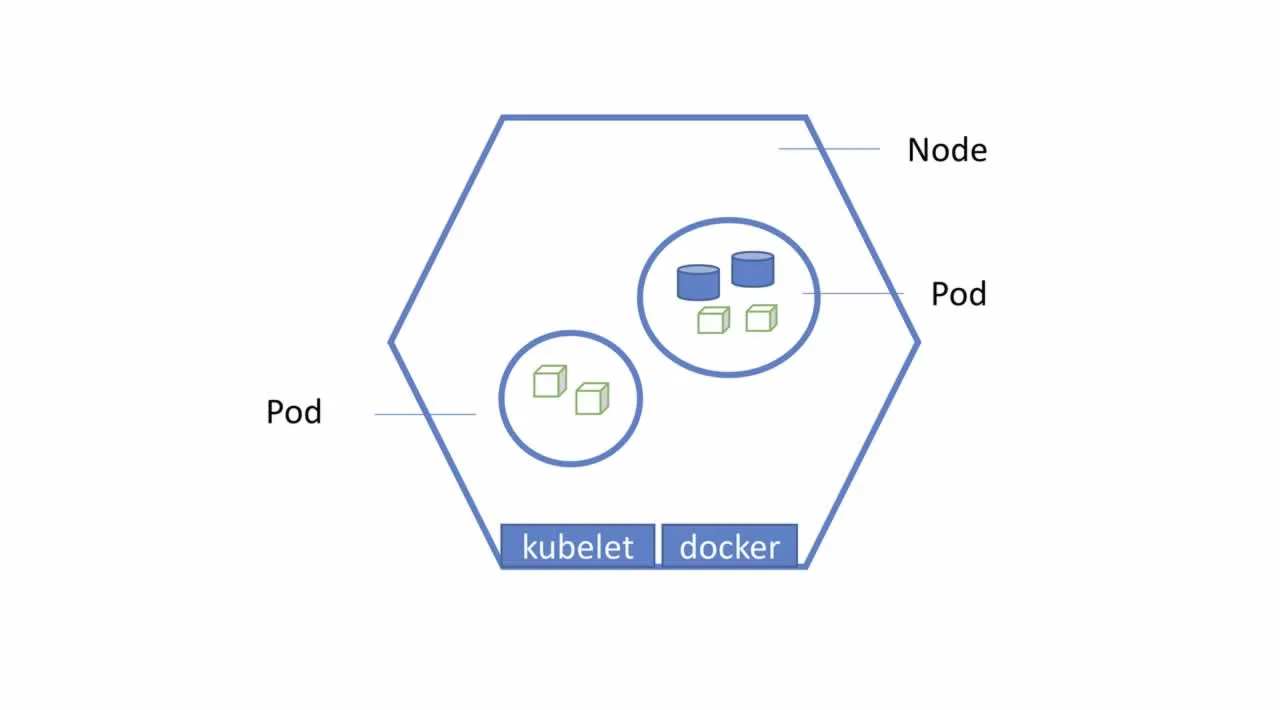
On August 20, 2020, a provider of access management tools released an advisory detailing several misconfiguration issues that affected the kubelet. This feature of Kubernetes functions as the primary “node agent” running on each node. In order to support this functionality, the kubelet maintains full control over a pod running in a node.
As reported by the Container Journal, digital attackers could exploit the misconfigurations described in the advisory to gain access to the kubelet. Subsequently, they could conduct reconnaissance of a cluster, access a container’s app and move laterally in the cluster. This could give malicious actors all they need to gather more information about the pods and run commands within them for the purpose of compromising the Kubernetes environment and stealing sensitive data.
The Importance of Pod Security
The reality is that similar pod-related vulnerabilities and weaknesses will continue to come up. Acknowledging this reality, organizations need to focus on protecting their pods. StackRox couldn’t agree more with this observation:
A critical cornerstone of any Kubernetes security strategy is to secure the pods and containers that make up your clusters. The good news is that Kubernetes itself as well as its ecosystem make available multiple types of flexible capabilities and tools that enable you to protect pods in ways that range from applying general security best practices to meeting specific, fine-grained requirements based on workload type or other needs. Kubernetes security context and security policies, including Pod Security Policies, are the best way to get started and immediately increase the security of your Kubernetes applications.
This blog post will explain how organizations can use security contexts to keep their pods safe. It will then discuss how organizations can enforce those security contexts using three different types of pod security policies. Finally, the blog post will provide some insight into how organizations might look beyond pod security policies to address their pod security needs.
#kubernetes #security