As the word implies, in a zero-trust security model, no device or user is trusted. And, every request received by the system goes through the validation and authentication steps. This essentially means, no device or user enters the private network of the organization, and only the application hosted on the edge provides access to them.
This is in contrast to the model of the trusted device, where on successful authentication, the device is trusted and is allowed access to the private network, such as in the case of Enterprise VPNs. The downside to this model is, when the trusted device gets compromised, the entire private network may be at risk. The upside is flexibility. When you have services using different protocols such as IMAP, XMPP, RDP, SSH, SMB, NFS, and so on, how do you authenticate every request at the edge?
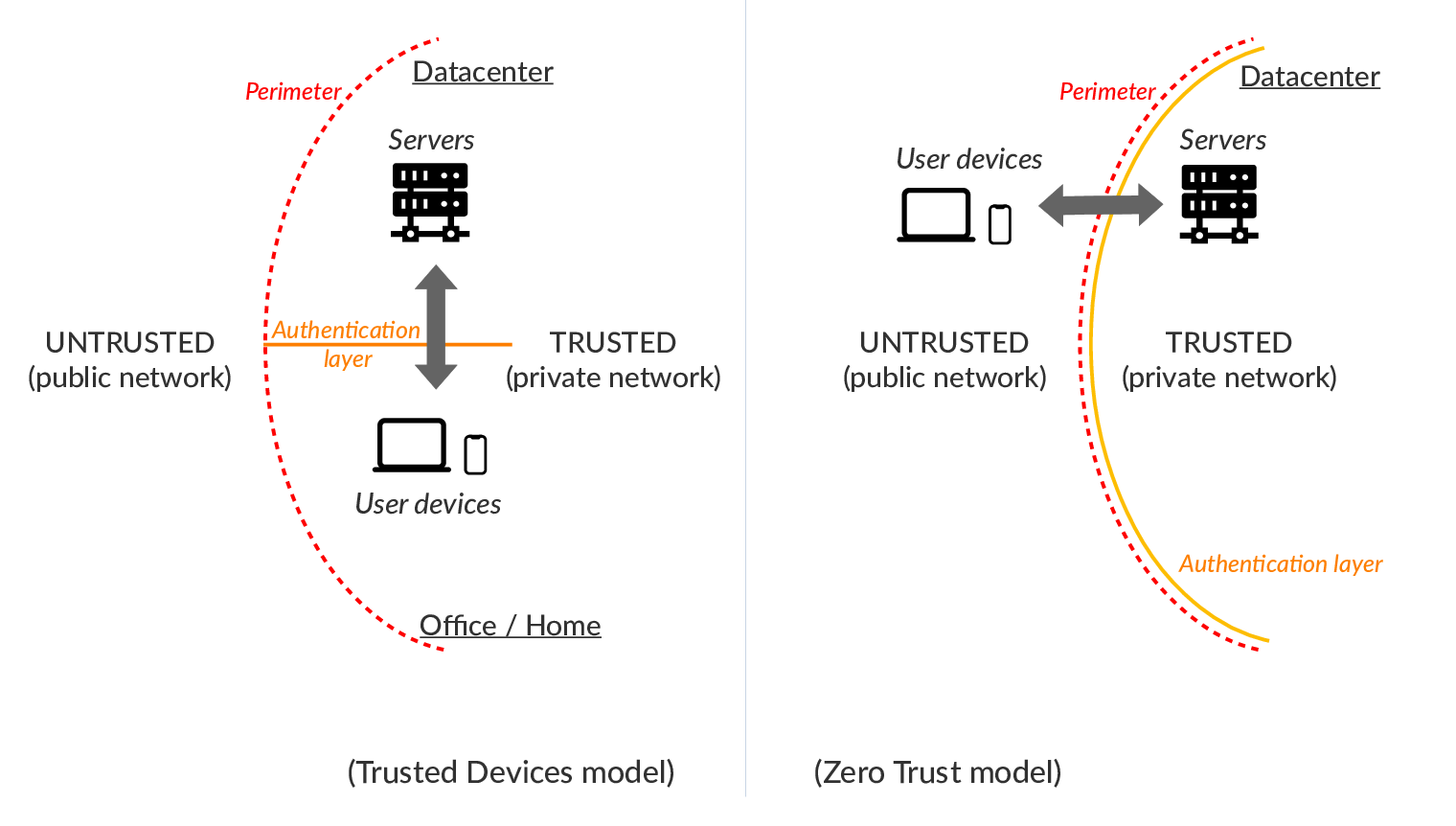
As more and more services are available as web applications, it has become possible to deploy an application proxy on the edge, that authenticates and grants access to internal web applications. This provides zero-trust security if the authentication method used is robust and secure. Currently, the most popular authentication method is OAuth 2.0.
#cybersecurity #devops #ssl #information-security #https