The goal of this challenge is to redirect our execution flow to print the winning statement by leveraging a Global Offset Table (“GOT”) instead of the return pointers that we used for previous Format String vulnerability challenges. Let’s see how we can do this :)
Things to note
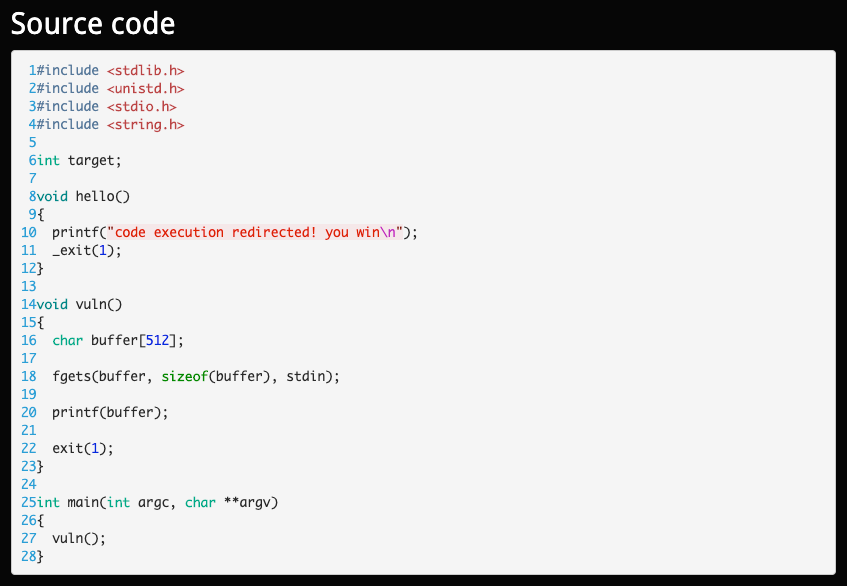
**char buffer[512]**: Setting the buffer size to 512.**fgets(buffer, sizeof(buffer), stdin)**: Getting a user supplied-input. And it limits the buffer size to size of the buffer, which is 512. We can max input with 511 bytes because C always add0x00at the end of the string as a terminator.**printf(buffer);**: This is the vulnerable function in this code. Theprintf()will not check whether the supplied inputs expected format strings or not since it is coded to accept any string values. So what we can do is simply to verify if we can leak the memory addresses and also write arbitrary code onto the stack ([READ]%por%x→ [WRITE]%n).**exit(1);**: Theexit(1)is a syscall, and it simply exits the program. Unlike previous exercises, we do not have any return addresses after theprintf(); instead, we have thisexit(1). But what we can do is since theexit(1)is a part of the Global Offset Table (“GOT”), we can overwrite its entry point for theexit(1)function with the address forhello()to print out the winning statement.
What is GOT?
Source: https://ctf101.org/binary-exploitation/what-is-the-got/
Simply put, GOT helps load shared library functions (e.g., exit()) in a dynamically-linked ELF binary. Basically, one can create their program without re-writing popular functions like exit(); instead, they can add pointers to call those functions as that they can be dynamically loaded at the run time. Example ASM file below:

Disassemble (GDB)
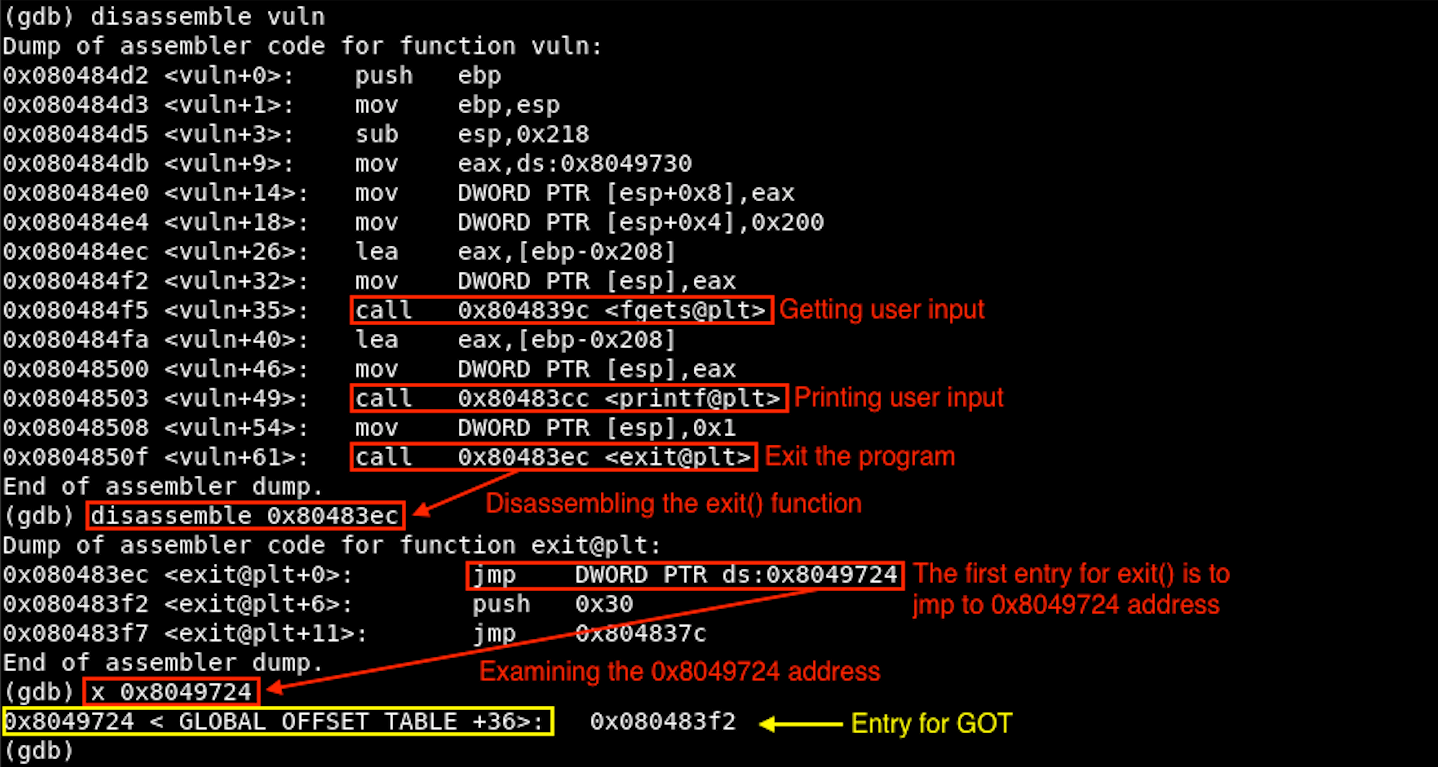
Let’s disassemble the binary to see what is doing at the ASM-level.
$ gdb -q /opt/protostar/bin/format4
Reading symbols from /opt/protostar/bin/format4...done.
(gdb) set disassembly-flavor intel
(gdb) disassemble vuln
 <
<
As we examined from the source code perspective, the program itself is pretty simple. We just need to note the entry address of the exit() function (0x8049724) right now.
#format-string-exploit #protostar-walkthrough #exploit-exercise-format4 #format4-solution #protostart-format4 #string
![[ExpDev] Exploit Exercise | Protostar | Format 4](https://miro.medium.com/max/746/0*7r32PQ2t6XWklu5L.png)