The “Internet of Things,” while difficult to define, has evolved into one of the fastest-growing industries in the technology world. Recent reports reveal that spending on IoT-related devices is expected to reach $1.6 billion over the next five years. Moreover, the increasing popularity of IoT devices has led to a significant increase in IoT app development. Though this poses obvious financial opportunities, it also carries with it some concerns related to security.
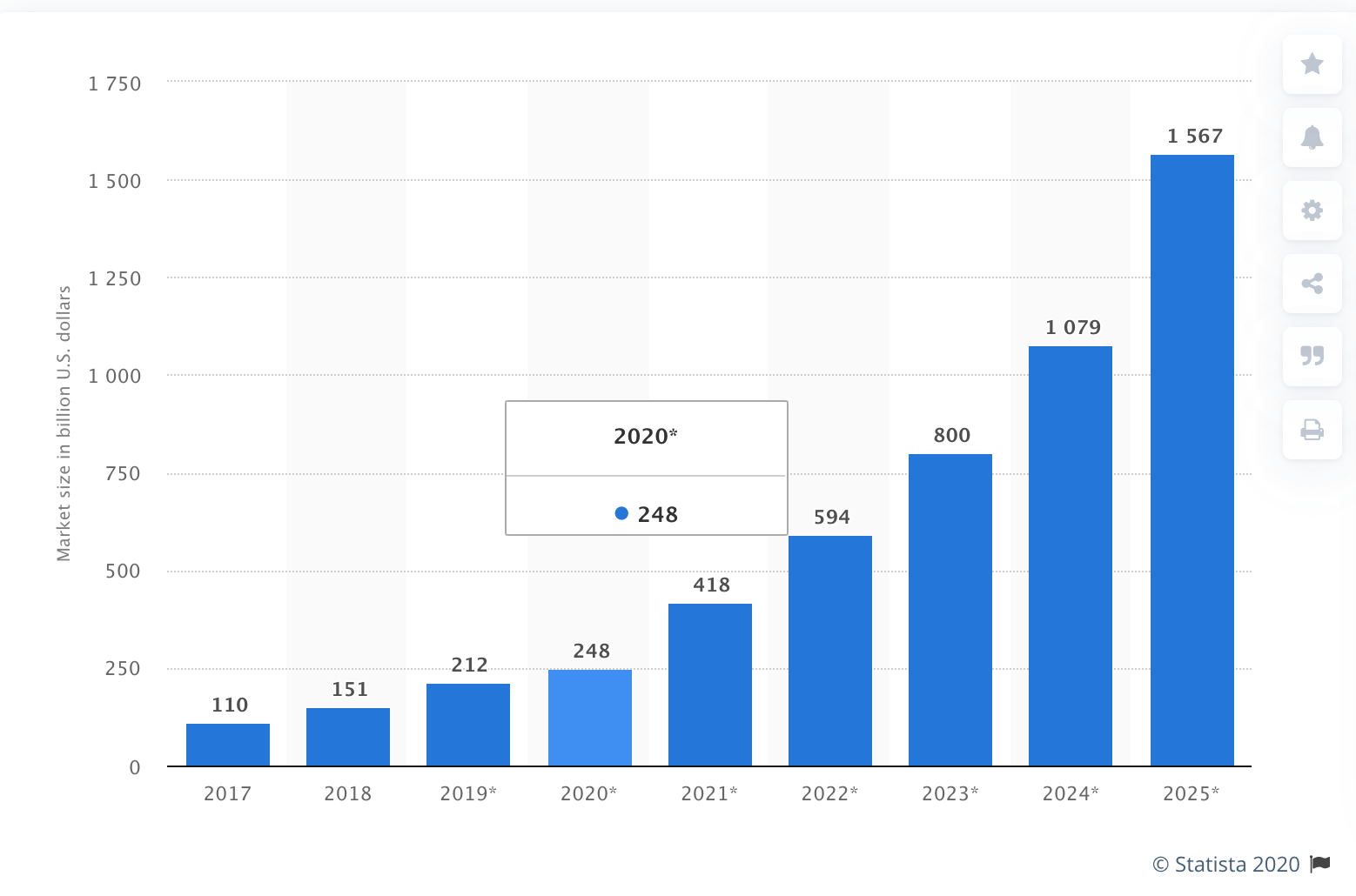
Internet of Things (IoT) connected devices installed base worldwide from 2015 to 2025
Manufacturers, of course, are largely concerned with who can create, package, and sell new devices the fastest. In this race against the competition, they are largely ignoring security issues related to data access and data management. On top of this, many are also ignoring security as it relates to the devices themselves.
