Publicly accessible web servers receive requests from both legitimate and malicious users. It is important to recognize them both and take appropriate actions to process only those requests that should be processed, and serve only those content that should be served.
In simpler terms, there are two distinct types of attacks against web servers, one that is targeted towards an organization or a domain, and other that is non-targeted which attempts to compromise any publicly accessible web server. A targeted attack might compromise the web application hosted, rather than the server software itself.
Hardening
When we talk about non targeted, the attack vector typically involves exploiting known vulnerabilities, misconfigurations and using openly available information about the web server software. Hardening the server makes it very difficult for the attacker to compromise the entire system, and limits the progression of the attack.
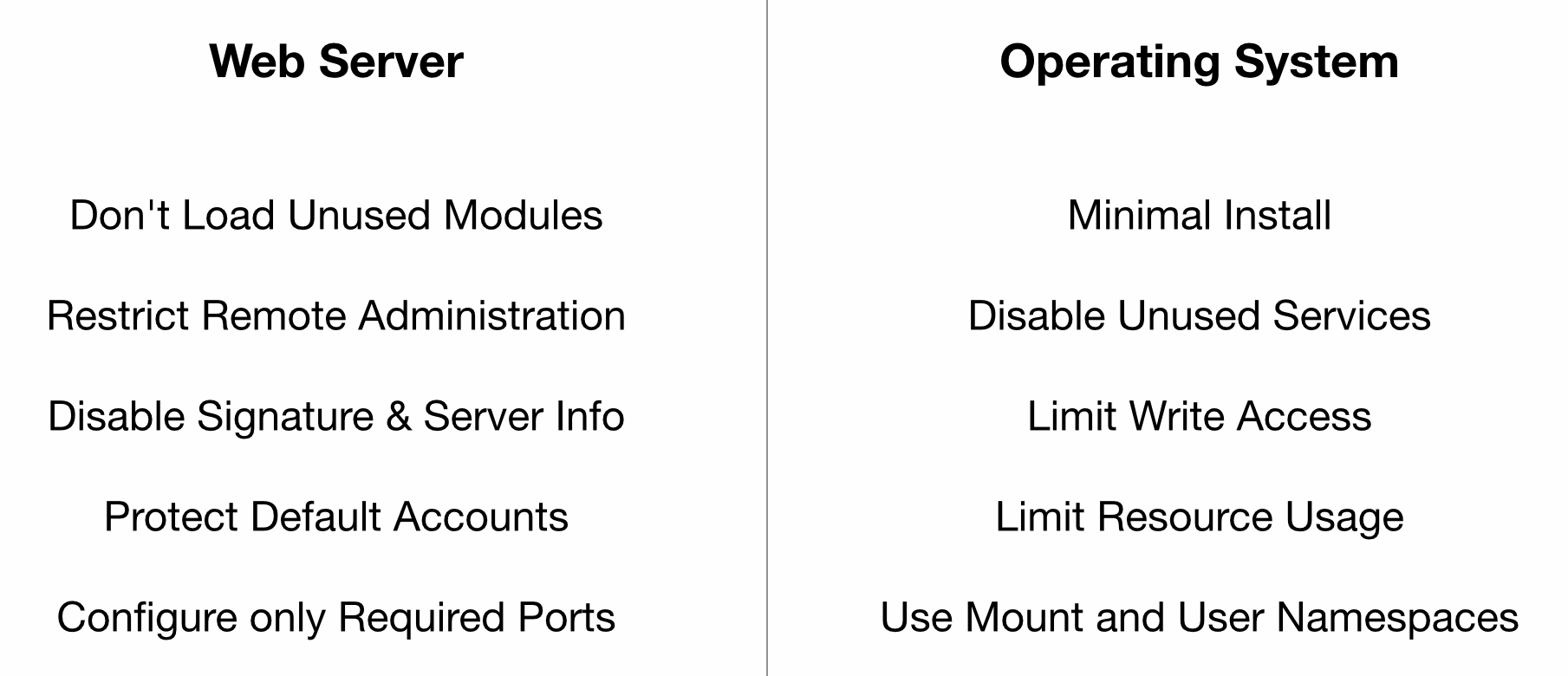
At a high level, hardening is about limiting the capabilities of the web server and the operating system. The web server might have features that may not be relevant to the deployment and could be turned off. This may mean modifying the default configuration files, loaded modules, permissions of files and directories, and so on. On the operating system side, by default, there will be installed tools and enabled services that are not required in a production environment. They should be removed/disabled.
Hardening web servers will not protect an organization from targeted attacks. However, it is the first step towards it and will protect the web server from non-targeted attacks.
#web-server #web-development #security #developer
