I am excited to share with you all (readers), how challenging and yet how amusing the CTF was. At certain point I was thinking that what am I doing wrong but as they say ‘No detail is too small.’ So here is my detailed CTF walkthrough of CloudSEK’s CTF EWYL Program.
CTF Difficulty Level:
· Medium
Penetration Testing Methodology:
· Web and Steganography based Penetration Testing
Reconnaissance:
· View-Source (Ctrl+U)
Exploitation:
· LFI Bug
Tools:
· Decoder (https://malwaredecoder.com)
· MD5 Hash Decoder (https://www.md5online.org/md5-decrypt.html)
· Base64 Encoder/Decoder (https://www.base64decode.org/)
· JWT.io/ POSTMAN (https://jwt.io/)
· Image Metadata Viewer (http://exif.regex.info/exif.cgi)
· Steghide
Results:
· Capturing the Flag
· Access the submission URL
Walkthrough
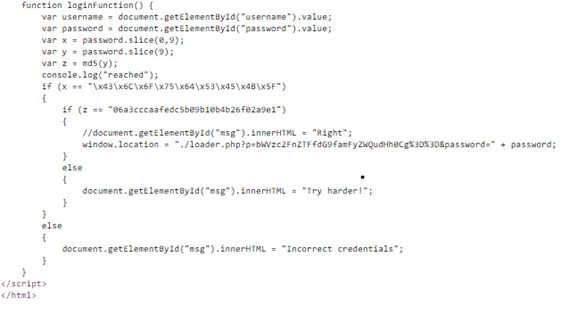
- view-source:http://54.244.19.42/ viewing the source code of the website for username and password to bypass the authentication.
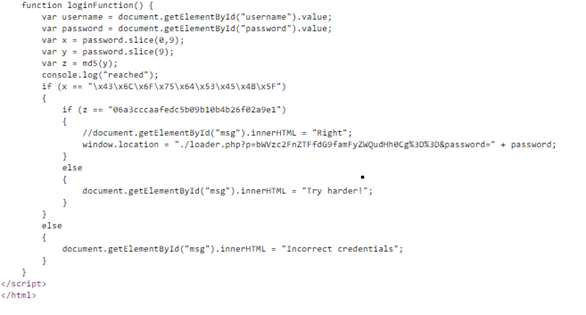
Source Code
2. Here we can easily deduce that the username is encoded as a hidden script and to uncover its real functionality we have to decode it.
#steganography #ctf #cybersecurity #bug-bounty #web-penetration-testing