Hi everyone! 👋 If you have been following my blog then you might have already read the article on reverse engineering an Android app by writing custom smali code. I am still very much a reverse engineering beginner so after that article, I got to learn about Frida. I was told that Frida is much faster and a lot easier for scenarios where I want to snoop on functions. Well, I am glad to report that all the suggestions were absolutely correct.
In this article, I will share some details about how I was able to use it to snoop around the Nike Run Club Android app. The final goal was to extract authentication tokens that Nike generates when you log-in. This was another project on the backburner and what better way to get a project off the back burner by learning something new?

Backstory
I am an avid runner. Most of my friends and family know that. When I started this sport I got hooked to Nike Run Club. I used to diligently record each run so that I had a record for all my runs. This went on for 2 years until I found out that most of my new running friends were using Strava. I decided to move over to Strava but was pretty bummed by the lack of data export options in NRC.
There were documents online about the Nike API and they allowed you to also export your data in the JSON format but I wanted something a bit more automated. Therefore, I decided to do what any other insane person would do and started my journey of reverse-engineering the Nike Run Club APK. I decided to go to the source and figure out if I could reverse engineer the login process and generate tokens in a completely automated fashion.
This article will teach you the basic usage of Frida and how you too can go ahead and snoop around different APKs. But before we go to that part, you need to know how I ended up deciding to reverse engineer the app and not simply do a MITM attack using mitmproxy.
Intercept NRC traffic
When I started the project, I decided to snoop the traffic using mitmproxy. You can download the NRC APK from APKMirror to follow along. After downloading it, rename it to nike.apk so that the rest of the commands in this tutorial are version agnostic.
Next, you can use adb to install this APK on the emulator:
$ adb install nike.apk
Now, you need to run mitmproxy. If you struggle with setting up an emulator or the proxy, refer to this previous article of mine where I go in slightly more detail about how to do these things. I used the following command to run mitmproxy:
$ mitmproxy --set block_global=false --showhost
The last thing to do is to install mitmproxy system certificates on the Android emulator by following the official docs and point the emulator to your local mitmproxy instance.
After this setup, I opened up NRC and started checking out the requests in mitmproxy. I was kinda surprised and pretty spooked by the number of analytics requests NRC was sending. There was no SSL pinning in place so I didn’t have to do anything special before all requests started showing up. All these 68 requests were before I even signed in:

When I tried signing in, I saw this login request:
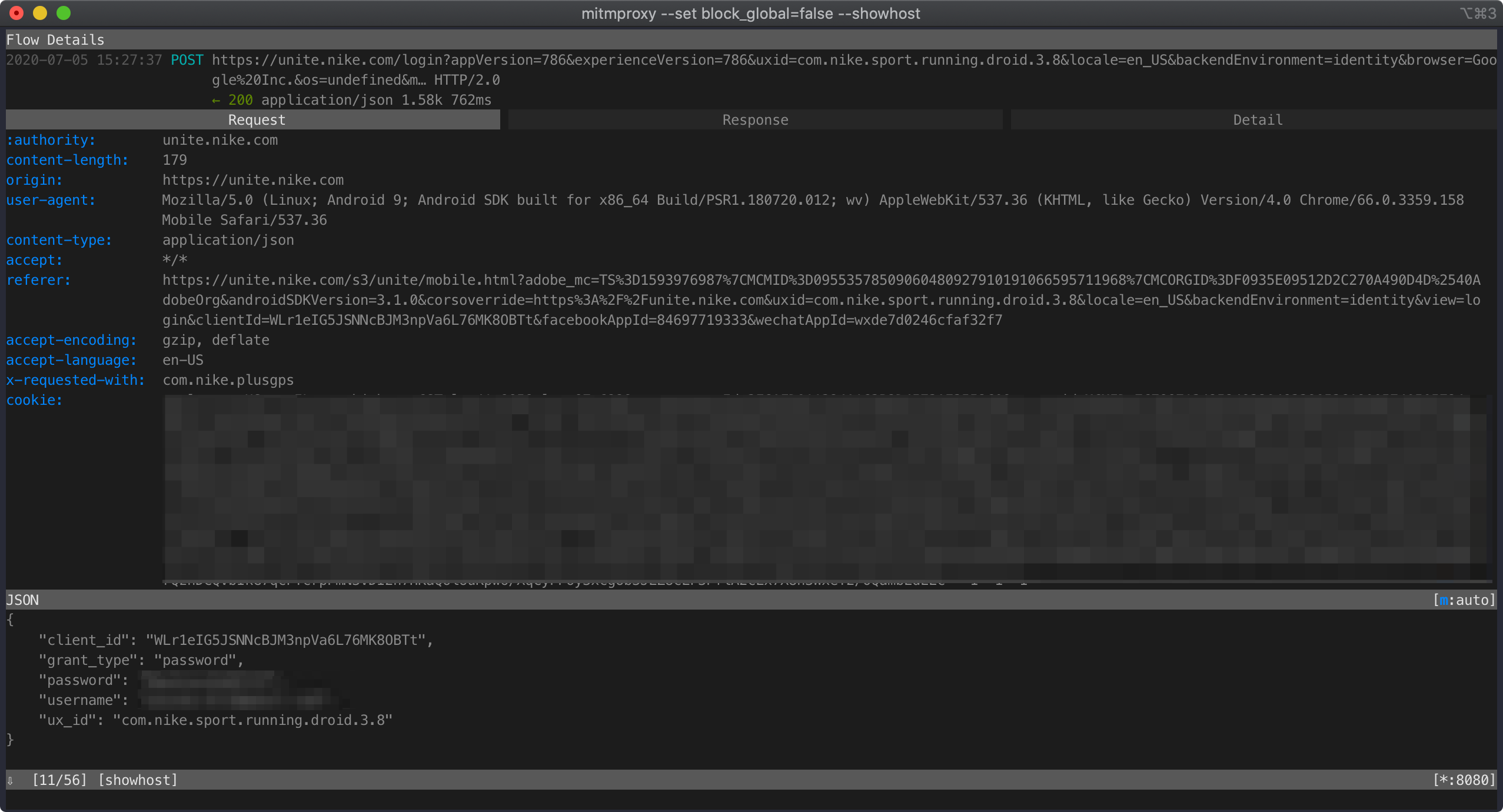
It looks like a legit login request. But what is that client_id? Everything else seems reasonable and is something we can produce on our own but the client_id seems pretty unique. Where is it coming from?
I checked out a couple of requests before and after this particular API call and couldn’t find the client_id anywhere. It had to be generated within the APK itself. I tried replaying the request a couple of times in mitmproxy and it started failing after 2-3 successful replays. I started receiving this response:
<HTML>
<HEAD>
<TITLE>Access Denied</TITLE>
</HEAD>
<BODY>
<H1>Access Denied</H1>
You don't have permission to access "http://unite.nike.com/login?" on this server.
<P>
Reference #18.2eaf3817.1593493058.26b69156
</BODY>
</HTML>
There was something dynamic in the request and I just had to figure out what. This was the perfect excuse to start snooping inside the NRC app.
By the way, the NRC app makes heavy use of HTML in their app. The login page is actually an HTML document and is loaded from the server. You can access it at this url. More about this later.
#android
