You have heard of the cache poisoning, a bug that had existed for far longer than most of people have been aware, as in many other cases of this nature, in my opinion. But, this article isn’t about a history lesson; however, there are a couple of lessons, maybe more, that you might find useful.
Param Miner with an Edge:
See what I did there? Never mind, it will make itself known soon enough.
Here’s the real world example. Of course I can’t disclose the bbp in question, but the details of the attack won’t make it necessary to do so.
I use Param Miner, an extension for burp pro (technically, it also works in burp community edition, but with a lot of limitations). And, aside from testing for hidden parameters, it also tests for cache poisoning, and then there’s burp pro with its scanner which tests for xss. Add them together and you can get yourself some nice bounties. But, it still requires some legwork.
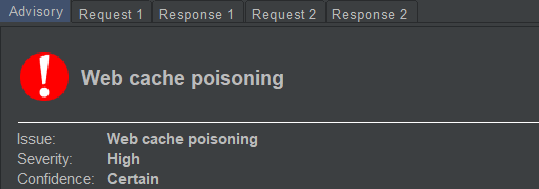
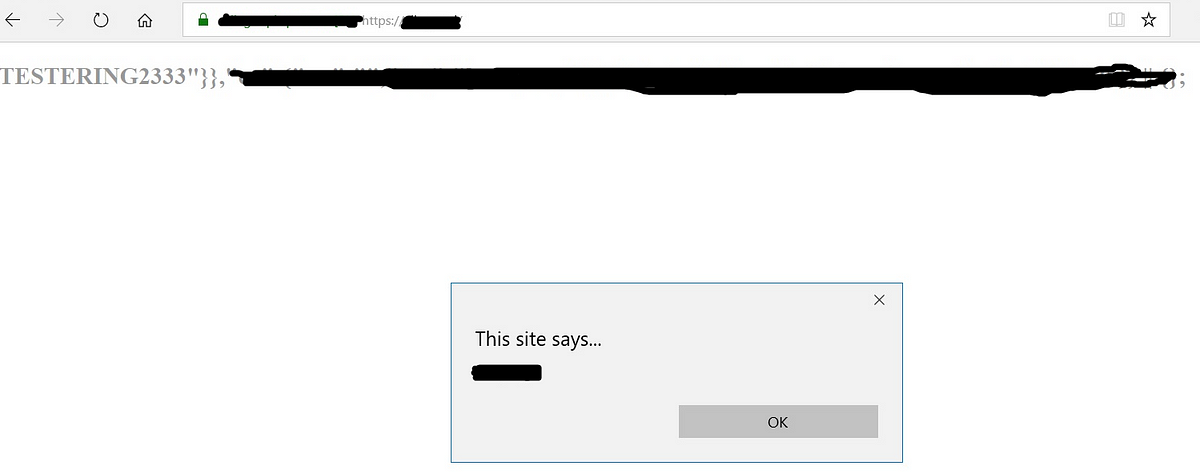
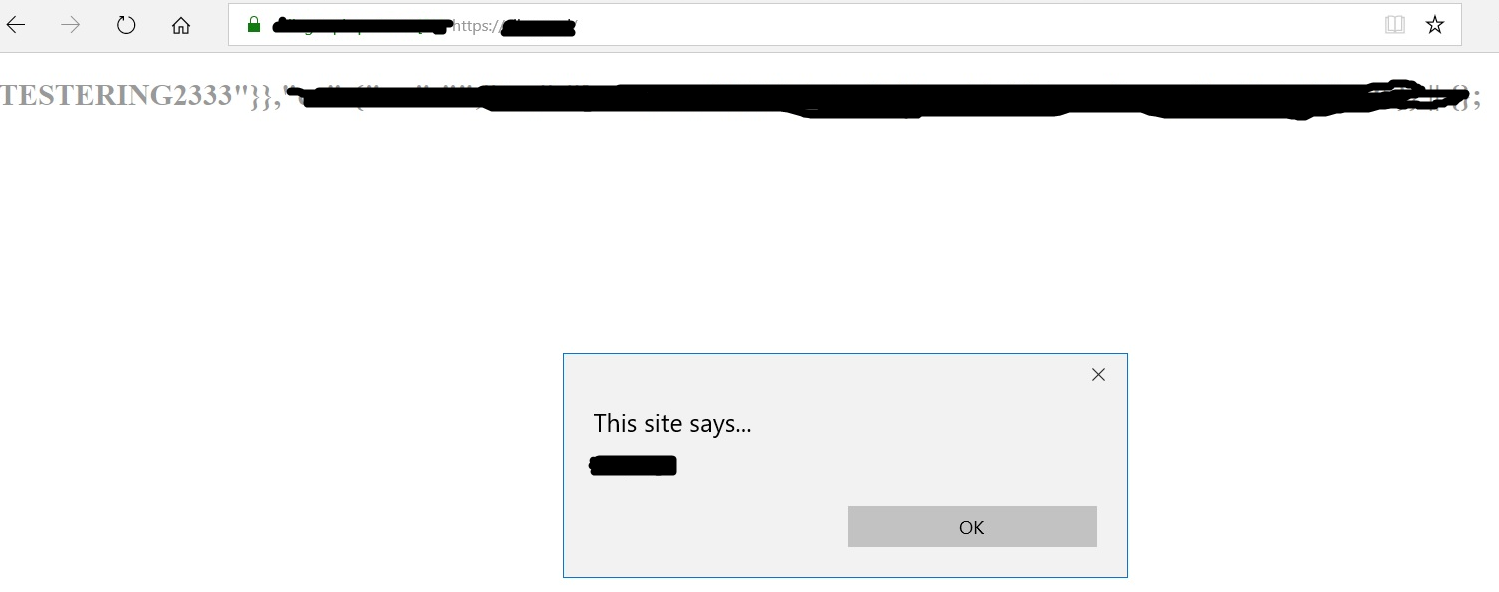
Doesn’t your heart simply swell up by an increase in adrenaline production upon seeing this, or maybe it flutters, or it starts beating stronger. Either way, it means a good news. It did for me. Upon the initial (with hands shaking) review, it turned out that it wasn’t a false positive. Param miner had discovered a hidden header parameter that was reflecting its value inside the body (plot twist) of the website’s main page. Bonus points: the value wasn’t being properly sanitized for xss. Yey.
But, for that initial review, I had been using burp repeater for verification, which was a mistake that took time figuring out. And, it did take me a while. Trying to replicate the results (i.e. website’s main page rendering with xss) was failing when done using firefox. I checked the source code, there was no trace of that param, and therefore no xss. What was going on?
Verification, and actually a PoC:
When in doubt, drink some coffee, and then some more coffee, maybe check what video games are on discount during the week in question, and then get back into the mud of ones and zeroes (not really ones and zeroes, unless if you’re doing some serious stuff which would probably place you far from this article). And then — curl.
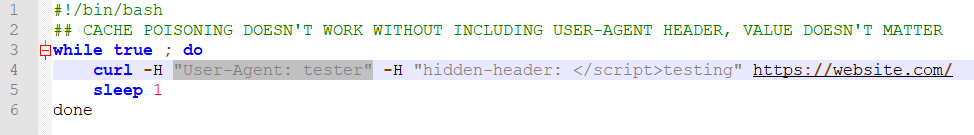
To be more precise,
bash script with curl command used to attack the website:
#bug-bounty-writeup #website-security #bug-bounty #infosec #xss-attack