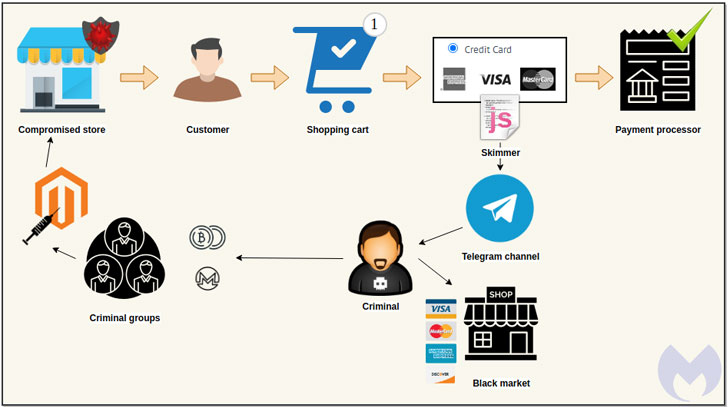
Cybercriminal groups are constantly evolving to find new ways to pilfer financial information, and the latest trick in their arsenal is to leverage the messaging app Telegram to their benefit.
In what’s a new tactic adopted by Magecart groups, the encrypted messaging service is being used to send stolen payment details from compromised websites back to the attackers.
“For threat actors, this data exfiltration mechanism is efficient and doesn’t require them to keep up infrastructure that could be taken down or blocked by defenders,” Jérôme Segura of Malwarebytes said in a Monday analysis . “They can even receive a notification in real time for each new victim, helping them quickly monetize the stolen cards in underground markets.”
The TTP was first publicly documented by security researcher @AffableKraut in a Twitter thread last week using data from Dutch cybersecurity firm Sansec.
Injecting e-skimmers on shopping websites by exploiting a known vulnerability or stolen credentials to steal credit card details is a tried-and-tested modus operandi of Magecart, a consortium of different hacker groups who target online shopping cart systems.
These virtual credit card skimmers, also known as formjacking attacks, are typically JavaScript code that the operators stealthily insert into an e-commerce website, often on payment pages, with an intent to capture customers’ card details in real-time and transmit it to a remote attacker-controlled server.
#data analysis