The reactive AI Gateway of the Spring Ecosystem—built on Spring Boot, WebFluz, and Project—is Spring Cloud Gateway. Spring Cloud Gateway’s job is to factor and route requests to services, as well as provide alternative concerns, like security, monitoring, and resilience. While Reactive models gain popularity, the microservices you use will most likely be a combination of Spring MVC blocking applications and Spring WebFlux non-blocking applications.
This article will show you how to use Spring Cloud Gateway for routing as well as traditional Servlet API microservices. You will also learn the necessary configurations for OpenID Configuration Authentication, Token Relay, and Client Credentials Grant, all of which are common OAuth2 patterns that use Okta as an authorization server.
Prerequisites:
- Java 11+
- cURL
Table of Contents
- Pattern 1: OpenID Connect Authentication
- Create a Eureka Discovery Service
- Create a Spring Cloud Gateway Application
- Pattern 2: Token Relay to Service
- Create a REST API Service
- Route the REST API Through Spring Cloud Gateway
- Pattern 3: Service-to-Service Client Credentials Grant
- Create a Microervice
- Secure the Micro Service using OAuth 2.0 Scopes
- Update the REST API to Call the Micro Service
- Putting it All Together
- Learn More About Building Secure Applications
Pattern 1: OpenID Connect Authentication
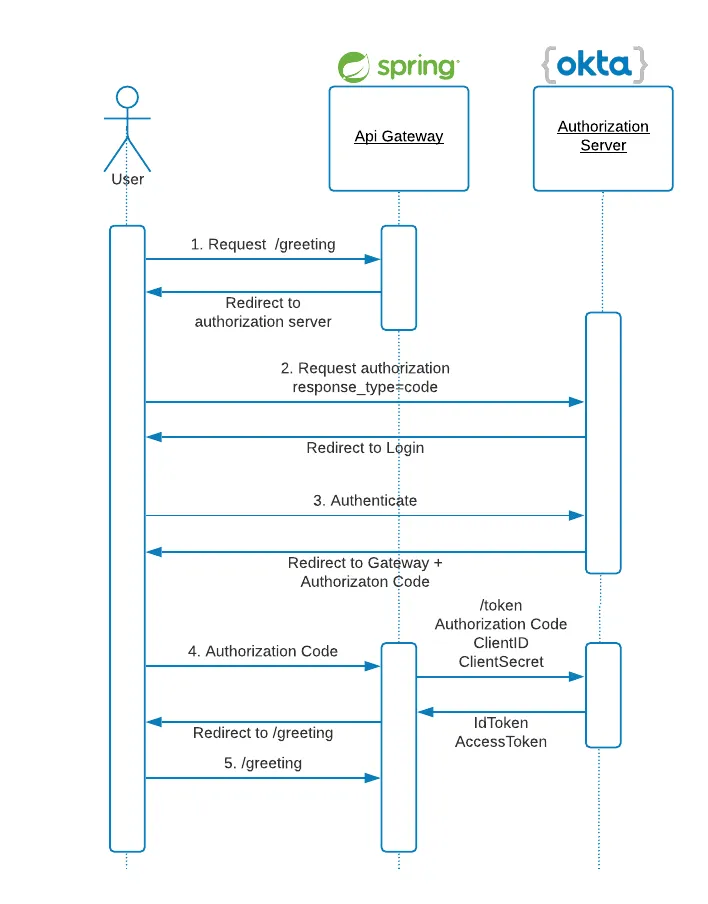
OpenID Connect defines a mechanism for end-user authentication based on the OAuth2 authorization code flow. In this pattern, the Authorization Server returns an Authorization Code to the application, which can then exchange it for an ID Token and an Access Token directly. The Authorization Server authenticates the application with a ClientId and ClientSecret before the exchange happens. As you can see in the diagram below, OpenID and OAuth2 patterns make extensive use of HTTP redirections, some of which have been omitted for clarity.
#spring boot #oauth 2