Exploiting System Level Vulnerability
Operating System vulnerabilities are very common and are at large especially Microsoft Windows. These vulnerabilities are exploited in different ways which can give system-level access to the adversaries trying to break into the system. One such vulnerability is going to be discussed in this article. As a proof of concept, I would be exploiting a very famous vulnerability found in Microsoft Windows which is known as Eternal Blue. The machine I am going to exploit is available on the TryHackMe Platform. So with any further ado lets start
Objective
Exploiting a very popular Microsoft Windows Vulnerability to gain system-level access and escalate privileges.
Learning Outcomes
Exploiting the host machine under consideration will enable the audience to :
- To gain a shell of the compromised system in a number of ways
- Migrating the process IDs in order to get the higher privileged processes
- Cracking hashes in order to gain access to different user accounts present on the system of the compromise resulting in gaining access to different flags on the system
1.Reconnaissance Phase
Let us first gather information about the system of compromise. The most common tool used to gather information regarding the open ports and services is Nmap. So let’s scan our host machine using Nmap with the following flags set.
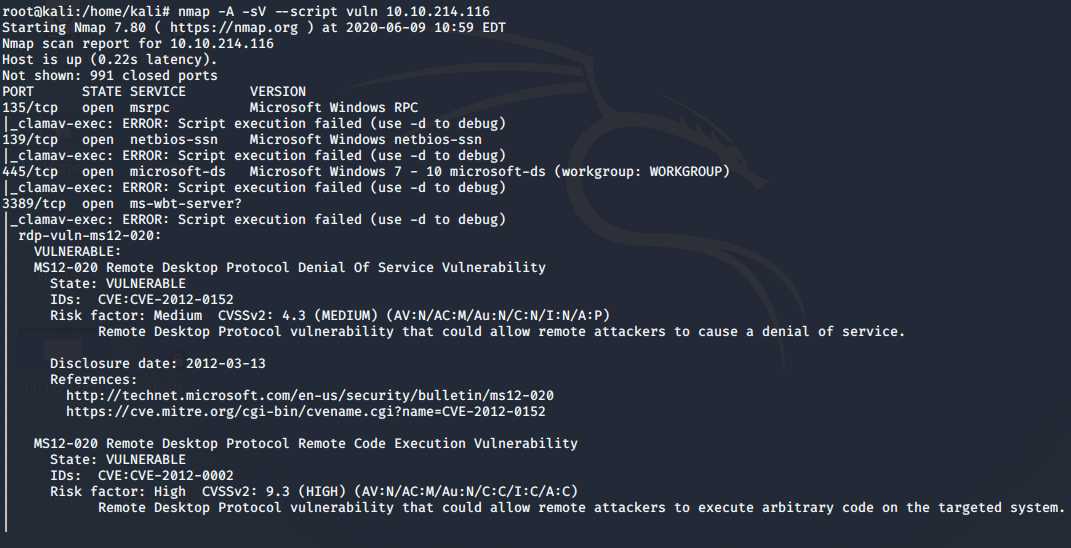
OK, so we get the number of ports that are open and the services that are running against these ports. This answers our task 2.This information helps in identifying service level vulnerabilities. Notice we also included the script vuln that acts as a vulnerability scanner and tells us about the vulnerabilities it finds. In our case, its MS17–010 also known as Eternal Blue, this vulnerability is marked with the risk level of critical so we are going to exploit this. This gives us the answer to task 3
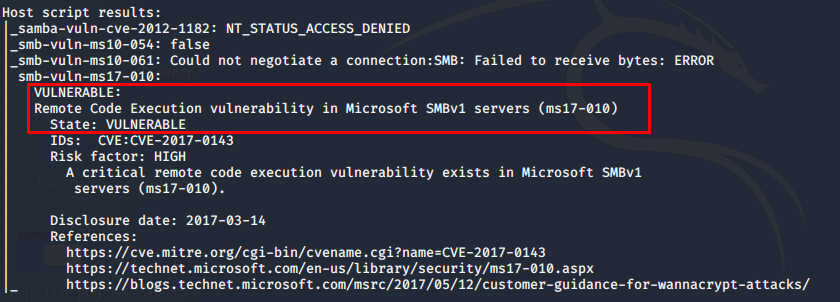
System Vulnerable to Eternal Blue
2.Gaining Access
Now that we know the vulnerability its time to exploit it. For exploitation, we are going to use Metasploit which contains a large number of exploits and post exploits which can be run against target systems. So fire-up Metasploit by typing msfconsole in the terminal and search for the exploit that corresponds to Eternal blue (MS17–010)
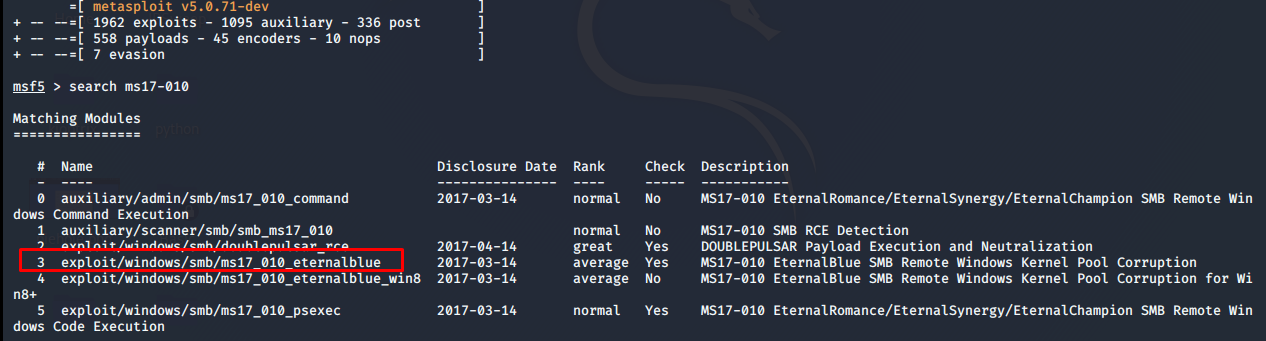
Now that we know which exploit to use, let’s run this exploit. Type show options in order to know which parameter is required as a prerequisite to run the exploit as seen below. Once the exploit and the parameters are set, run the exploit as shown below
#ethical-hacking #eternalblue #security-vulnerabilities #walkthrough #pentesting