Hey, hope you are having a wonderful day!
Let’s talk about a simple case scenario
You are building a cool application/website with your team and in some instances, you have to store user passwords in the database, now everyone who has access to the database can see passwords which are in plain text format what if I tell you that a hacker hacks your database using SQL Injection attacks or some other strong attack and unfortunately your application just got released and users are logging in with passwords. Now the hacker can just check the database which is already hacked and get the passwords and alter the user data or exploit them. To tell in simple words your application is less secure.
How to overcome the above problem?
The best solution for the above problem is to use hashing technics for storing the passwords securely and that’s what we are talking about in this article today.
What is hashing?
Hashing is the process of converting a given key to another value. A hash function is used to generate the new value according to a mathematical algorithm. The result of a hash function is known as a hash value or simply, a hash.
An image from audienceplay.com
There are different hashing algorithms out there some are secure and fast but some are not. We will be implementing sha256 which comes under the shah-2 series which is a robust hashing algorithm for now.
Sha256 was initially developed by the US National Security Agency in the spring of 2002 becoming the powerful successor of Sha-1.Sha256 returns a unique hash value of 256-bits or 64 hexadecimal digits with an internal block size of 32 bits. It’s a bit slower compare to Sha-1 and MD5.
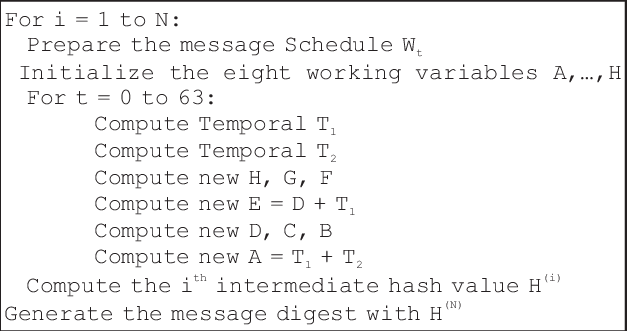
An image from researchgate.net
The above image shows the basic algorithm of Sha256. If you don’t understand it’s ok it’s just a few mathematical computations and let’s not dive deep into how this algorithm works we will talk about just implementation.
if you want to check what will be the output of the sha256 when any string is passed to it then here is the link.
I will be using Python 3 to implement this algorithm
To make this simple we will be using a python library which goes by the name of “hashlib”
Let’s start coding
#sha-256 #cybersecurity #python #hashing #database
