CIS Benchmark Overview
The following items are checked for this benchmark item:
- 1.7 PodSecurityPolicies
- 1.7.1 Do not admit privileged containers
- 1.7.2 Do not admit containers wishing to share the host process ID namespace
- 1.7.3 Do not admit containers wishing to share the host IPC namespace
- 1.7.4 Do not admit containers wishing to share the host network namespace
- 1.7.5 Do not admit containers with allowPrivilegeEscalation
- 1.7.6 Do not admit root containers
- 1.7.7 Do not admit containers with dangerous capabilities
In practical terms, these best practices may not apply to each and every pod being deployed in the system. When deployed on our Kubernetes cluster, we will use this as the default policy across the cluster, and will selectively grant permissions on a targeted basis.
Design Overview
This benchmark requires that Kubernetes PodSecurityPolicies be enforced for all pods running in the system. The following diagram shows the basic pod security policy configuration data model:
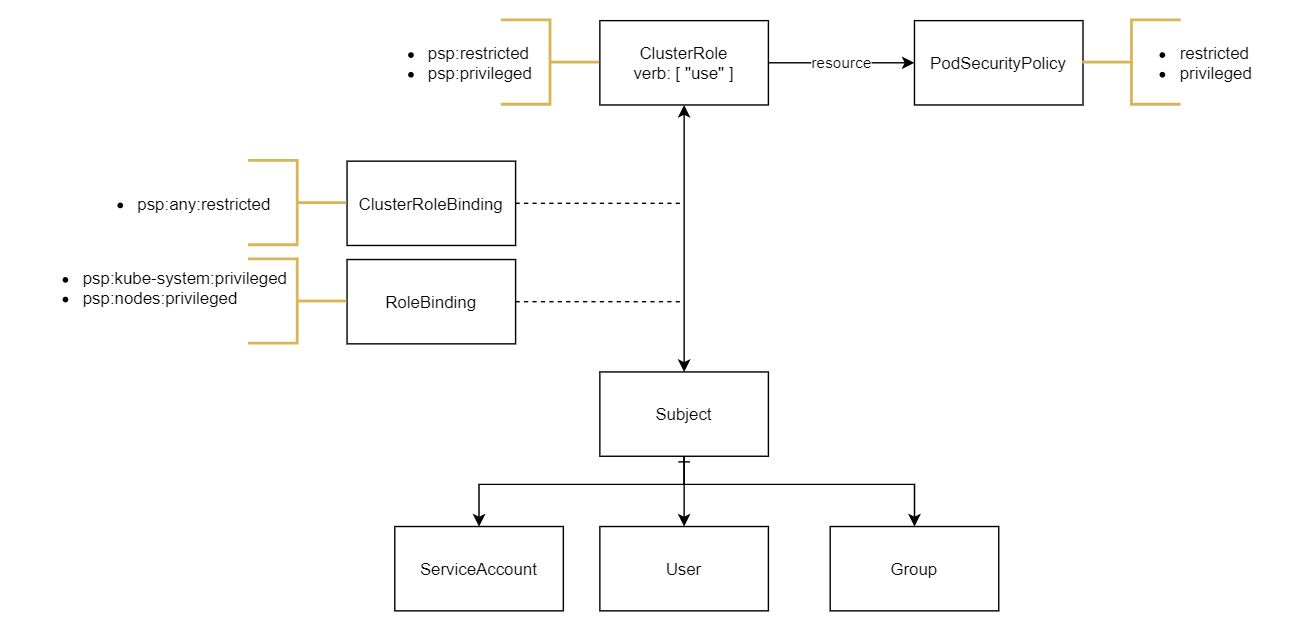
Practically, we may have some pods that will require some elevated permissions, but most will not. To cater to the requirements, let us define two basic pod security policies:
- restricted
- privileged
#security #kubernetes #containers #podsecuritypolicies

1.70 GEEK