Introduction
In our earlier article, we explained a custom API for fetching the key vault secrets that were built using Azure API Management Gateway and Azure Functions to provide an endpoint for doing the operation. In this blog, we are going to create another endpoint for generating a new Azure Active Directory BearerToken using a managed identity assigned to Azure Function. This API will be using the same architecture as described in the earlier article.
Ok, so now that we have laid the groundwork, let’s begin by understanding why we need this? The first thing that any developer will have to figure out for performing any operations (CRUD) in a controlled Azure environment is a way to authenticate the application with Azure to get the required token, even though Microsoft has provided many custom solutions for authentication which can be implemented in custom applications to retrieve access tokens.
One of the most commonly used authentication approaches is a service principle-based approach where we would create a service principal in Azure Active Directory and then assign required permissions on APIs against which the access token is to be retrieved. After the service principal is created, we will write the authentication module using the created service principal client ID, client secret, and resource URI of the API on which permissions were granted in Azure Active Directory. There are a few problems with this approach:
- Service Principle details need to be shared with all applications or we will need to create separate service principles for each application
- Password rotation policies become extremely tricky to apply in multi-usage scenarios
- Additional overhead if we have to do this at more than one place and more than one module/application as it will need to rewrite those solutions at each place.
- To comply with security standards, we will have to move service principle details to the key vault and then implement a module (we have done that using API in an earlier blog) to fetch it and use in the authentication module
This is where this particular API comes into the picture. This custom API will take care of the authentication module and can be reused. With this custom API, we will:
- No longer need the service principle as we will be using User Assigned Managed Identity
- Not rewrite of the authentication-related code in every module/functionality
- Provide a single end-point to generate bearer token for any given resource URI, like https://management.azure.com, https://vault.azure.net, etc. to use respective Azure REST APIs
- Use a generated bearer token to perform any kind of operations in Azure using Azure REST APIs of resource Uri against which token is generated
- Use generated bearer token to invoke REST APIs from any platform
As stated above, we are creating this API on the same lines as our previous API so all pre-requisites are applicable here with additional pre-requisite i.e. User Assigned Managed Identity. We have to create a User Assigned Managed Identity in Azure and need to add the same at Azure Function App created in the previous article. Let’s do it by following the below steps.
- Go to the function app (created in the above-mentioned article) in Azure Portal
- Navigate to Identity option available under the Settings section
- Click on “user assigned” tab and click on Add button
- Now, on the displayed form, select the subscription under which we have created our user-assigned managed identity, search that identity in the search box and select it.
- Now, click on the Add button.
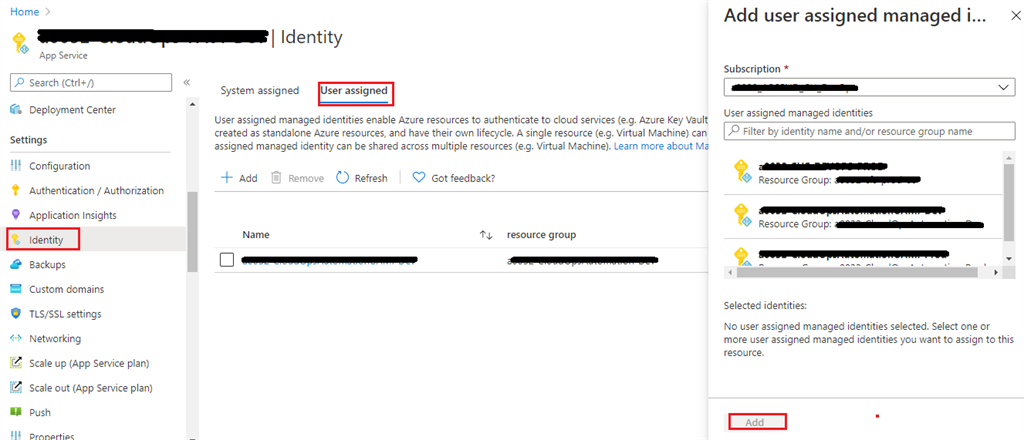
Once this is done, created identity should be granted with Contribute/Owner access at subscription/resource group under which resources are to be accessed, updated, created, or deleted in Azure.
Note
For details on Managed Identities, please go through this article.
Now that we are ready with all pre-requisites, let’s jump right to writing API code.
Open the master solution created in an earlier article, in VS code, and create a new Azure Function Project with C# as the language, “GenerateBearerToken” as a function name, HTTP Trigger as the Function Template and Authorization level as Anonymous/Function (this is required for API Management). This will create a class file with the name “GenerateBearerToken.cs”.
Now, lets code the Azure Function to generate Bearer Token against Azure Active Directory using User Assigned Managed Identity. Open GenerateBearerToken.cs file and update the below code in it.
#azure #azure-api #aainst-azure
