an issue. How do I whitelist the IP of my Cloud Function in my MongoDB Atlas account if the IP is always going to be changing? We could just use 0.0.0.0 , but then we are open to attackers hammering out at our servers! We need a way to protect ourselves against these attackers while still being able to have our functions speak to each other.
In today’s article, we are going to show you how to connect your serverless Cloud Function and GCP instance to your MongoDB Atlas database.
How It Works
In a traditional non-serverless environment, a simple way to defend against attackers is to just whitelist your IP addresses. You get a server with a static IP and tell your database that IP is the only one you will accept requests from. Piece of cake.
But in serverless architecture, the requests will always be coming from different IPs. The way Cloud Functions (and other serverless function providers (or “Function as a Service” aka FaaS) work is that every time the serverless function is triggered, they essentially spin up a new VM or instance with all the code you have and run it. This means you can’t whitelist the IP since it will always be different.
The way we are going to still be safe is by using a virtual private cloud (VPC) and [adding serverless VPC access](https://cloud.google.com/vpc/docs/configure-serverless-vpc-access?hl=en). This is a way to virtually pretend that all the services that we need (GCP and MongoDB) are in the same cloud/network. We simply add these services all together in our GCP instance, and then we enable Network Peering on the MongoDB instance.

Original Image from GCP Documentation.
The image above is _almost _accurate, with the only difference being that the MongoDB instance is actually _not _in the same virtual private cloud network as the GCP instances. This is possible since we can host another VPC on the GCP that both our GCP instance and our MongoDB instance have access to. This is possible because MongoDB and Google Cloud have a nice integration that allows these additional services to be spun up easily!
We then whitelist this third VPC middleman on our MongoDB instance, and presto! We no longer have exposed IPs to the world! Let’s look into how this is actually done.
Step by Step
You can find a version of these steps in the MongoDB documentation and the Google Cloud documentation. Note that this only works if you have an M10+ version of the MongoDB Atlas cluster.
Set up a virtual private cloud on the GCP

VPC networks on the GCP
- Go to your Google Cloud Console Home.
- Go to VPC Networks.
- You can either leave the default as
defaultor add a new network here by clickingCreate VPC Network. - Be sure to grab your
Project ID. You can find this by hitting the dropdown (in this case, you can see mine ischainlink) and looking at the project ID. It will be next to the project name.
You will need your Project ID and VPC Network Name for the next part. In my case, the network name is default.
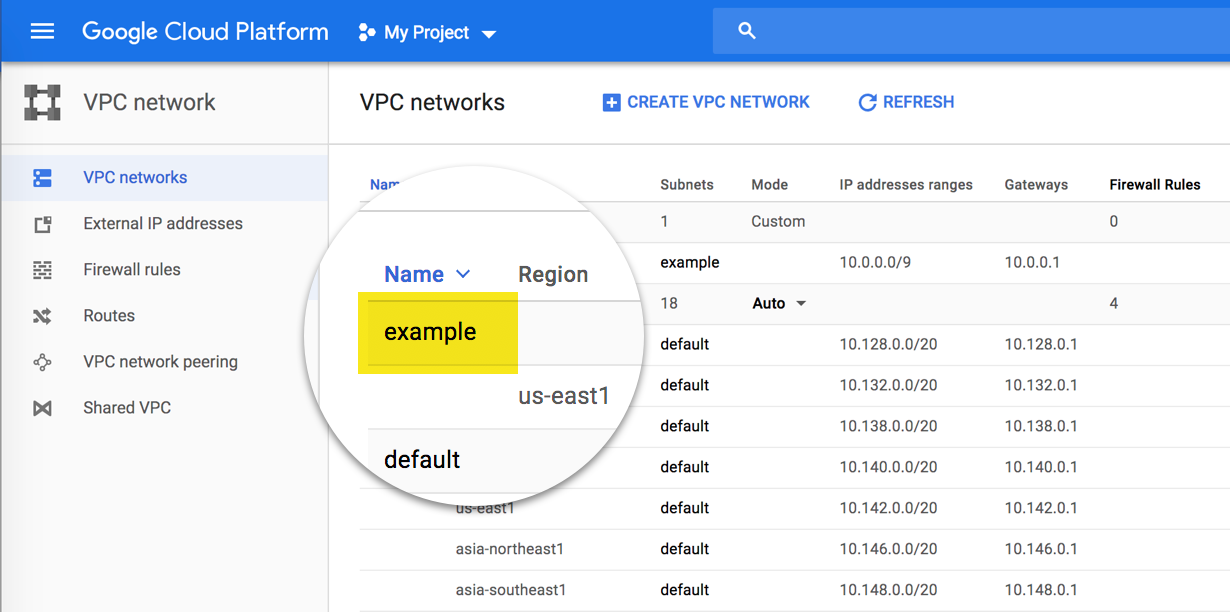
Original Image from MongoDB — the network name is “example” here.
Set up your MongoDB network peering
- Navigate to your cluster that you want the access for.
- In the Security section of the left navigation, click Network Access.
- In the Peering tab, click the plus icon to Add Peering Connection.
- In the Peering Connection modal, select Google Cloud Platform and click Next.
- Enter the required information in the Peering Connection modal.
Project ID
GCP Project ID of the peer VPC. Refer to the dialog for instructions on finding your
VPC Network Name
Name of the peer VPC. Refer to the dialog for instructions on finding your VPC Name.Atlas CIDR
CIDR block for your Atlas cluster. (You can ignore this)
#database #mongodb #cloud #serverless #developer
