Hey hackers!!!
We have already discussed about basic commands on Nmap and also the cheat sheet for Nmap, which i believe helped you for performing scans on networks , today we are going to discuss about some more Nmap commands ,such as Stealth scan , OS detection , Zombie scan, Bypassing Firewall Commands and many more.
TCP Connect Scan
First scan we will look is TCP scan , this scan is often considered the most basic and stable of all the port scans because it actually completes the three way handshake and then tears down the connection gracefully.
nmap -sT 192.168.1.3
However, we have discussed this command prior , but for better understanding i have also made use of Wireshark to record the behavior of the packets.


You can see from above wireshark output that it actually completed Three Way handshake.
TCP SYN Scan
The SYN scan is arguably the most popular Nmap port scan.As is the the default Nmap scanning technique i.e even if you don’t specify the “-s” switch, Nmap will use the SYN scan by default.
SYN scan is faster than TCP scan .
nmap -sS 192.168.1.3
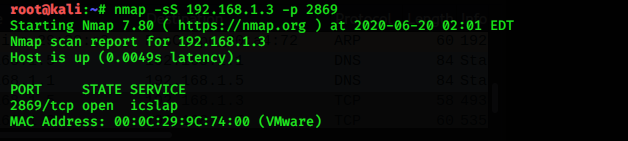
As you can se that i have also made use of “-p” switch which allows you to scan a specific port.(2869 in this case , which is intentionally left open).
Below is the wireshark output for the same.
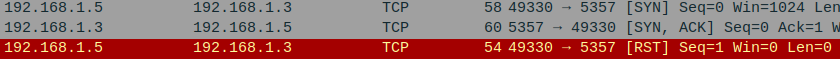
NULL ,FIN and XMAS Scan
NULL,FIN and XMAS scans are similar to each other .The major advantage of using these scans for pentest is that many times they get pass through firewall and IDS and can be really beneficial against Unix-based OS as all three of these scans do not work against Windows OS.
NULL Scan
A NULL scan is accomplished by sending no flags inside the TCP header .If no response comes, it means that the port is open ,if RST packet is received, it means that the port is closed or filtered.
To perform NULL scan type below command :
nmap -sN 192.168.1.3
FIN Scan
A FIN flag is used to close a currently open session.In a FIN scan the sender sends a FIN flag to the target machine.If no response comes from the target machine , it means that the port is open ,if the target responds with RST packet , it means that the port is closed.
To perform FIN scan type below command:
nmap -sF 192.168.1.3
#ethical-hacking #cybersecurity #nmap #network-security