We were using alb ingress controller in AWS EKS. But the main limitation of the ALB ingress controller is that It does support cross-namespaces. To work with multi-namespaces you must deploy ingress in each namespace and it will create another load balancer. It is really very expensive if you have many namespaces. See this post for the details.
So alternative solution is using Nginx ingress controller at https://github.com/kubernetes/ingress-nginx
I deployed from https://github.com/kubernetes/ingress-nginx/blob/master/deploy/static/provider/aws/deploy.yaml
Updated ingress-nginx-controller service with the following annotations terminate TLS on NLB
service.beta.kubernetes.io/aws-load-balancer-type: nlb
service.beta.kubernetes.io/aws-load-balancer-ssl-ports: "https"
service.beta.kubernetes.io/aws-load-balancer-ssl-cert: 'arn:aws:acm:eu-west-1:1234567819:certificate/ef5011e2-c830-4194-b1f1-fbttf'
and deployed a pod and service to test NLB TLS termination.
Used sample apple service from https://aws.amazon.com/blogs/opensource/network-load-balancer-nginx-ingress-controller-eks/
But got some errors.
- 400 The plain HTTP request was sent to HTTPS port
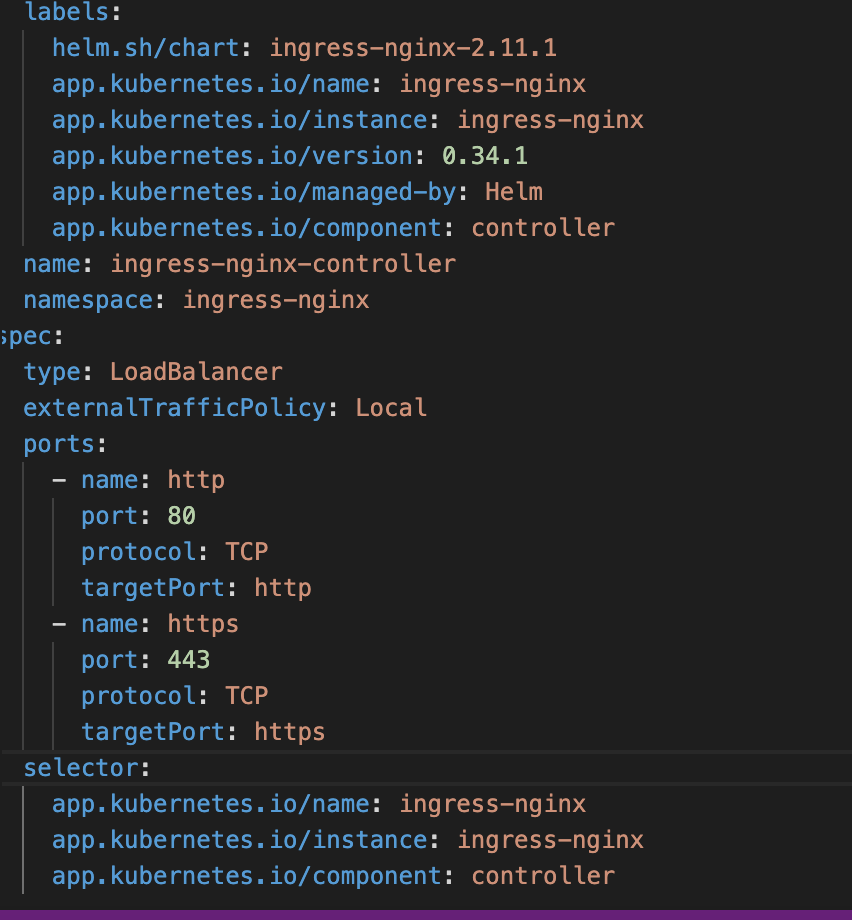
- Default Nginx-ingress-controller service sends HTTPS requests to HTTPS
(targetPort: https)ports. But If we terminate TLS in NLB, did not configure ingress to use TLS then we got400 The plain HTTP request was sent to HTTPS portin the browser. - Solution: Change
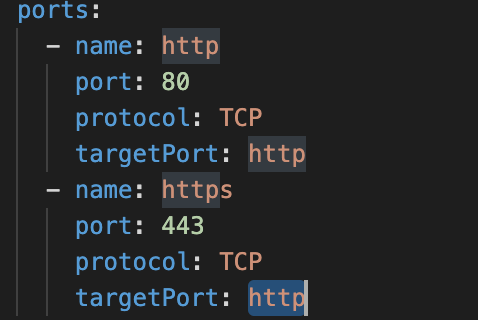
targetPortvalue fromhttpstohttpin https ports settings.
Before:
After:
#aws-eks #kubernetes #tls #nginx-ingress-controller #aws-nlb
