The three fundamental roles of identity and access management systems are identification, authentication, and authorization. In other words, IAM allows the appropriate personnel to execute tasks using devices, hardware, software applications, or any other IT technology.
**
Why Do We Need Identity and Access Management?**
It reduces security risk: Identity and access management systems can be used to detect unauthorised access privileges, validations, and policy breaches in a single system. You can also make sure your company complies with all regulatory and audit standards.
-
It minimizes IT costs: IAM can help you save a lot of money on your operations. Organizations can, for example, use federated identity to incorporate third-party services into their systems. Similarly, cloud IAM eliminates the need to purchase and manage on-premise infrastructure.
-
It enhances the user experience: Users no longer have to remember and input several passwords thanks to SSO. Gone are the days when you had to memorize hundreds of different password combinations. When customers use SSO, they can experience automatic logins whenever they switch to a new connected device.
-
It helps to improve security profiles: SSO is used in modern IAM systems, with additional levels of security. The bulk of these systems employ Security Assertion Markup Language (SAML) 2.0, which may authenticate and authorize users depending on their directory profiles’ access levels.
How IAM Solution Can Accommodate Your Enterprise Requirements
The broad experience of LoginRadius in the identity and access management sector will assist you in developing the best process for your company.
The following solutions are available from IAM providers to assist you in creating safe, seamless experiences for your customers and employees.
-
Single Sign On: LoginRadius SSO gives your users a single identity that they can use to access all of your web assets, mobile apps, and third-party services.
You can recognise your users as they move from one site to the next, and you can keep track of their activities in a central profile. -
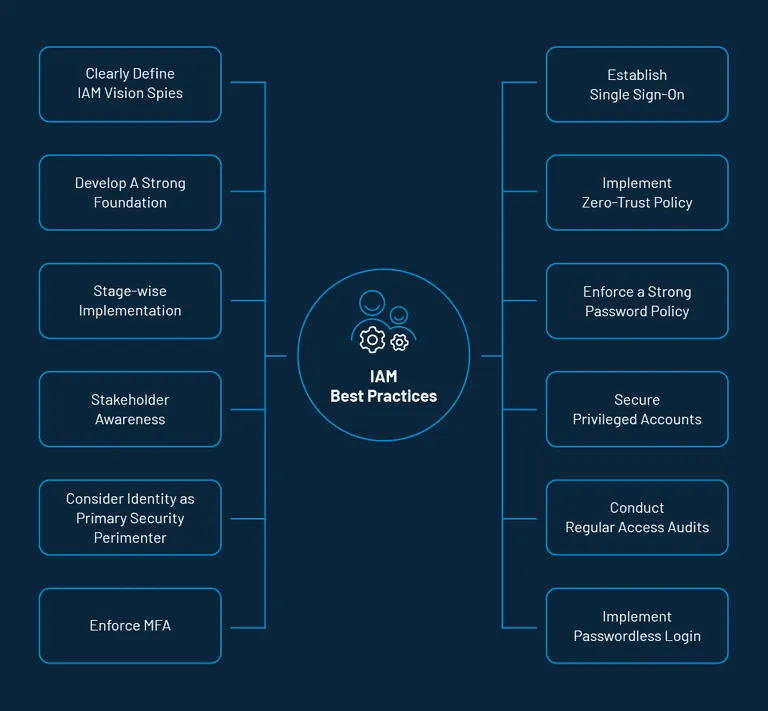
Multi-factor authentication (MFA): It adds additional layers of security to the authentication process, allowing it to verify identities. MFA ensures that the proper consumer gets access to your network by requiring at least an extra step to validate identities. It relieves users of the stress of forgotten or stolen passwords and makes it more difficult for fraudsters to gain access to their accounts.
-
Federated SSO: Federated SSO allows users to access web apps from many organizations using one digital identity.
Standard SSO protocols such as SAML, JWT, OAuth 2.0, OpenID Connect (OIDC), and Web Services Federation are supported by LoginRadius. The IAM platform provides a single dashboard for managing all of the protocols’ configurations.
Your IAM should be a blend of cutting-edge technology and business processes. You must first comprehend your present IT and network architecture before planning your future capabilities.
Regardless of where they operate, enterprises may reap significant time-saving, efficiency-building, and security-enhancing benefits from the proper IAM provider. The broad experience of LoginRadius in the identity and access management sector will assist you in developing the best process for your company.
#identity #access #management #iam #solutions