This post shows how to implement an Azure client credential flows to access an API for a service-to-service connection. No user is involved in this flow. A client certificate (Private Key JWT authentication) is used to get the access token and the token is used to access the API which is then used and validated in the API. Azure Key Vault is used to create and provide the client certificate.
Code: https://github.com/damienbod/AzureADAuthRazorUiServiceApiCertificate
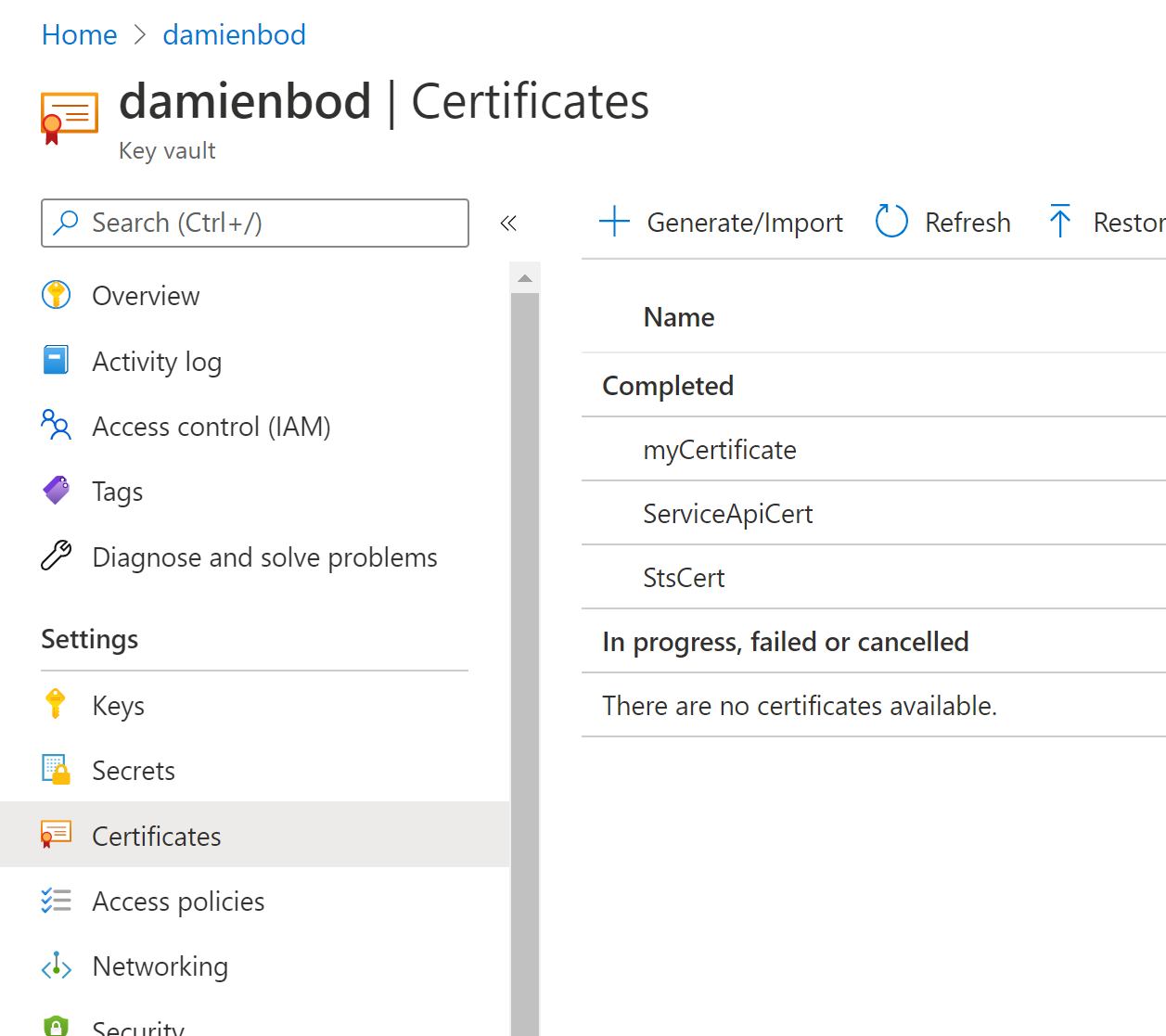
Create a client certificate in Azure Key Vault
A self signed certificate with a key size of at least 2048 and key type RSA is used to validate the client requesting the access token. In your Azure Vault create a new certificate.
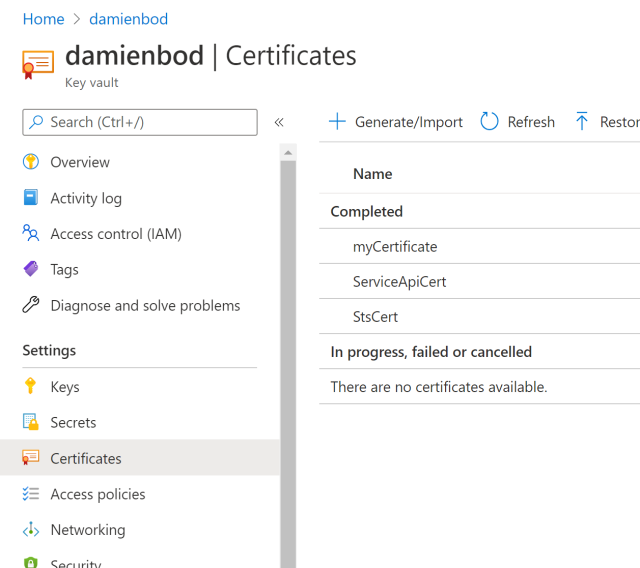
Download the .cer file which contains the public key. This will be uploaded to the Azure App Registration.
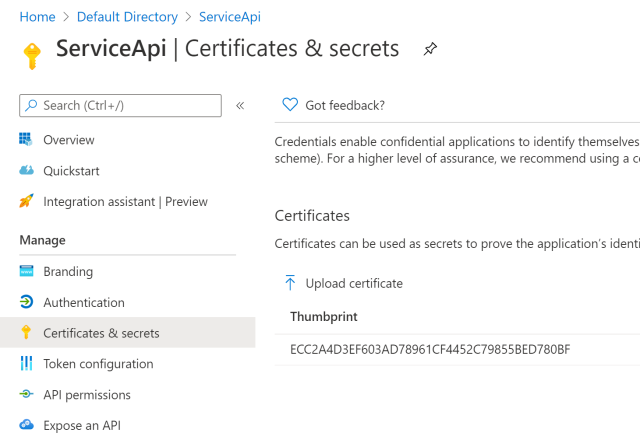
Setup the Azure App Registration for the Service API
A new Azure App Registration can be created for the Service API. This API will use a client certificate to request access tokens. The public key of the certificate needs to be added to the registration. In the Certificates & Secrets, upload the .cer file which was downloaded from the Key Vault.
No user is involved in the client credentials flow. In Azure, scopes cannot be used because consent is required to use scopes (Azure specific). Two roles are added to the access token for the application access and these roles can then be validated in the API. Open the **Manifest **and update the “appRoles” to include the required roles. The **allowedMemberTypes **should be Application.
#app service #asp.net core #aspnet5 #azure key vault #7523 #azpacr #azure #azure app registration #client credentials #jwt #key vault #microsoft.identity.client #microsoft.identity.web #oauth #oauth2 #private key jwt authentication #rfc7523