Security is one of the most important pillars for an organization. Worryingly, there has been an increase in the number of CVEs (Common Vulnerabilites and Exposures) every year, for e.g. in just last three months, there have been 5959 new security loopholes found. There is even a twitter feed to follow every new vulnerability as it is announced (not for the faint-hearted!).
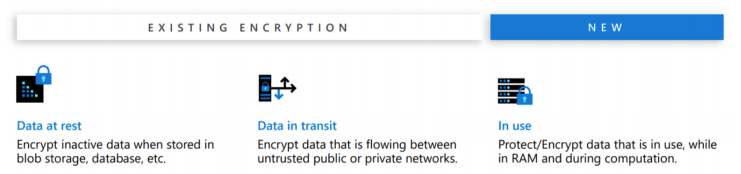
Data security — in different states
© Confidential Computing Consortium
Data is primarily in three states — at-rest, in-transit or in use. In the last years, the focus has primarily been on security of data at-rest and in-transit. Data at-rest can be encrypted at file, filesystem or disk level. Data in-transit has been more and more secure with the increased adoption of HTTPS. More and more companies are even moving towards stronger RSA encryption.
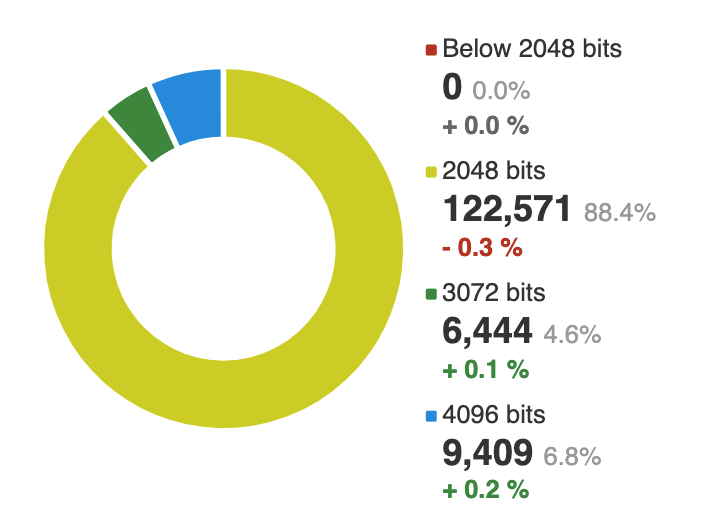
© SSL Labs — Key strength distribution comparison between July 8, 2020 and June 3, 2020
Data-in-use security however had been ignored, but has grained traction lately for multiple reasons:
- Attack vectors — As data-at-rest and in-transit have gotten more secure, the attackers have started to exploit the vulnerabilities of data-in-use, mainly using malwares / memory snooping / memory scraping. Attack vectors on the cloud include hypervisor and container breakout, firmware compromise, and insider threats.
- **Costs of data breaches **— As more and more regulations are introduced in various places (GDPR in Europe, CCPA in California etc.), there has been a monetary cost associated with data breaches, other than the loss of brand image and general embarrassment. For e.g. under GDPR, the data custodian is to pay 4% of gross annual revenue for a data breach.
- Reluctance in Cloud Adoption — Many companies have been reluctant in adopting the public cloud because of the lack of security while data-in-use or because the regulation prohibits it or unauthorized access to their code (intellectual property) or the fear of data compromise etc.
The problem of data-in-use security is what is primarily confronted in Confidential computing. So let’s dive in.
Confidential Computing
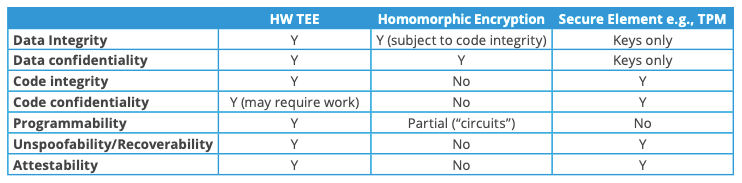
Confidential computing aims to protect your code and data from being compromised. Confidential computing is achieved using hardware-based Trusted Execution Environments (TEE), also known as **Enclaves, **however there are other ways of data protection called Homomorphic encryption and Trusted Platform Modules (TPM).
© Confidential Computing Consortium
Important: It’s important to clear up what confidentiality and integration stand for here. Confidentiality stands for prevention of any unauthorized view, whereas Integrity stands for prevention or detection of any unauthorized change.
Confidential computing requires a mix of software and hardware where hardware normally serves as the root of trust for security purposes.
Enclaves / TEE
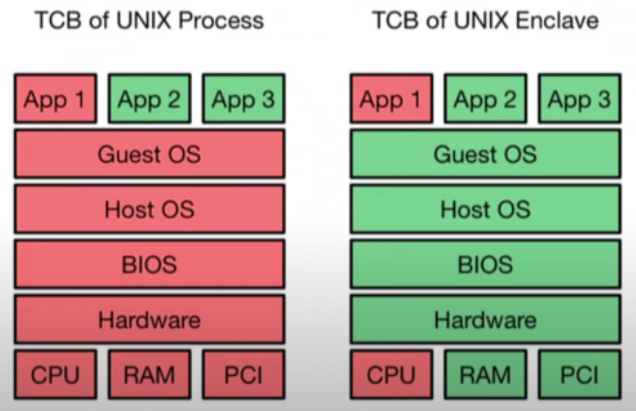
The basic idea in confidential computing is to reduce your attack surface area, for e.g. on traditional systems, if some attacker is able to get root access to your machine where you keep your keys, not much can be done to stop this attack. However if you run an application in an Enclave (TEE), the application can run protected from even the OS kernel, with the guarantee that even a user running with root privileges cannot extract the Enclave’s secrets or compromise its integrity.

#confidential-vms #security #confidential-computing #cloud #cloud-computing #cloud
