One of the most significant limitations of AWS Fargate is the inability to run containers in privileged mode. This limitation means Docker-in-Docker (DinD), which enables the building and running of container images inside of containers, does not work with the AWS Fargate Custom Executor driver for GitLab Runner. The good news is that users don’t have to be blocked by this limitation and may use a cloud-native approach to build containers, effectively leveraging a seamless integration with AWS CodeBuild in the CI/CD pipeline.
We provide in-depth instructions on how to autoscale GitLab CI on AWS Fargate in GitLab Runner’s documentation. In this blog post, we explain how to instrument CI containers and source repositories to trigger AWS CodeBuild and use it to build container images.
Architecture overview
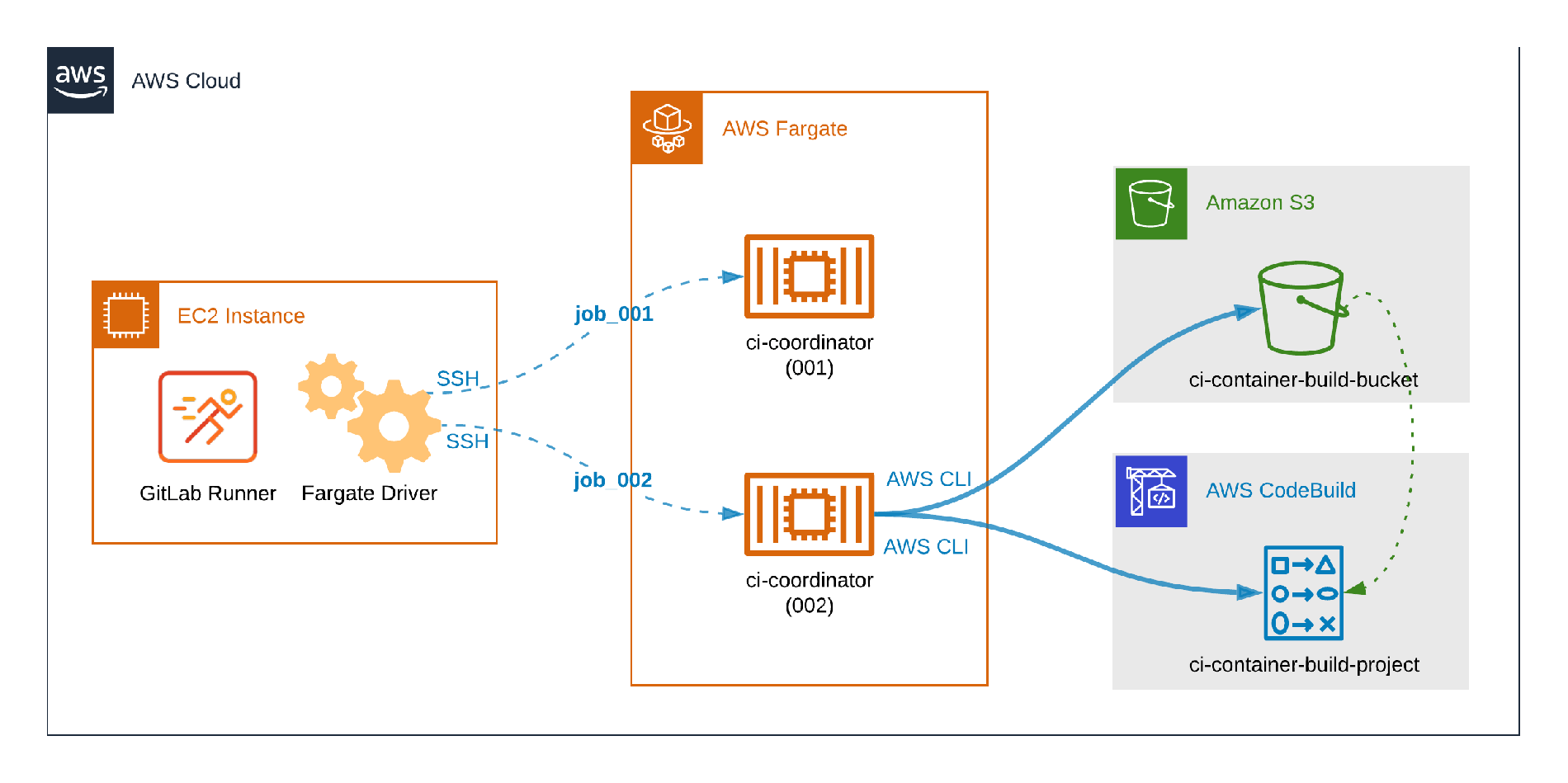 How distinct CI workloads run on Fargate.
How distinct CI workloads run on Fargate.
The picture above illustrates distinct GitLab CI workloads running on Fargate. The container identified by ci-coordinator (001) is running a typical CI job which does not build containers, so it does not require additional configuration or dependencies. The second container, ci-coordinator (002), illustrates the problem to be tackled in this post: The CI container includes the AWS CLI in order to send content to an Amazon S3 Bucket, trigger the AWS CodeBuild job, and fetch logs.
Prerequisites
Once these prerequisites are configured, you can dive into the six-step process to configure CI containers and source repositories to trigger AWS CodeBuild and use it to build container images.
- The AWS Fargate Custom Executor driver for GitLab Runner must be set-up appropriately.
- Ensure the AWS IAM user permissions include the ability to create and configure S3 and CodeBuild resources.
- AWS IAM user or service role with permissions to upload files to S3, start CodeBuild jobs, and read CloudWatch Logs.
- AWS IAM user with permissions to create and configure IAM Policies and Users.
Step 1: Create an AWS S3 bucket
- In the top menu of AWS Management Console click Services.
- In the Storage section, select
S3. - Click
Create bucket. - Choose a descriptive name (
ci-container-build-bucketwill be used as example) and select your preferred region. - Leave all other fields with default values and click
Create bucket. - In the Buckets list, click the name of the bucket you created.
- Click
Create folder. - Give it the
gitlab-runner-buildsname. - Click
Save.
Step 2: Create an AWS CodeBuild Project
- Using the AWS Console, click
Servicesin the top menu - Select
CodeBuildin the Developer Tools section - Click
Create build project - In
Project Nameenterci-container-build-project - In
Source providerselectAmazon S3 - In
Bucketselect theci-container-build-bucketcreated in step one - In S3 object key or S3 folder enter
gitlab-runner-builds/build.zip - In
Environment image, selectManaged image - For
Operating systemselect your preferred OS from the available options - For
Runtime(s), chooseStandard. - For
Image, selectaws/codebuild/standard:4.0 - For
Image version, selectAlways use the latest image for this runtime version - For
Environment typeselectLinux - Check the
Privilegedflag - For the
Service roleselectNew service roleand note the sugggestedRole name - For
Build specificationsselectUse a buildspec file - Scroll down to the bottom of the page and click “Create build project”
#aws #cloud computing #fargate custom executor