When using Docker to run applications, security is a major concern, but it can sometimes be easy to forget as we focus first on functionality. This doesn’t need to be the case, as AWS Elastic Container Registry (ECR) can now be setup to automatically scan images on push, and provide feedback on any vulnerabilities that need to be addressed.
How Does ECR Image Scanning Work?
ECR uses the Common Vulnerabilities and Exposures (CVEs) database from the open-source Clair project. Clair performs static scanning of Docker images, meaning that it happens prior to deployment, as opposed to _dynamic scanning, _which happens at runtime.
Clair analyzes each layer of the Docker image and then returns vulnerabilities that might affect the image. These vulnerabilities are then shown to us in the AWS Console or we can fetch them via the AWS Command Line Interface (CLI).
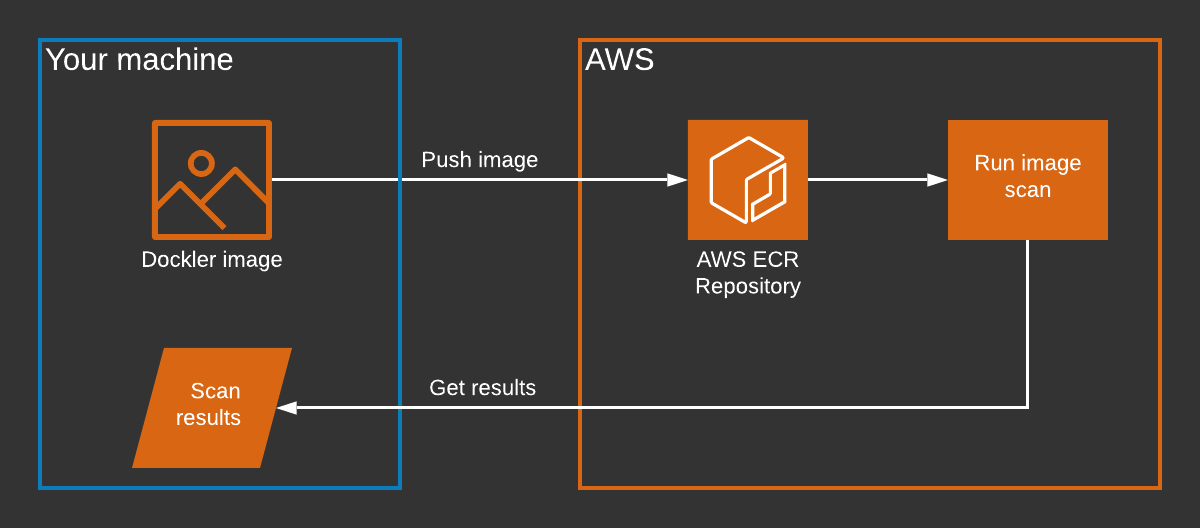
Additionally, ECR offers these features:
- Automatically scan on pushing an image to ECR.
- An event is sent to AWS EventBridge when an image scan completes, allowing for further process automation.
Scanning Images With ECR: Hands-On
Let’s start off by scanning everyone’s favorite base image, Alpine Linux. It’s a lightweight Linux distribution that is used as a base image for many popular applications in Docker. It’s also one of the official approved Docker images. ✅
At the time of writing version 3.11 of Alpine, it was not compatible with ECR image scanning, so we’ll use version 3.10.
#docker #aws #kubernetes #secuirty #ecr
