Find Security Vulnerabilities when Scan Your Docker Images
How to find security vulnerabilities before it’s too late. Scan Your Docker Images for Vulnerabilities.
So you’ve crafted a Dockerfile, tested your container in your development workstation, and you’re waiting for the CI/CD to pick it up. Eventually, pre-prod is updated, integration tests passed and functional testers give the green-light. Is it now time to roll-out to prod? Not so fast.
Docker Image Layers Inheritance
Each batch of files added to an image end up creating a layer that is added to the image. Your Docker image is the concatenation of all these layers in the specific order in which they’ve originally been created.
The same principle applies when you create an image inheriting a parent image using the FROM directive in your Dockerfile. Your final image will include all the layers of your parent image, augmented with the layers you’ve created yourself.
What if you use a parent image that also uses another parent image, that may also use another parent image, that finally uses a base image like Ubuntu or Alpine? I guess you see where this is going: You end up inheriting multiple layers of content (i.e. files and executables) from upstream images that you have never seen (let alone controlled) yourself.

What if a security vulnerability is included in any of these upstream layers? We’ll look next at how to detect these. But first, what exactly is a security vulnerability?
Security Vulnerabilities
As you can see on the top-left part of the above figure (openjdk:8-jre image), there are multiple layers. On the right part, you can also visualise the files included in that image, courtesy of the Dive¹ tool. Many of those files are executables and, as with all source code we write, susceptible to security issues and vulnerabilities.
If those were files in your local filesystem you’d probably run a virus scan and, by all means, do so when feasible. In a broader sense, a virus could be regarded as a security vulnerability itself. However, a computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected areas are then said to be infected with a computer virus².
Security vulnerabilities are not viruses.
Security vulnerabilities exist in, usually, good-intended source code that has a logical or technical flaw resulting in a system weakness that can be exploited to compromise a system. Such vulnerabilities may exist undiscovered for years until someone discovers them, either while actively looking for them or by mere luck.
Vulnerability databases
The responsible thing to do when you discover a vulnerability, which could affect thousands or millions of users, is to report it. First, privately to the owner of the source code, providing enough time for a fix to be pushed out, and then publically to raise awareness for everybody else.
There are currently many well-established online vulnerability databases that can be used for such public announcements, such as CVE³, NVD⁴, and VULDB⁵.
Docker Static Vulnerability Scanning
Let’s recap on what we’ve established so far:
- A Docker image consists of layers with files and executables.
- Security vulnerabilities of executable (or library) source code are publicly held in online databases.
What if we combine those two points? Could we try to compare the executables found in our layers against the entries of an online vulnerability database to find out if our Docker image is exposed to already-known threats?
Let’s try that next.
Anchore Engine
There are many tools available, both open-source and commercial, allowing you to scan your images for known vulnerabilities. Such tools can be run as part of your CI/CD pipeline or can be connected with your images registry and scan new images as they become available. Some of these tools include Clair, Dadga, Nexus Repository Pro, Black Duck, Qualys, Harbor, and Twistlock.
For the hands-on part of this post, I’m going to show you how to use Anchore⁶. Anchore consists of a commercial edition (Anchore Enterprise) and an open-source edition (Anchor Engine).

Anchor has an impressive clientele comprising of companies like Cisco, eBay, Atlassian, Nvidia, and RedHat. The commercial edition provides you with an extra UI, RBAC, and support among others — however, it still uses the underlying, open-source edition, Anchor Engine we’re about to use here.
Installation
Anchore Engine is provided as a set of Docker images that can be run standalone or within an orchestration platform such as Kubernetes, Docker Swarm, Rancher, Amazon ECS, and other container orchestration platforms. You can quickly boot up your local version of Anchore Engine using Docker Compose and the following one-liner:
curl https://raw.githubusercontent.com/anchore/anchore-engine/master/docker-compose.yaml | docker-compose -p anchore -f - up
The above docker-compose.yaml will create five containers and then try to fetch online vulnerability databases, so it may take a few minutes to complete.
