Introduction
The CI/CD process of an application is crucial to its success and having an easy way to maintain said process can lead to an even healthier lifecycle for the application. Enter infrastructure as code: a reliable method of managing and provisioning pretty much anything you would need in a CI/CD pipeline to get it going, through the use of templates and definitions. Ever needed to keep the configurations of an AWS pipeline somewhere so you don’t need to remember the clicks from the Management Console by heart? Or maybe you wanted to give a working example to a colleague, so they can build their own pipeline. These problems and many more can be solved through infrastructure as code and CloudFormation, if we’re talking AWS.
In the following lines, we’ll go through everything you need to create your own pipeline, connect it with other pipelines and maintain them only by running a not that complicated bash script. And by the end, you’ll probably come to realize yourself how awesome infrastructure as code is (no need to thank us).
Table of contents
- Simple Codepipeline using CloudFormation, The Serverless Framework, and IAM Roles
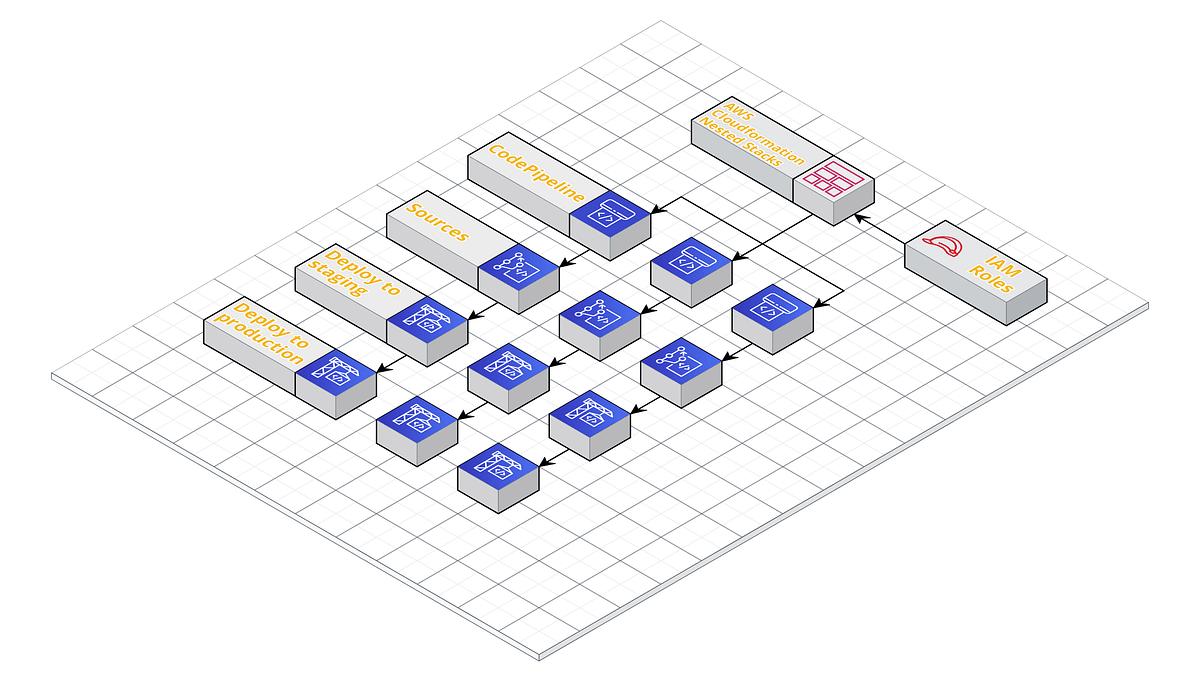
- Complex Codepipeline(s) with AWS Templates and Nested Stacks
- Automation through scripting
Just want to see the code? Here you go:
- Simple pipeline CodeFormation template
- The Serverless Framework catch
- Template with nested stacks
- Automating template packaging/deployment through scripting
CodePipeline using Cloudformation
Building a pipline in AWS’s CodePipeline is pretty simple and conceptually similar to other CI\CD tools out there, but it’s also quite verbose, requiring a considerable amount of code, especially if you want to build your pipeline in an infrastructure-as-code approach.
From a high level there’s 5 main types of resources we need in order for us to put together an AWS Codepipeline:
- **A S3 bucket **resource— where our code artifact will be stored
- A CodePipeline resource— this will model what steps and actions our CodePipeline will include and execute
- IAM Roles — one role that CodePipeline will assume during its execution, in order to create/update/deploy the resources in our codebase. A second role used by a CodeCommit webhook(see #5).
- CodeBuild Project(s) — are used by the CodePipeline resource to execute the actual commands we want in our pipeline.
- An Event Rule — an AWS Event Rule that will act as a webhook triggering the pipeline on each master branch change(this is only required when working with CodeCommit. If you use Github or other supported repo provider there are build-in webhooks)
Now we’ll go over each of the resource types and then we’ll put it all together in a complete CodePipeline.yml definition for a serverless application built on AWS Lambdas using the Serverless Framework(but not limited to these).
#cloudformation #the-serverless-framework #aws-cloudformation #aws-codepipeline #codepipeline