TLDR- Blog will comprise of two parts.In first part we talk about OSINT and various resources used for it in infosec and in second blog we will look into some osint challenges.
This blog is brief introduction to the OSINT. It tells what OSINT is about how to perform it .
Open-source intelligence (OSINT) is data collected from publicly available sources to be used in an intelligence context. In the intelligence community, the term “open” refers to overt, publicly available sources (as opposed to covert or clandestine sources). It is not related to open-source software or collective intelligence.
Open source intelligence (OSINT) is information collected from public sources such as those available on the Internet, although the term isn’t strictly limited to the internet, but rather means all publicly available sources.
“OS” (from OSINT) means Open Source. In this case, it is not related to the famous [open source movement][34], but to any publicly available source where the user can obtain the information in their intelligence data collection.
The key word behind OSINT concept is information, and most importantly, information that can be obtained for free. It doesn’t matter if it is located inside newspapers, blogs, web pages, tweets, social media cards, images, podcasts, or videos as long as it is public, free and legal.
With the right information in your hands, you can get a great advantage over your competition, or speed up any company/people investigation you are in charge of.
It can be simple as it is to
- Asking questions on any search engine.
- Research public forums on how to fix your computer.
- Watch a youtube video on how to make a birthday cake.
OSINT IN CYBER SECURITY
While there are a lot of OSINT techniques and mechanisms, not all of them will work for your target. First, you will have to ask yourself a couple of questions:
- What am I looking for?
- What is my main research goal?
- What or who is my target?
- How am I going to conduct my research?
Try to find the answer to these questions, and that will be the first step in your OSINT investigation.
While a lot of OSINT techniques are used by government and military agencies, they can often be applied to your own company, too. Some may work, others may not, but that’s part of the OSINT strategy — you will have to identify which sources are good and which ones are irrelevant for your research.
Let’s take a look into the most popular OSINT techniques used in cybersecurity:
- Collect employee full names, job roles, as well as the software they use.
- Review and monitor search engine information from Google, Bing, Yahoo, and others.
- Monitoring personal and corporate blogs, as well as review user activity on digital forums.
- Identify all social networks used by the target user or company.
- Review content available on social networks like Facebook, Twitter, Google Plus, or Linkedin.
- Access old cached data from Google — often reveals interesting information.
- Identify mobile phone numbers, as well as mail addresses from social networks, or Google results.
- Search for photographs and videos on common social photo sharing sites, such as Flickr, Google Photos, etc.
- Use Google Maps and other open satellite imagery sources to retrieve images of users’ geographic location.
These are some of the most popular techniques you will find. However, after you are done doing OSINT research, you will have a lot of data to analyze. That’s when you will have to refine your results, and search in detail for all the really necessary things you need, and discard the rest.
The final step in the OSINT strategy will be to translate all this digital intelligence data into a human-readable format, so it can be understood by non-technical individuals, which are often at the head of most companies.
Since whole internet is your friend in OSINT.So you are fatal and dangerous for your target.
- Suppose you want to conduct a social engineering attack against your target now you want to send a mail containing a malicious attachment to send it you planned to target one of the employees but wait you know only about the company not about its employees.Here OSINT comes into play before the internet era you would need to go the perimetre of the company headquaters and then physically verify the employees but now all you need to do is a google search on the company probably its own website reveals name of some of its employees like managers and oher team members good time to note it down in your notebook.After that lets go to the linkedin profile for the company and it contains employees section where you can see those users who have put their position in their profiles.So now you get company employees.Most of the time you will get many employees as you can from linkedin so it is best place to search for company employees.Now after going to employee profile you can get his email address to send the email.
