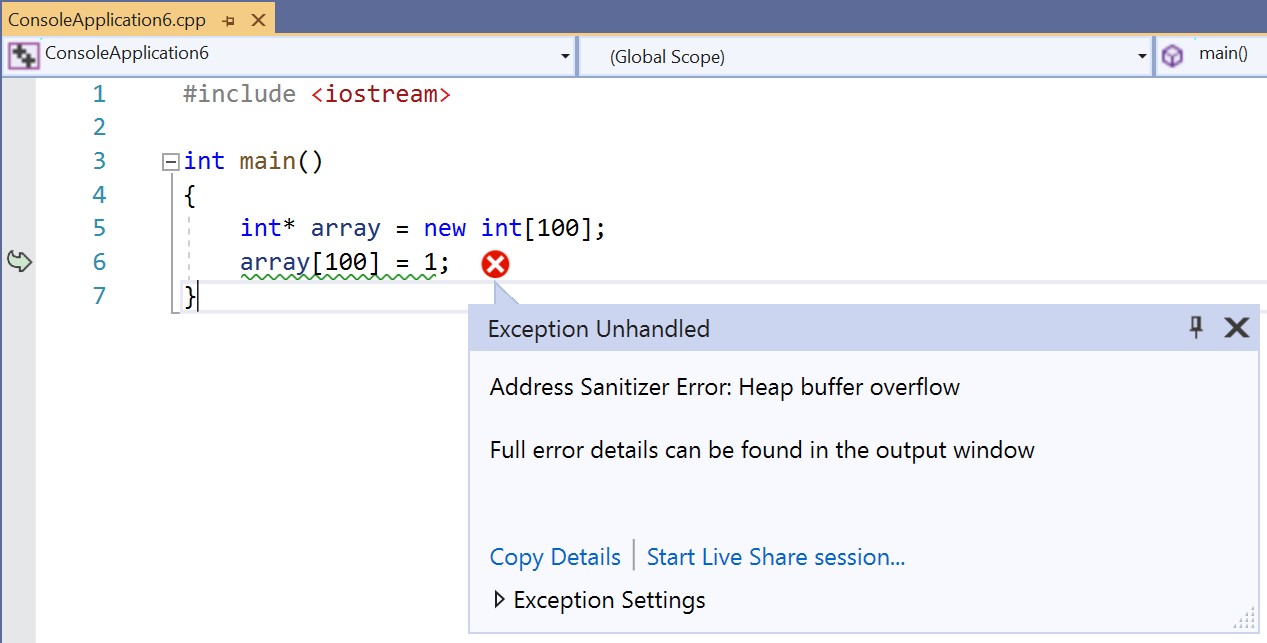
Last October, we announced AddressSanitizer support for Windows as part of the x86 retail MSVC toolset. This included an IDE experience in Visual Studio with AddressSanitizer error reporting, visualized in dialog boxes anchored to the source code where the error was caught. AddressSanitizer was designed by Google to improve memory safety in programs by identifying violations. It reports precise errors using source lines and symbols. Most importantly, it reports no false positives.
As of Visual Studio 2019 version 16.7, we support both x64 and x86 targets. Both targets also have full support for Debug and fully optimized Release builds. These compilers produce the new code generation and metadata required to interop with the AddressSanitizer runtime. They support this new functionality with all levels of optimization.
To support the IDE and testing workflows, we have included a new** vcasan.lib.** This small, static library creates metadata the IDE will parse to support error reporting in its sub-panes. This metadata is stored in the Crashdump (.dmp) files produced when a program is terminated by AddressSanitizer when an issue is found. These .dmp files are commonly used to debug causes of unexpected program crashes and can easily be shared with others to replay the program’s behavior in Visual Studio prior to the crash. This functionality allows executables to take advantage of a snapshot process type unique to the Windows operating system.
To fully support those design goals for the Windows platform, we have made changes to enhance the open source runtimes and have more to contribute back to the community. We have fixed bugs in our tools thanks to customers who were early adopters and building large internal systems like Office, all using “–fsanitize=address.” Finally, we have extended functionalities across the C++ developer stack on Windows. We have more to come in 16.8.
Getting Started with AddressSanitizer for Windows
For more information on how to get started, including installing the necessary components for Visual Studio, enabling build system integration, and running ASan from the command line or IDE, take a look at our previous blog post, AddressSanitizer for Windows with MSVC.
Features available in 16.7
These are AddressSanitizer features (64-bit and 32-bit) that your code can leverage in the 16.7 release:
- stack-use-after-scope
- stack-buffer-overflow
- stack-buffer-underflow
- heap-buffer-overflow (no underflow)
- heap-use-after-free
- calloc-overflow
- dynamic-stack-buffer-overflow (alloca)
- global-overflow (C++ source code)
- new-delete-type-mismatch
- memcpy-param-overlap
- allocation-size-too-big
- invalid-aligned-alloc-alignment
- use-after-poison
- Intra-object-overflow
- Initialization-order-fiasco
- double-free
- alloc-dealloc-mismatch
#c++ #cplusplus #programming-c