In the past month, I had a chance to implement JWT auth for a side project. I have previously worked with JWT in Ruby on Rails, but this was my first time in Spring.
In this post, I will try to explain what I have learned and applied in my project to share my experience and hopefully help some people.
We will start by taking a quick look at the theory behind JWT and how it works. Then we will look at how to implement it in a Spring Boot application.
JWT Basics
JWT, or JSON Web Tokens (RFC 7519), is a standard that is mostly used for securing REST APIs. Despite being a relatively new technology, it is gaining rapid popularity.
In the JWT auth process, the front end (client) firstly sends some credentials to authenticate itself (username and password in our case, since we’re working on a web application).
The server (the Spring app in our case) then checks those credentials, and if they are valid, it generates a JWT and returns it.
After this step client has to provide this token in the request’s Authorization header in the “Bearer TOKEN” form. The back end will check the validity of this token and authorize or reject requests. The token may also store user roles and authorize the requests based on the given authorities.

Implementation
Now let’s see how we can implement the JWT login and save mechanism in a real Spring application.
Dependencies
You can see the list of Maven dependencies that our example code uses below. Note that the core dependencies like Spring Boot and Hibernate are not included in this screenshot.
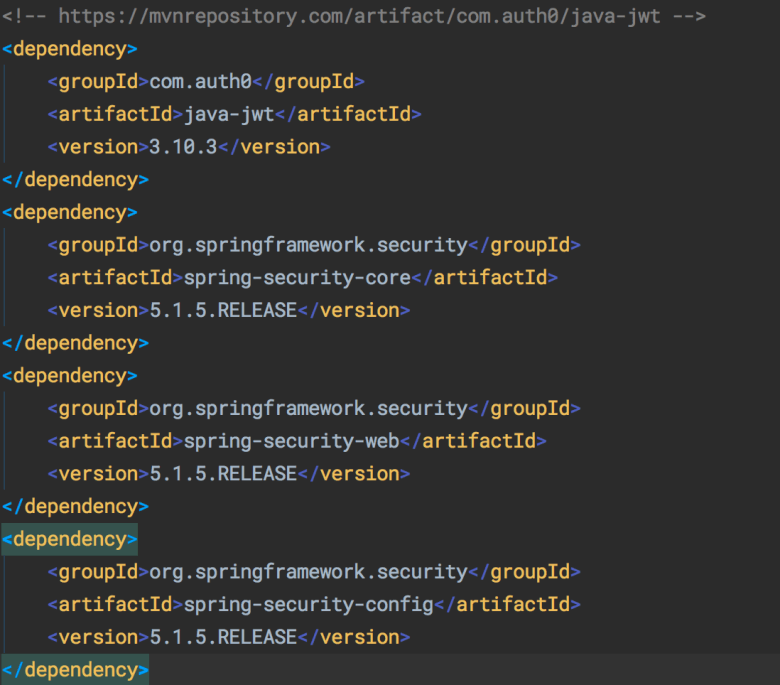
Saving Users
We will start by creating controllers to save users securely and authenticate them based on username and password.
We have a model entity called User. It is a simple entity class that maps to the USER table. You can use whatever properties you need depending on your application.

We also have a simple UserRepository class to save users. We need to override the findByUsername method since we will use it in authentication.
public interface UserRepository extends JpaRepository<User, String>{ User findByUsername(String username); }
We should never store plaintext passwords in the database because many users tend to use the same password for multiple sites.
There are many different hashing algorithms, but the most commonly used one is BCrypt and it is a recommended method of secure hashing. You can check out this article for more information on the topic.
@Bean public BCryptPasswordEncoder bCryptPasswordEncoder() { return new BCryptPasswordEncoder(); }
To hash the password, we will define a BCrypt bean in @SpringBootApplication and annotate the main class as follows:
We will call the methods on this bean when we need to hash a password.
We also need a UserController to save users. We create the controller, annotate it with @RestController, and define the corresponding mapping.
In our application, we save the user based on a DTO object that is passed from the front end. You can also pass a User object in @RequestBody.
After we pass the DTO object, we encrypt the password field using the BCrypt bean we created earlier. You could also do this in the controller, but it is a better practice to put this logic in the service class.
@Transactional(rollbackFor = Exception.class)
public String saveDto(UserDto userDto) { userDto.setPassword(bCryptPasswordEncoder.encode(userDto.getPassword()));
return save(new User(userDto)).getId();
}
#jwt #spring-boot #security #api #developer