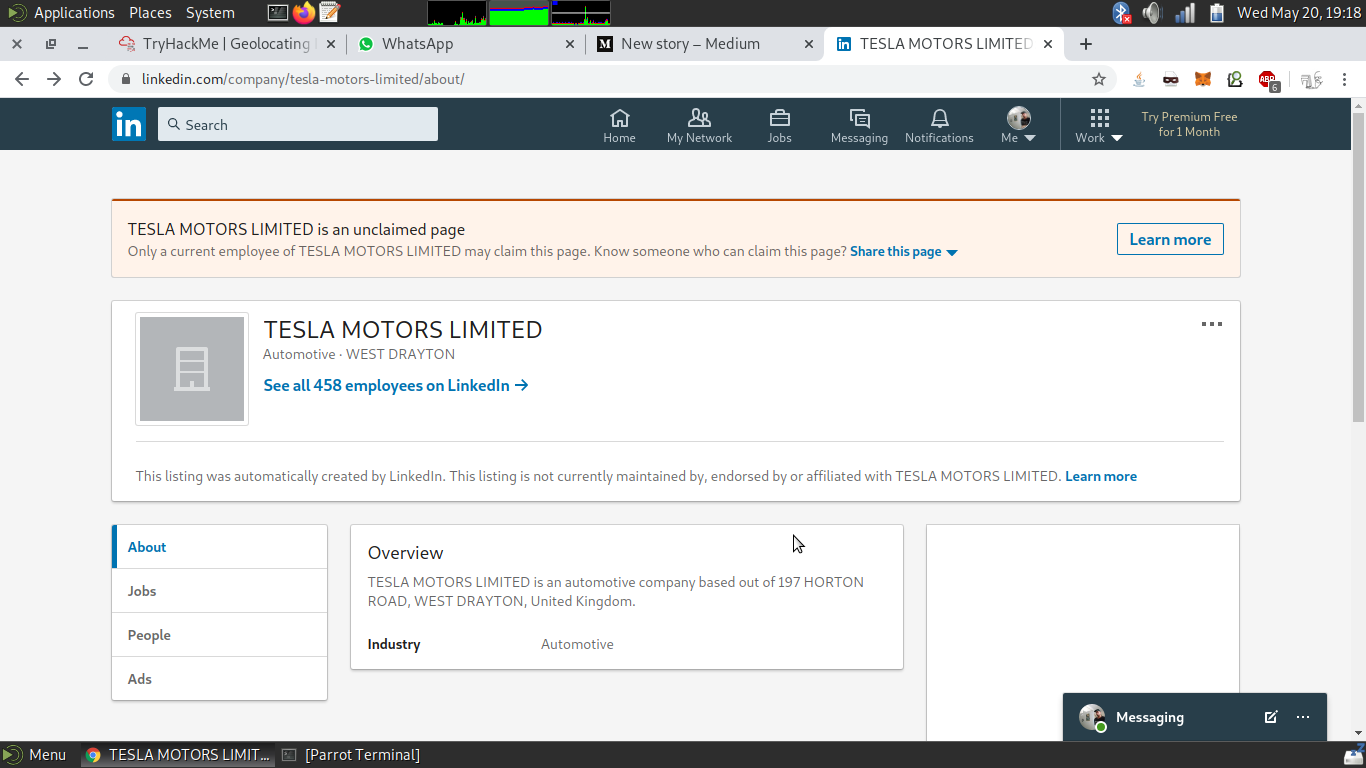
See we can see 458 employees of tesla motors.This will include engineers,managers,HR’s,CEO,CTO etc.
- Suppose you want to get into a website of your target or into CMS of your target as you can be on a bug bounty hunt then best place is to search into github and gitlab repositories because most of the code is developed using a version controlled system like Git.Remember the developers still leave many sensitive credentials in the repositories and forget to remove while making them public.This includes API keys,their credentials to access website,mysql crendentials,FTP credentials,ssh key or ssh credentials.Here github dorks comes into play
