Building security into the fabric of your applications no longer requires you to be an expert in cryptography. The open source IBM Fully Homomorphic Encryption Toolkits provide code and development environment settings that developers can use to experiment with a different kind of secure programming model.
Access the toolkits
The toolkits synthesize 11 years of top-notch cryptography research into a streamlined initial developer experience that is accessible and freely available to anyone. Now, in the time it takes most people to brew a pot of coffee or declutter a desk, developers can follow simple instructions to get up and running with a FHE toolkit.
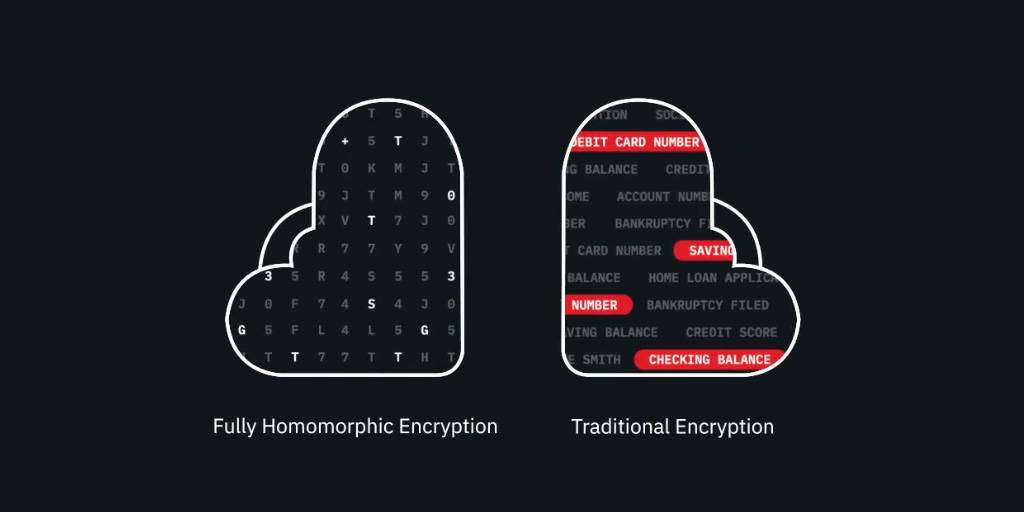
In FHE, security is not bolted on, it permeates the business logic by design. Most notably, FHE lets you compute on encrypted data which is very unlike the two common encryption paradigms most developers use — encryption at rest and encryption in transit. Since the business logic must consider that values remain encrypted at all times, it requires developers to rethink their traditional programming models.
Making it easier for developers to embrace cryptography
Right now, the average developer might have a hard time knowing where to start when it comes to adding encryption to an application. These toolkits make it easier for non-cryptographers to have access to this technology in a useful way.
By offering the toolkits on common platforms like MacOS, iOS, Linux, and Android, we hoped to create a friction-free experience for developers running their first homomorphic encryption application. At the core of each toolkit is a platform-specific IDE configuration, a complete sample program, and the dependency libraries needed to build FHE apps on top of the world’s most mature FHE library HElib.
Why open source?
In 2013 IBM open sourced the core library for Fully Homomorphic Encryption that forms the basis of the new FHE toolkits. But a library isn’t enough to help developers use encryption—they need working code, tutorials, documentation, and use cases to use the library successfully. The intent is to grow the toolkits and to augment the core library while staying true to the academic and pedagogical integrity at its roots.
By open sourcing the code and growing a community of developers and researches around the toolkits, more eyes will be on the code, finding defects, fixing security issue, and enhancing the encryption technology overall. With open source, anyone use, improve, or advance their research and business objectives.
Example use cases for the toolkits
Right now, every time you use a free search app for food or directions, you are revealing your intent or query data to the app’s provider. The data is used to market to you or aggregated for other purposes. With FHE, you can enact “privacy preserving search” that enables someone to search against a cloud service without revealing their intent (or query data) to the cloud provider. This concept sounds simple, but could actually be the undoing of the “free apps that mine you for data” that permeate our smartphones.
But this doesn’t have to be the case. Using FHE, you can create applications that give directions or offer product or restaurant recommendations without the apps revealing location or other information to the cloud provider.
A second use case is fully encrypted machine learning, where you can train your machine learning model on a large data set in the cloud. The data set can include your individual data, but with encrypted data from other individuals studying the same kinds of problems. Your model would benefit from this superset of encrypted data without individual parties making their data public. For example, what if all the health care providers on the planet could pool fully encrypted patient records to allow analytics on patient data without divulging anything about the individuals involved. Think of the progress that could be made with regards to treating certain kinds of diseases!
As you might appreciate, the concept generalizes to analytics and cloud storage for regulated industries in general. Basically most scenarios where information-sharing collides with the paradox of “need-to-know” vs. “need to share” would benefit from FHE.
Access the tools and contribute to the open source community
To make the tools available to a wide range of developers, we creaed them for use in four different development platforms — MacOS, iOS, Android, and Linux. Presently, the MacOS and iOS releases are available while Android and Linux are in progress. Android and Linux support will be coming as soon as they are finalized.
#security #mac #data #ios