In the following article, we’ll discuss some of these challenges in more detail.
Inadequate QA, Testing, and Updating
As of this writing, there are about 23 billion devices connected to the IoT around the world. By 2025, this number is expected to triple. Of course, all of these new gadgets are not created equal. In fact, in many cases, the tech companies building these devices do not perform adequate testing, provide too few updates, or fail to provide updates for their products at all.
This means that devices considered secure at the time of purchase might eventually become unsecured at some point down the line. People who are old enough may remember similar issues with early computer systems and anti-virus software. However, since IoT manufacturers are much more eager to out-produce their competitors, they will offer no updates or only issue updates until they move on to the next new product.
As if this weren’t troubling enough, IoT manufacturers are also prone to using unsupported legacy Linux kernels, leaving the customer exposed to potential attacks due to both outdated hardware and software.
In the end, the only way to solve this problem is for all IoT developers to perform proper testing and quality assurance before sending their devices to the marketplace. Even the, they need to be issuing regular updates to protect their consumers from hacking or data breaches. In the end, it only takes one large-scale breach to ruin a company completely.
Malware and Ransomware
With the number of IoT connected devices rising so fast, it should come as no surprise that the amount of malware and ransomware products designed to attack them is rising as well. Moreover, hackers are becoming increasingly innovative in how they implement their malware, sometimes limited or disabling devices while also stealing user data.
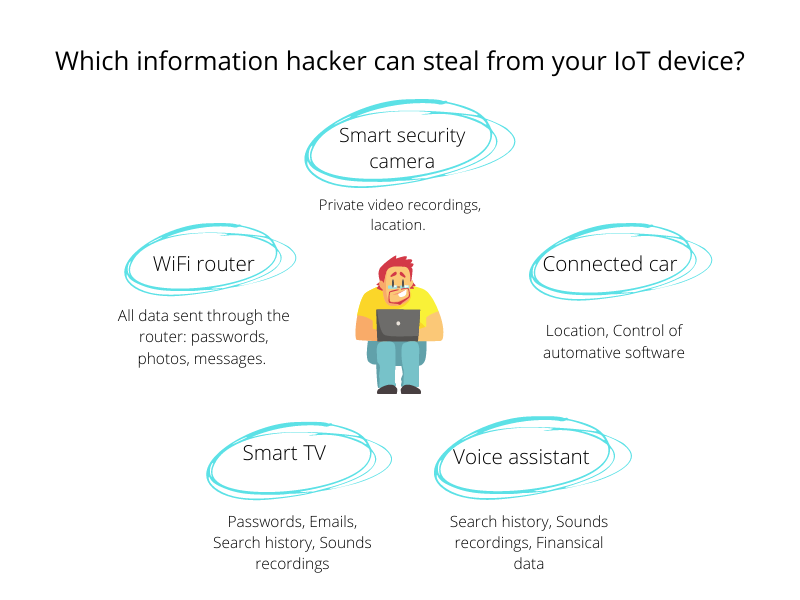
To give you an example, a simple IP camera can be used to capture a variety of sensitive information about your home or office. Once accessed, data can be funneled to an outside web address, and a ransom demanded unlocking the device and/or returning the stolen data. No doubt, attacks like this will not only become more common but also become more creative.
Cryptocurrency Botnets
The crypto boom has proved much too tempting for hackers to ignore. While blockchain is highly resistant to hacking, there is no shortage of highly-intelligent individuals trying to change that. Indeed, attacks are increasing in frequency, but not necessarily on the blockchain itself. Rather, hackers are targeting the app development that runs the blockchain.
With social engineering and other types of manipulation, scammers can get their hands on usernames, passwords, and other private information. It’s highly likely that such techniques will also be used to attack blockchain-based applications. In fact, Monero, an open-source cryptocurrency currently mined by IoT devices, and it’s far from the only one.
Already we are seeing hackers repurposing IP and video cameras in order to mine crypto. We’ll likely soon see major blockchain breaches, IoT botnet miners, and data manipulation on a large scale, which will pose a major risk to the already-volatile crypto market. To combat this, IoT apps and other blockchain-related technology will need constant regulation and monitoring.
#iot #internet of things #app development #iot development #software developent #iot security #cybersecuity