for example to look for passwords in the github repo’s of the target company
"target.com” password
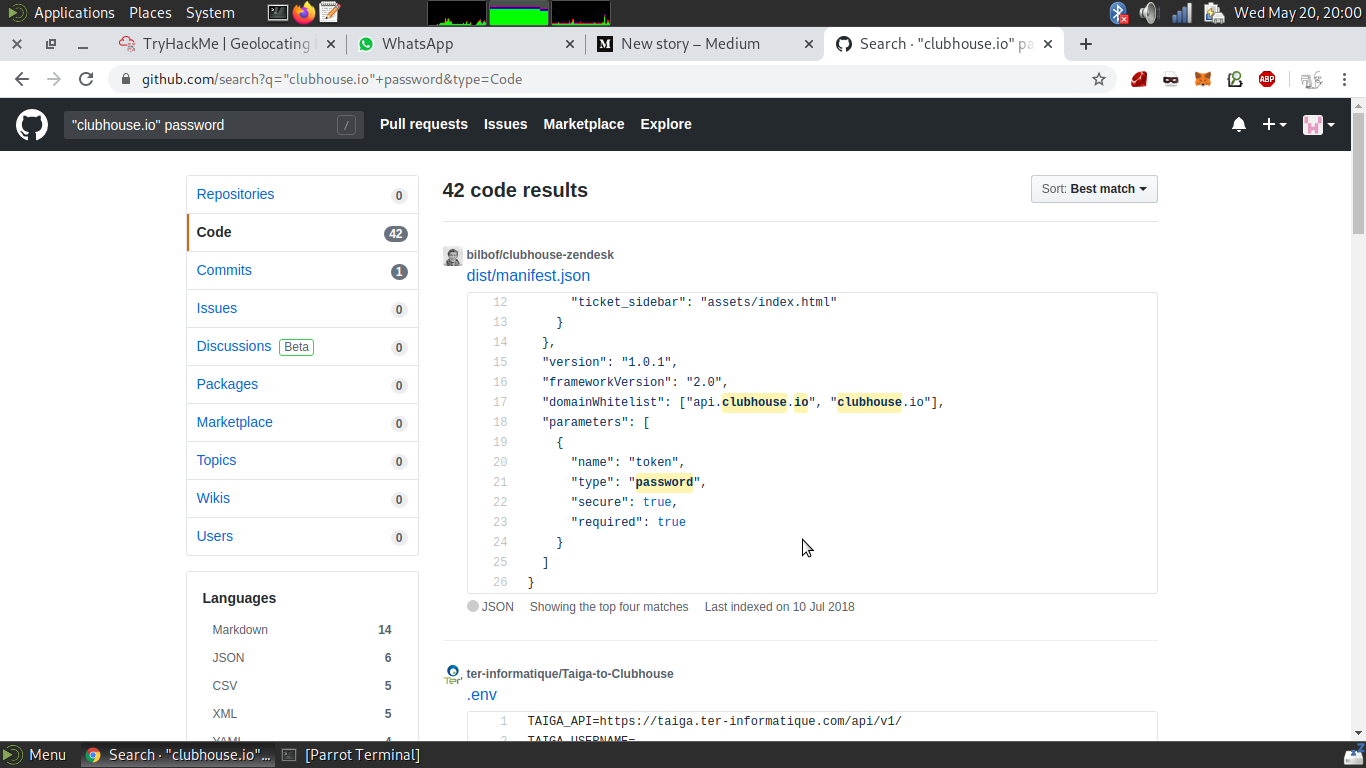
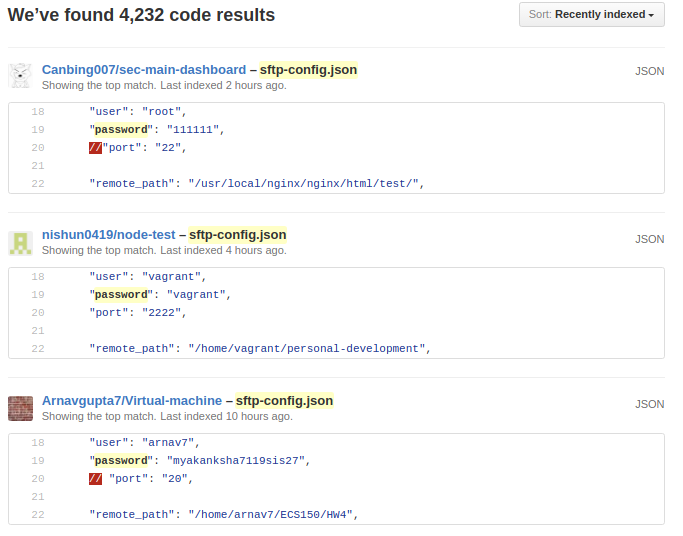
user credentials getting leaked on github
To look for ftp or sftp credentials of your target
"target.com" filename:ftpconfig
"target.com" filename:sftp-config.json password
For smtp credentials
"target.com" filename:.env MAIL_HOST=smtp.gmail.com
For mysql credential search for your target
"target.com" extension:sql mysql dump password
Here are some more dorks
filename:credentials aws_access_key_id
filename:wp-config.php
filename:id_rsa
#cybersecurity #infosec #recon #research #osint #go