The Microsoft identity platform is key to secure access to your web app. Users can authenticate to your app using their Azure AD identity or social accounts. The authorization model can be used to grant permissions to your backend app or standard APIs like Microsoft Graph. In this blog, a web application is discussed that does the following:
- 1. Azure AD login with user role: basic or user role: premium
- 2. Access to MS Graph using delegated permissions of signed-in user
- 3. Access to backend using application permissions and app role
The code of the project can be found here, architecture can be found below.
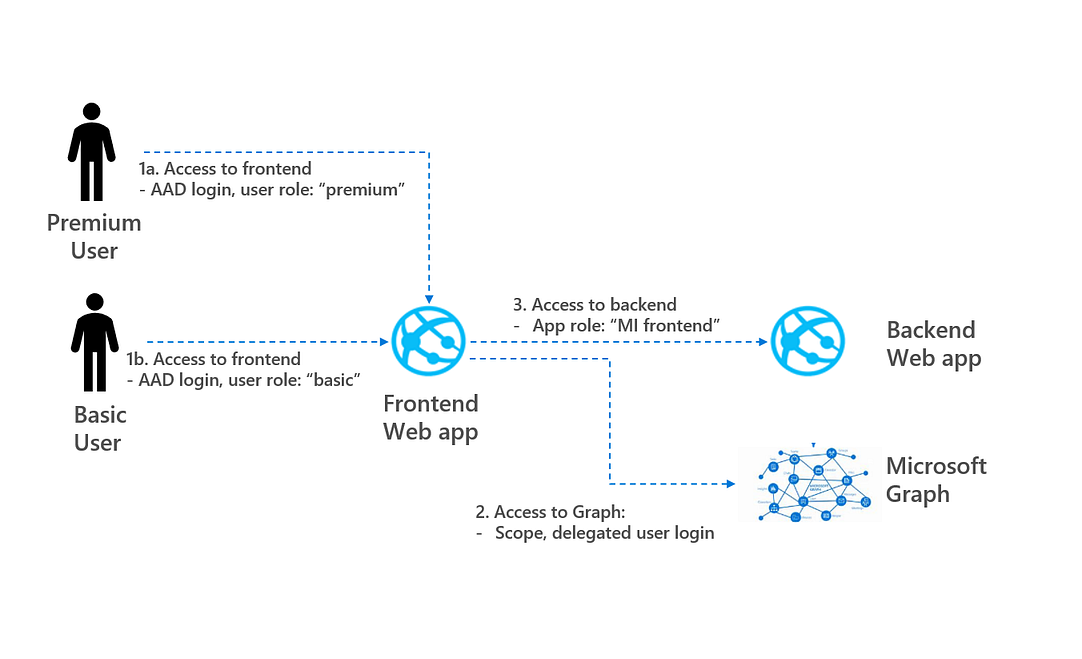
Project Architecture, image by author
The focus is to provide a working example using Microsoft identity platform and to “get your hands dirty”. The focus is less on explaining the internal workings of OAuth 2.0 and Azure AD. In the remaining of this blog, the following is discussed.
- Step 0: Preliminaries — set up frontend and backend
- Step 1: Access to frontend — Azure AD login, add user role
- Step 2: Access to Graph — Delegated permissons retrieving users details
- Step 3: Access to backend — Applications permissions retrieving data
- Miscellaneous: Other possibilities to configure project
- Conclusion
To learn how to access Azure SQL database using delegated or application permissions, see my previous blog. Notice that both blogs share the same git repo, so this project can be configured to access Azure SQL rather than a backend app.
#python #identity #azure #programming #towards-data-science
