SQL injection is when you insert or inject a SQL query via input data from the client to the application.
Successful attacks allow an attacker to access sensitive data from the database, modify database data, potentially shut the database down or issue other admin commands, recover the contents of files, and occasionally issue commands to the operating system.
This type of attack is relatively easy to detect and exploit, so it’s particularly important that any vulnerable systems are quickly remediated.
How Does SQL Injection Work?
SQL injection occurs when data enters a program from an untrusted source and that data is used to dynamically construct a SQL query.
Because SQL doesn’t distinguish between the control plane and the data plane, the attacker can place a meta character (a character not interpreted as data, such as an underscore _ which, in SQL, will read as a wildcard for a single character) into data input, then follow by entering SQL commands in the control plane.
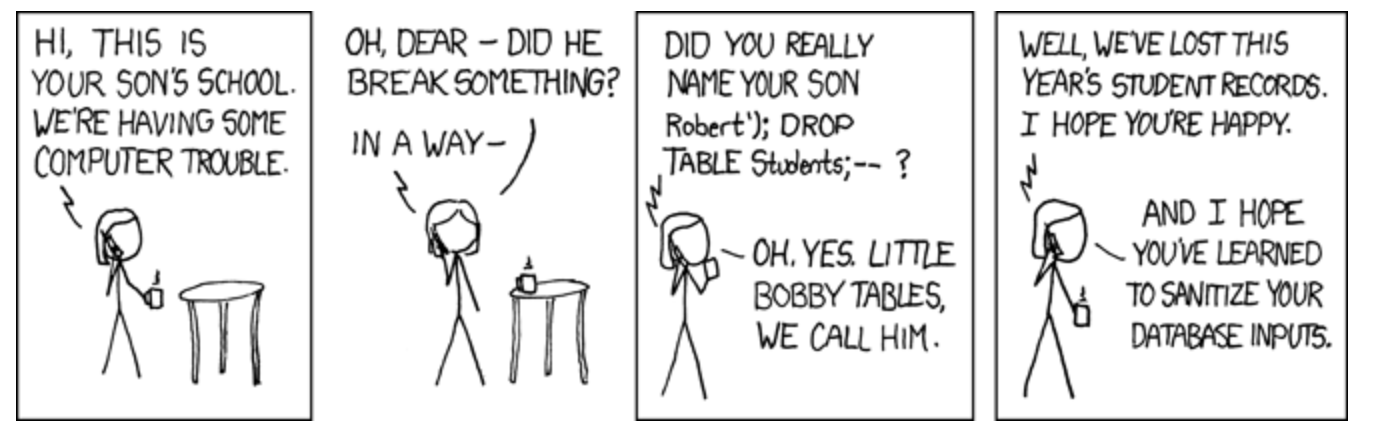
For example, in the comic below, if the string Robert'); DROP TABLE Students;–- were entered into a query which requested the studentName, then the query would become the following:
AND studentName = 'Robert';
DROP TABLE Students;
--'
The drop table command is used to delete a table and all the rows in that table, while the pair of hyphens tells most database servers that the remainder of the statement should be treated as a comment (allowing the server to ignore the trailing ’ left by the modified query).
Many database servers allow for multiple queries to be executed at once, as long as they’re separated by semicolons. If they do, this type of attack allows the attacker to execute several commands against a database (several database servers, including Oracle, do not allow this type of execution).
Preventing SQL injection is actually fairly simple - either don’t allow dynamic queries or prevent user supplied input which contains malicious SQL from affecting the logic of the query.
#sql #security #hacking #developer