In the current era of hybrid mobile architecture, the Webviews and Deep Links are extensively used hand in hand. The former one is used to deliver dynamic web content while the latter one is used to make the applications more interactive.
In this story, we would be discussing the common security misconfiguration pertaining to the mingling of Webview and Deep Link. We would majorly be discussing the amazing security research performed by Bagipro on Insufficient URL Validation and later we would be ending it with some recommendations to mitigate this issue.
The story is also meant for the security evangelists who might not have the understanding of fundamental concepts of Android system. The Prerequisites section covers a few of the concepts which are later used in the story if you are already clear with these fundamental concepts feel free to skip this section.
Prerequisites
Activity
An activity is one of the Android application components, in layman terms it can be considered as a screen. It has a user interface, which allows a user to interact with the application.
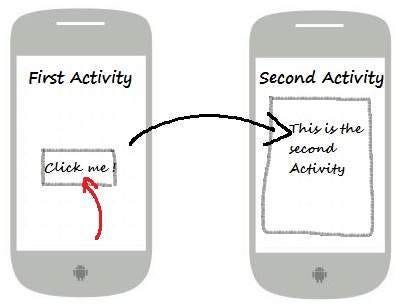
Usage of Intents For Communication
Intent and Intent Filters
An intent is a messaging object that allows communication between different application components such as Activity, Content Providers, Services, etc. It can be used for communication between application components of the same or different applications.
I strongly recommend you to have a look at Pg. 11 and 19 of The Grey Matter of Securing Android Applications paper to have a better understanding of the concept of Intents and Intent Filters.
Webview
Android allows developers to display web content directly into their application through Webviews. You can consider Webview as a dedicated web browser of an application.
What The Fish is Deep Link!?
While navigating web content on web browsers you might have observed the interaction wherein the browser invokes the specific application installed in your device to display the web content. The following GIF shows the interaction between browser and application through a deep link.

Deep links are nothing but specific URIs(Uniform Resource Identifiers) that must be handled by our application to improve the user experience. For example, fb://profile/33138223345 is a deep link, the URI contains all the information needed to launch directly into a particular location within the Facebook mobile app, in this case, the profile with id ‘33138223345’, i.e., the Wikipedia page, within the Facebook app.
Under the hood, we have an Android Activity which is to be invoked once a deep link is triggered. We usually call such Activities as Browsable Activities as they are configured to acknowledge the Browsable Category Intents. The Browsable Activity must have an intent filter defined with three elements viz. action,_ category and data_ as shown in the AndroidManifest.xml snippet below. You can read more about this here.
<activity
android:name="com.example.android.GizmosActivity"
android:label="@string/title_gizmos" >
<intent-filter android:label="@string/filter_view_example_gizmos">
<action android:name="android.intent.action.VIEW" />
<category android:name="android.intent.category.DEFAULT" />
<category android:name="android.intent.category.BROWSABLE"/>
<!-- Accepts URIs that begin with "webviewdemoapp://” -->
<data android:scheme="webviewdemoapp"/>
</intent-filter>
</activity>
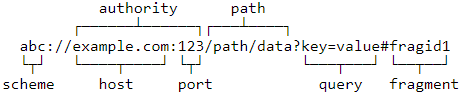
Note: We define the URI scheme in the data element using the android:scheme tag such that now Android system would not only acknowledge the URIs with this scheme(webviewdemoapp://) but would also invoke this Browsable Activity once such deep link is triggered, this is how a deep links work under the hood.
#bug-bounty #application-security #infosec #cybersecurity #android
