In this article, I will be taking a look at the InsecureBankv2 Android application created by the GitHub user dineshshetty. According to the creator, this vulnerable Android application is for developers and security enthusiasts to learn more about Android insecurities by testing a purposefully vulnerable Android application. I have left a link to application’s GitHub repository in the references below, which provides a list of all the vulnerabilities currently present in the application.

Disclaimer
I was inspired to make this article out of an interest to learn more about Android mobile application security. This article will obviously contain spoilers about the vulnerabilities present in the InsecureBankv2 Android application. I encourage readers to exploit as many vulnerabilities as they can and then come back later to read this article if you get stuck or want to see a potentially different approach to exploiting an insecurity. Without any further delays, lets jump in to the setup😃!
Setup
The creator of this application provides a detailed guide on their GitHub about how to setup the application and it’s backend server (see references). For this article, I used a _Kali Linux _virtual machine as my host device and a Samsung Galaxy S8 emulator created with Genymotion as my testing device. I also configured both virtual machines to use NAT and Host-Only network adapters. The specs for my Android emulator can be seen in the image below.
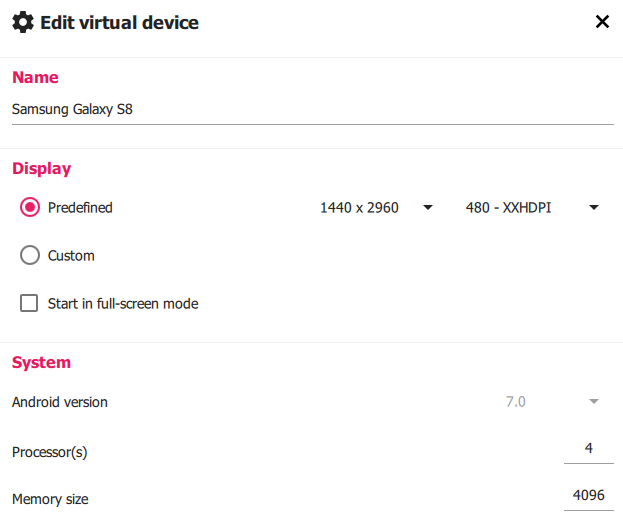
To setup the AndroLab server, I started by cloning the application’s GitHub repository to my Kali machine and then using pip to install the necessary requirements.
pip install -r requirements.txt
Once all the requirements were installed, I ran the HTTP server on the default port 8888.
python app.py
Next, I used Android Debug Bridge (ADB) to connect to my emulator and installed the InsecureBankv2 APK file.
N.B. Android Debug Bridge (adb) is a versatile command-line tool that lets you communicate with a device. The adb command facilitates a variety of device actions, such as installing and debugging apps, and it provides access to a Unix shell that you can use to run a variety of commands on a device.
adb connect "your-host-only-ip-address"
adb install InsecureBankv2.apk
Once successfully installed, the application icon appears on my emulator
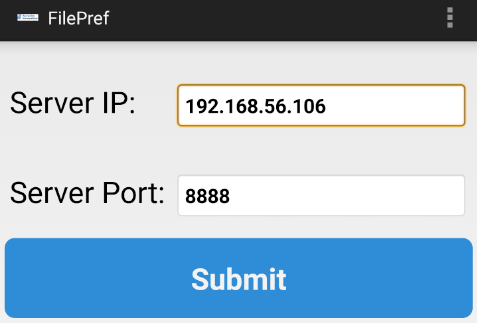
Once installed, the final step is to open the app and point the app to the IP address and port where the AndroLab server is running. In my case, this is the IP address of my host only network adapter and port 8888 for my Kali machine.
#reverse-engineering #cybersecurity #android #technology #application-security
