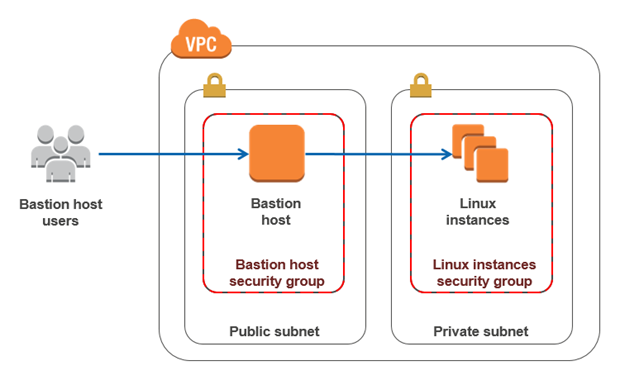
What is a Bastion Host?
_A bastion host _ is a server whose purpose is to provide access to a private network from an external network, such as the Internet. Because of its exposure to potential attack, a bastion host must minimize the chances of penetration.
Including bastion hosts in your VPC environment enables you to securely connect to your Linux instances without exposing your environment to the Internet. After you set up your bastion hosts, you can access the other instances in your VPC through Secure Shell (SSH) connections on Linux.
In my previous article, I launch WordPress in the public subnet and MySQL private subnet in AWS using Terraform. Read Article here.
My previous setup(article) has the following drawbacks.
1.MySql instances can not accessible by admin via ssh.
2.MySql instances can not go to Internet
Now in this article, I gonna setup infrastructure using bastion host so MySQL instances can accessible by ssh and goto internet for update and other stuff.
In my previous article, I create two security groups for WordPress and MySQL but here I am gonna add two more security groups for bastion-host and another which allow ssh access to MySQL.
Create a Security Group for Bastion-admin
resource "aws_security_group" "admin-bastion" {
name = "bastion-host"
description = "ssh login into bastion host"
vpc_id = "${aws_vpc.ashu-vpc.id}"
ingress {
description = "ssh"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "admin-bastion"
}
}
Create Security Group for bastion host which allow ssh for MySql instances
resource "aws_security_group" "bastion-allow" {
name = "bastion-to-mysql"
description = "ssh from bastion"
vpc_id = aws_vpc.ashu-vpc.id
ingress {
description = "ssh"
security_groups =[ aws_security_group.admin-bastion.id , ]
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "bastion-allow"
}
}
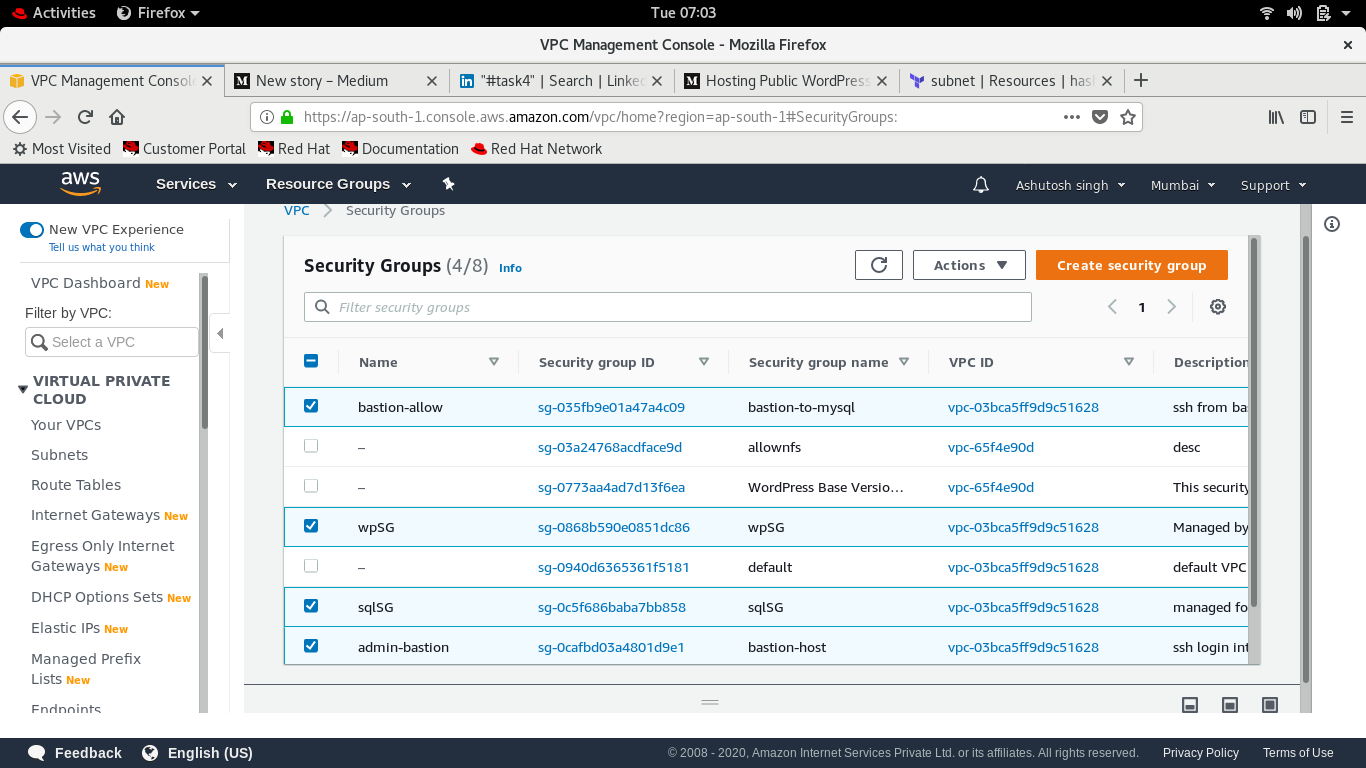
Here you see bastion-host and admin-bastion security group created[pic by author]
#wordpress #terraform #aws #mysql