Introduction
This is a real case study of how to enumerate and use IAM permissions to your advantage. I strongly suggest you read my previous article on how IAM permissions work. It’s long, but necessary to understand most of the things we did here. Another thing I want to clarify, this exploitation was long and somewhat technical, so I wont go too deep on the easier vulnerabilities we found (one of them is also covered in a previous writeup). We’ll cover manually enumerating IAM policies and roles, as well as automated tools that can do it for you (and why you shouldn’t trust them 100% of the time). We’ll also get a crash course on jq.
Getting a foot inside the network
A Nessus scan of a public AWS endpoint showed a Hadoop instance with an exposed unauthenticated ResourceManager service. You might remember this vulnerability from my previous writeup on Hadoop and MCollective exploitation. You can easily exploit this with metasploit to achieve RCE.
After compromising this instance and quickly setting up a couple of backdoors to re-gain access in case the service went down, we started scanning the network, and found a master Hadoop node with an exposed service on port 9290 on an internal interface (10.0.0.0/8).
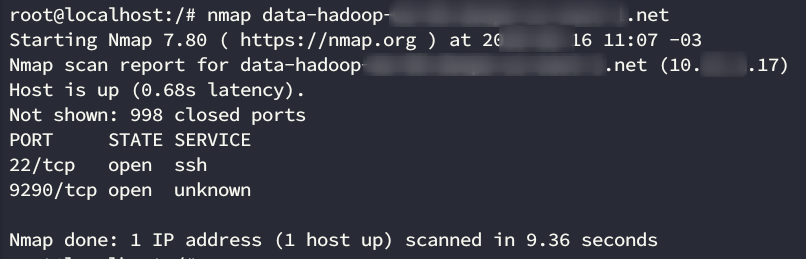
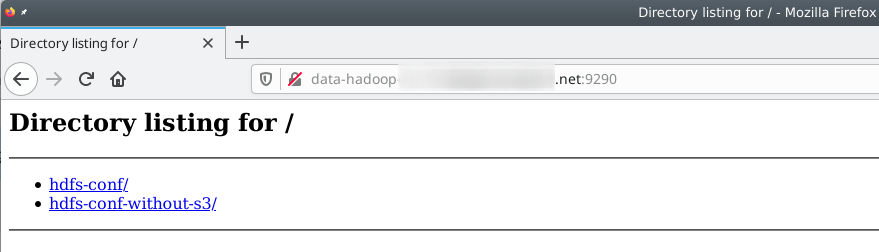
We verified that it hosted configuration files for Hadoop.
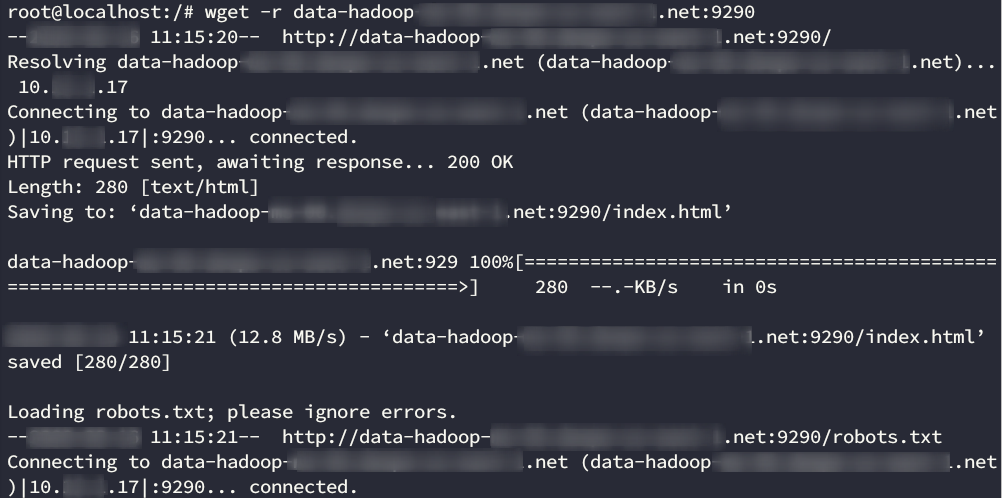
We proceeded to download all the information to analyze it.
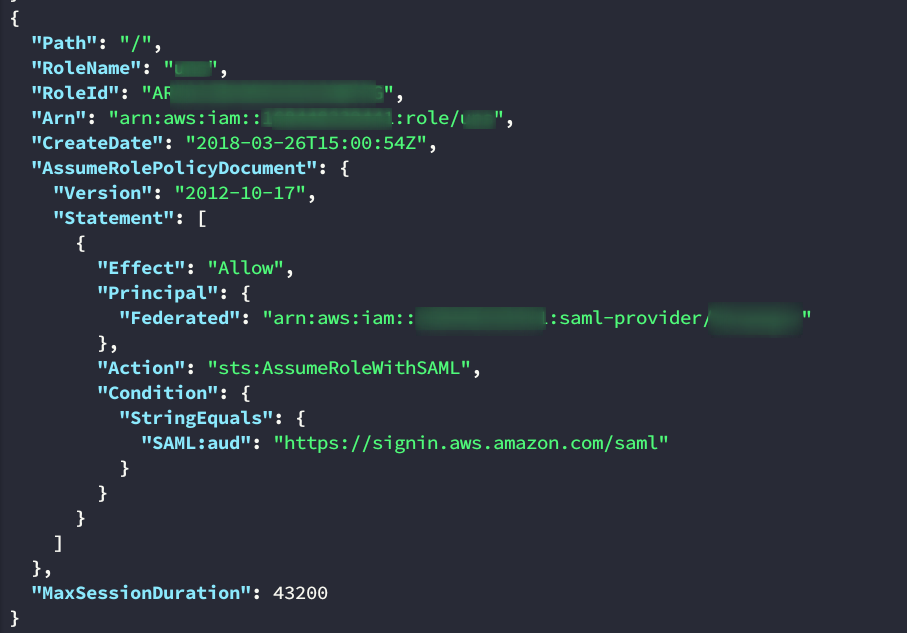
When you’re working on AWS environments, one of the best things you can find are AWS access keys and secret keys. You can find the relevant regex’s here: https://gist.github.com/hsuh/88360eeadb0e8f7136c37fd46a62ee10
#devops #infosec #red-team #security #pentesting