Network-Mapper (NMap), is the most famous scanning tool used by penetration testers. In this article, we will look at some core features of Nmap along with a few useful commands.
What is Nmap?
Nmap is the short form for Network Mapper. It is an open-source Linux command-line tool that is used to scan IP addresses and ports in a network and to detect installed applications. Nmap allows network admins to find out the devices running on their network, discover open ports and services, and detect vulnerabilities.
Gordon Lyon (pseudonym Fyodor) wrote Nmap as a tool to help map an entire network easily and to find its open ports and services. Nmap is also hugely popular, being featured in movies like The Matrix and the popular series Mr. Robot.
Why Nmap?
There are a number of reasons why Nmap is preferred over other scanning tools. Nmap helps you to quickly map out a network without sophisticated commands or configurations. Nmap supports simple commands (eg. to check if a host is up) and complex scripting through the Nmap scripting engine.
Other features of Nmap include:
- Ability to quickly recognize all the devices including servers, routers, switches, mobile devices, etc. on single or multiple networks.
- Identify services running on a system including web servers, DNS servers, and other common applications. Nmap can also detect application versions with reasonable accuracy to help detect existing vulnerabilities.
- Nmap can find information about the operating system running on devices. It can provide detailed information like OS versions, making it easier to plan additional approaches during penetration testing.
- During security auditing and vulnerability scanning, you can use Nmap to attack systems using existing scripts from the Nmap Scripting Engine.
- Nmap has a graphical user interface called Zenmap. It helps you to develop visual mappings of a network for better usability and reporting.
Commands
Let’s look at some Nmap commands. If you don’t have Nmap installed, you can get it from here.
Basic scans
Scanning the list of active devices in a network is the first step in network mapping. There are two types of scans you can use for that:
- **Ping scan — **Scans the list of devices up and running on a given subnet.
> nmap -sp 192.168.1.1/24
- **Scan a single host — **Scans a single host for 1000 well-known ports. These ports are the ones used by popular services like SQL, SNTP, apache, etc.
> nmap scanme.nmap.org
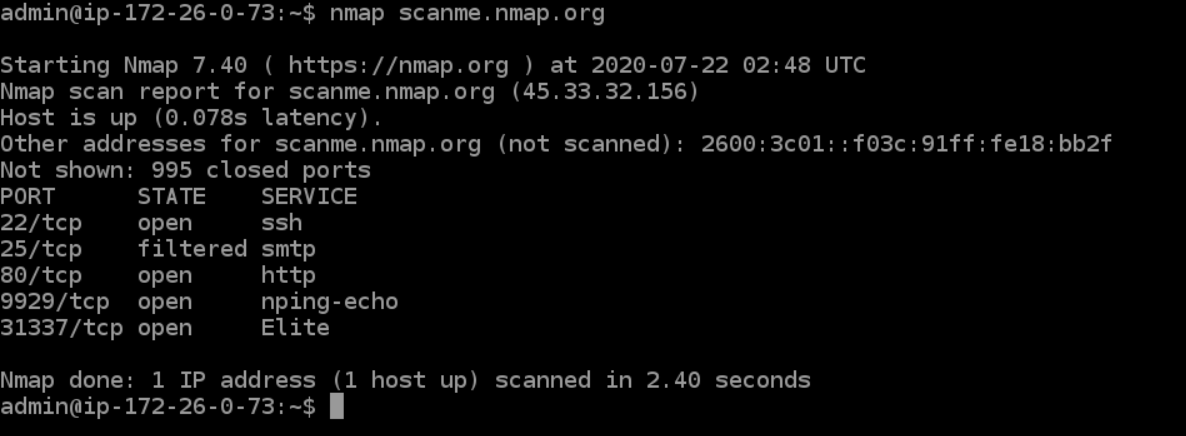
Nmap Basic Scan
Stealth scan
Stealth scanning is performed by sending an SYN packet and analyzing the response. If SYN/ACK is received, it means the port is open, and you can open a TCP connection. However, a stealth scan never completes the 3-way handshake, hence it’s hard for the target to determine the scanning system.
> nmap -sS scanme.nmap.org
You can use the ‘-sS’ command to perform a stealth scan. Remember, stealth scanning is slower and not as aggressive as the other types of scanning, so you might have to wait a while to get a response.
Version scanning
Finding application versions is a crucial part in penetration testing. It makes your life easier since you can find an existing vulnerability from the Common Vulnerabilities and Exploits (CVE) database for a particular version of the service. You can then use it to attack a machine using an exploitation tool like Metasploit.
#penetration-testing #cybercrime #network-security #computer-security #cybersecurity