Running the client
Anchor Engine is accessed via a command-line client. You can conveniently run the CLI client via another Docker image:
docker run --rm -e ANCHORE_CLI_URL=http://anchore_engine-api_1:8228/v1/ --network anchore_default -it anchore/engine-cli
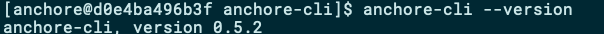
You now have a shell to the Anchore CLI client where, for now, you can execute a test command, like anchore-cli --version:
Checking-in a Docker image
Anchore Engine provides with you a vulnerabilities assessment report in two steps. You first need to add an image to be scanned and then you can request the vulnerability report for that image, allowing enough time between those two commands for the image to be downloaded and scanned.
In the following example, we will be using an old Wordpress image known to have vulnerabilities.
⚠ If you intend to use Wordpress with Docker, make sure you use a recent image instead. ⚠
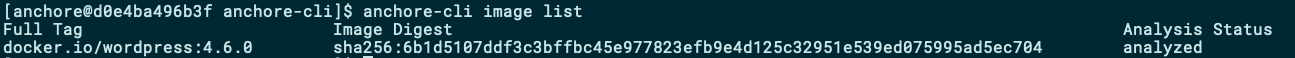
So, time to add our first Docker image with the CLI client:
anchore-cli image add wordpress:4.6.0 && anchore-cli image wait wordpress:4.6.0
With the above command, we add a new image to be analysed and wait until Anchore reports that the analysis is completed.
Viewing vulnerabilities
To see the discovered security vulnerabilities you can execute the following command:
anchore-cli image vuln wordpress:4.6.0 all
In an old image like the one we used above, we can get many, many vulnerabilities. In fact, Anchore reported 1420 known vulnerabilities for our Wordpress testing-image back from 2016:
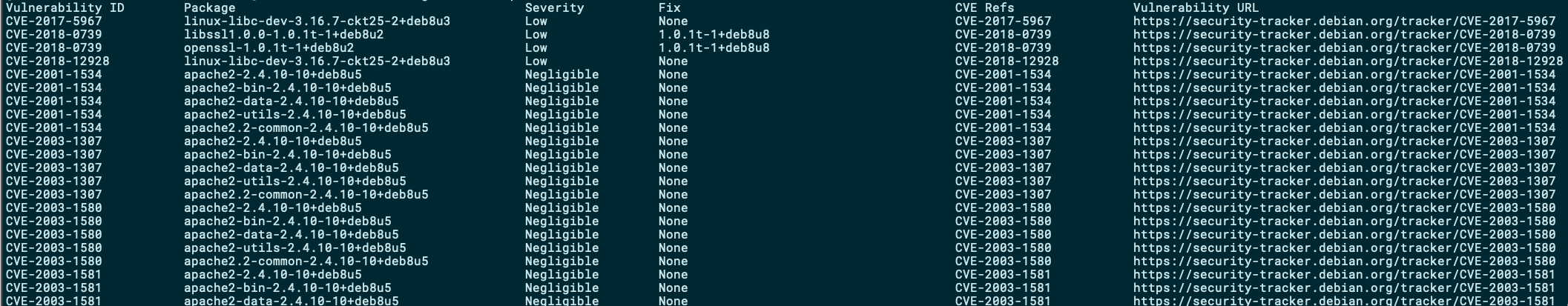
As you can see, instantiating a Docker container with the above image is an action bearing high risk. If this was an image you have created to distribute your own application with, you should probably block this release until a vulnerability assessment takes place first.
Conclusion
Software is (still) written by humans and humans make mistakes. Don’t let such mistakes haunt your Docker images. Use a Docker image security vulnerability scanner and, at least, be protected from already-discovered security issues. Integrate vulnerability scanning as part of your CI/CD pipeline and establish rules to conditionally block release roll-out when vulnerabilities are discovered.
Thank you for reading !
#Docker #Security #DevOps #Development #Programming
