Introduction
Welcome to my second article here on Medium. Today we will be looking at Bastion from HackTheBox. This is a rather realistic box in my opinion and it made a lot of fun. This article will be similiar to my first article, because I will provide some more information on the Box and why it is vulnerable. However, the following articles will not give as much information on the different tools that I will be using. You can look this up in my first article of the series. You can find cheat sheets and helpful information on the tools that Kali has to offer. This will save some time. So let’s get right into it:
Setup
Before we start, a few words to my setup:
- Kali Linux on a VM
- Tilix: A tiling terminal emulator for Linux
- Cherry Tree for note keeping, I would highly recommend the template from James Hall
Enumeration
Today we will be looking at Bastion from HackTheBox, so get your VPN up and running.
First, let’s start with enumeration in order to gain as much information about the machine as possible. The first step is using nmap. My methodology with nmap looks like this:
nmap -A -oA nmap 10.10.10.134
This scan setup runs very fast and shows important results. We can look at our scan with this command:
less nmap.nmap
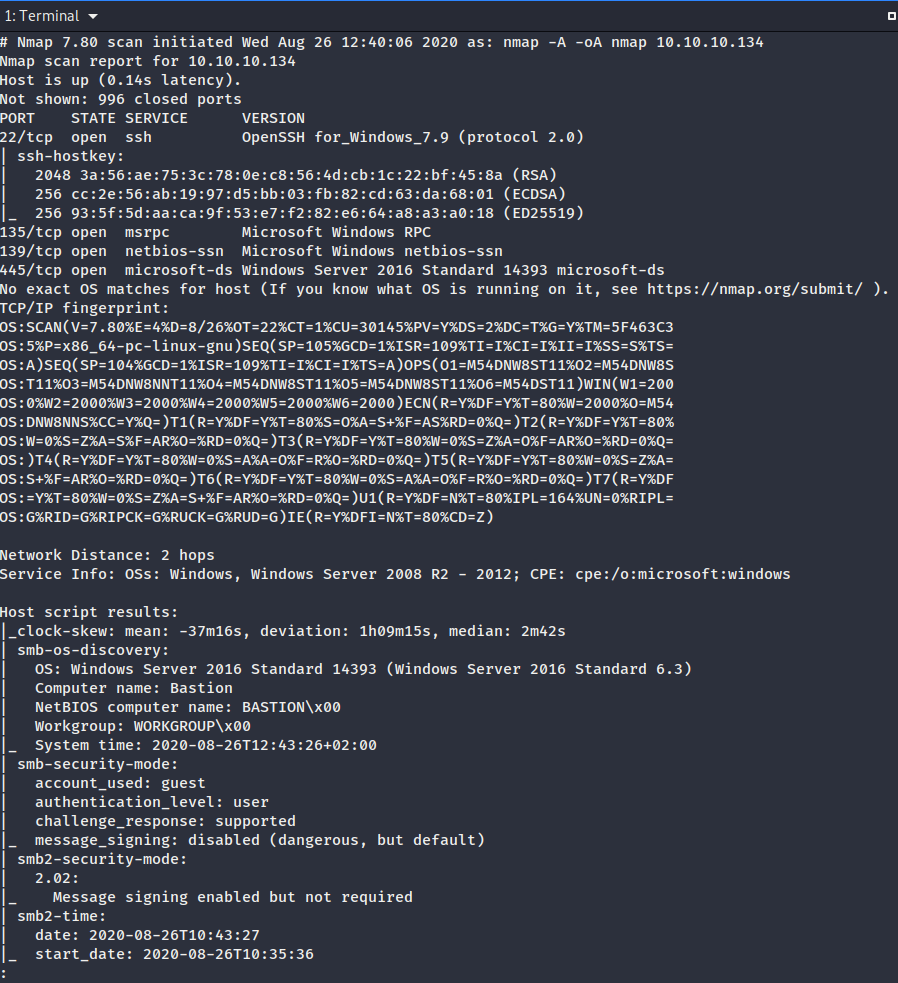
Nmap port scan
Findings
There are some interesting findings to be written down in Cherry Tree, which would also be documented in a pentest report:
- Port 22 is open which is ssh. The system uses OpenSSH for windows. Mostly Unix systems use OpenSSH and not Windows systems.
- Remote Procedure Call on port 135
- SMB on ports 139 (NetBios) and port 445
- There are no webservers running, which is odd
- Nmap gives us some more information on the system: It’s a Windows server 2016 and the computer name is Bastion
I would take a closer look at SMB. Sometimes there is anonymous access on SMB, however there is almost always some kind of authentication on OpenSSH.
The name of the computer seems very suspicious. If you do not know: A bastion is part of a fortification, e.g. a castle. It’s main purpose is to protect the castle against attackers. This technique is also being used in IT. A bastion host is a computer on a network specifically designed and configured to withstand attacks. The computer generally hosts a single application, for example a proxy server, and all other services are removed or limited to reduce the threat to the computer.
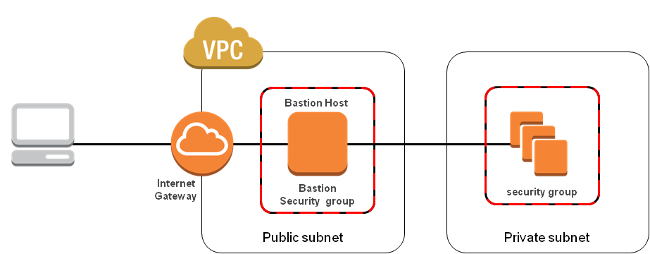
Bastion host
There is a really good article on this topic by Henrik Sylvester Pedersen in which he explains that there really isn’t a necessity for a bastion host.
#pentesting #security #kali-linux #hacking #hackthebox
