In this article, I will be continuing my walkthrough of the _InsecureBankv2_Android application created by the GitHub user dineshshetty. Check out Part 1 & Part 2 to see how to setup the application and some of the application’s insecurities I have already demonstrated. I have left a link to application’s GitHub repository in the references below.

Disclaimer
As I stated in Part 1 & 2, I was inspired to make this article out of an interest to learn more about Android mobile application security. This article will obviously contain spoilers about the vulnerabilities present in the InsecureBankv2 Android application. I encourage readers to exploit as many vulnerabilities as they can and then come back later to read this article if you get stuck or want to see a potentially different approach to exploiting an insecurity. Lets get started 😄!
Root Detection Bypass
Each time I successfully login, the new activity contains a message saying that the device is rooted (i.e. “Rooted Device!!”).

Looking at the source code for the “PostLogin” activity, I can see a method called “showRootStatus()” which returns a message based on whether the device is rooted or not.

Looking at the source code above, two methods called “doesSuperuserApkExist()” and “doesSUexist()” are used to determine if the device has been rooted. The source code for both methods can be seen below.
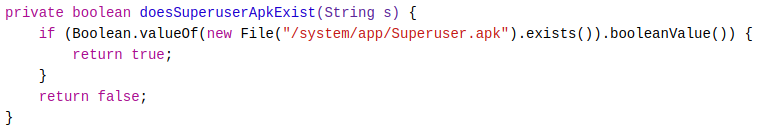
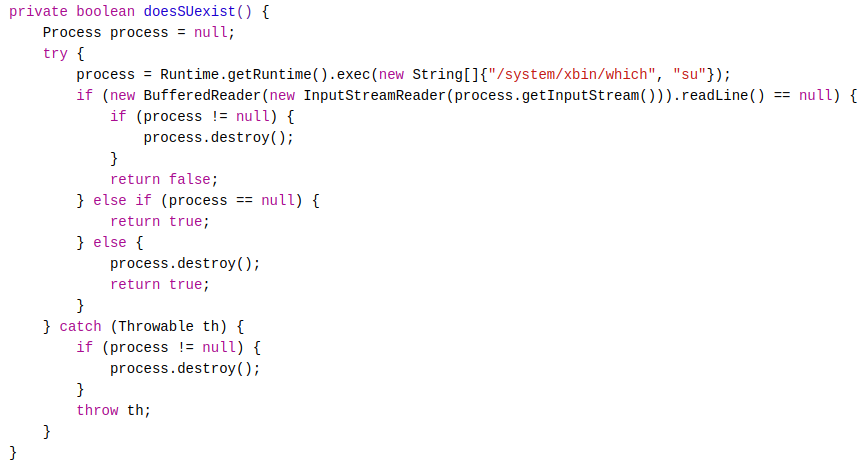
To bypass root detection, I can use Frida to hook both boolean methods and make them return** false **using the script seen below.

The python script used to load this hook is provided below.
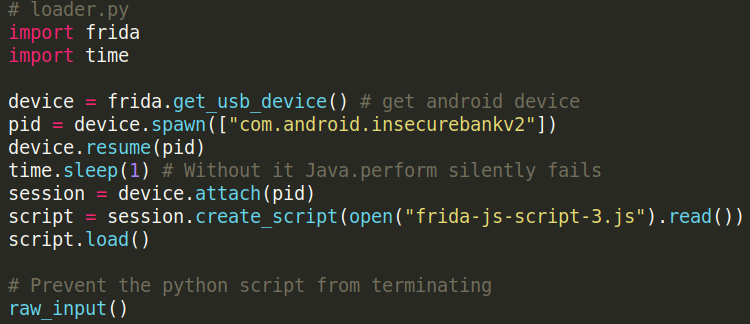
#cybersecurity #technology #reverse-engineering #application-security #android
