In this story, I share with you the research and defense solution against the LibSSH authentication bypass vulnerability, on the year of discovery, as I’ve developed during an Information Security workshop at Tel-Aviv University.
The solution enables the firewall not only to block this attack but also to inspect the content of the SSH communication.
The full code of the firewall is available at the end of this story.

What is the LibSSH Authentication Bypass vulnerability?
This vulnerability is found in libssh library, which provides a simple API for SSHv2 protocol, prior to versions 0.7.6 and 0.8.4.
SSH is a protocol for secure remote login usually into Unix-like OSs, in an encrypted manner.
The attacker would create channels, **without **performing authentication which results in unauthorized access.
How would the attacker trick the libssh library to grant access? Simply by sending a message that, according to the protocol, is sent **after **the server replies with authentication success.
This malicious message would then trick the server’s state machine to belive that attacker has a valid channel.
Let’s delve into the details!
During the normal authentication process, client sends the server a message with its username and password (SSH2_MSG_USERAUTH_REQUEST), the server then inspects the request with the userauth_pubkey function and checks for the username existence and validity of password and replies with either success (SSH2_MSG_USERAUTH_SUCCESS) or failure (SSH2_MSG_USERAUTH_FAILURE) message.
An attacker would first scan for vulnerable devices on which a libssh with unpached version is installed and target them with malicious message.
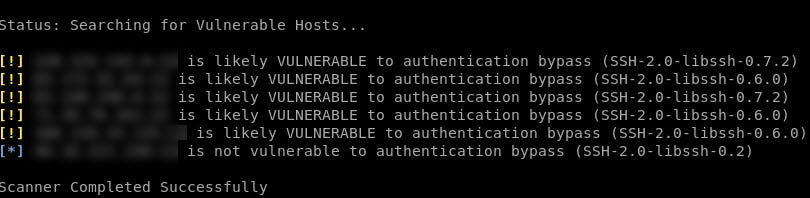
LibSSH vulnerability scanning with Leap Security scanner tool, photo taken from leapsecurity.
After finding a vulnerable device with a matching version, the attacker (client) simply skips the authentication stage described above by sending a message (SSH2_MSG_USERAUTH_SUCCESS) that bypasses all checks.
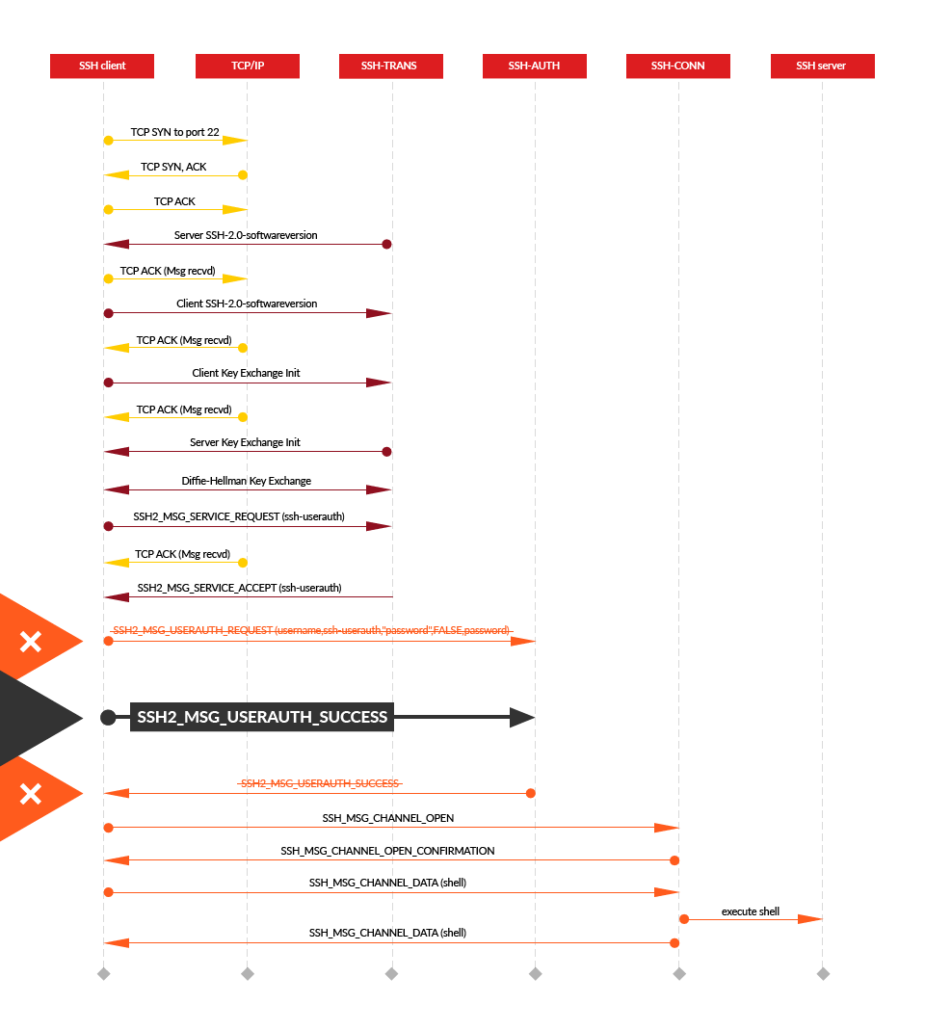
The LibSSH Authentication bypass attack, photo taken from guardicore.
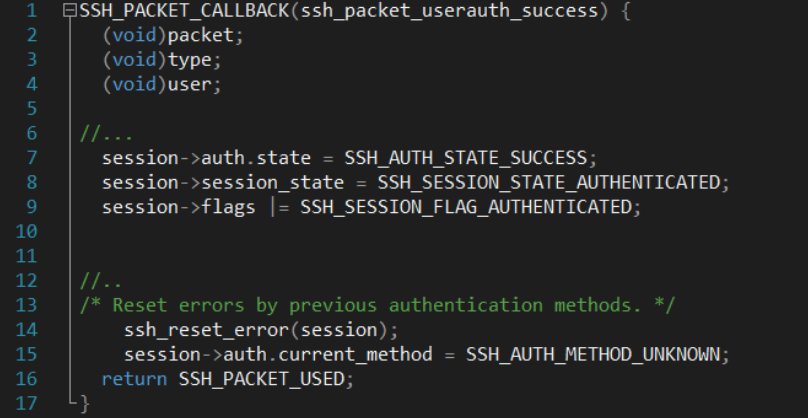
When the SSH2_MSG_USERAUTH_SUCCESS arrives, the SSH_PACKET_CALLBACKcallback is triggered, server session marked as authenticated.
#programming #ssh #security #cybersecurity #firewall
