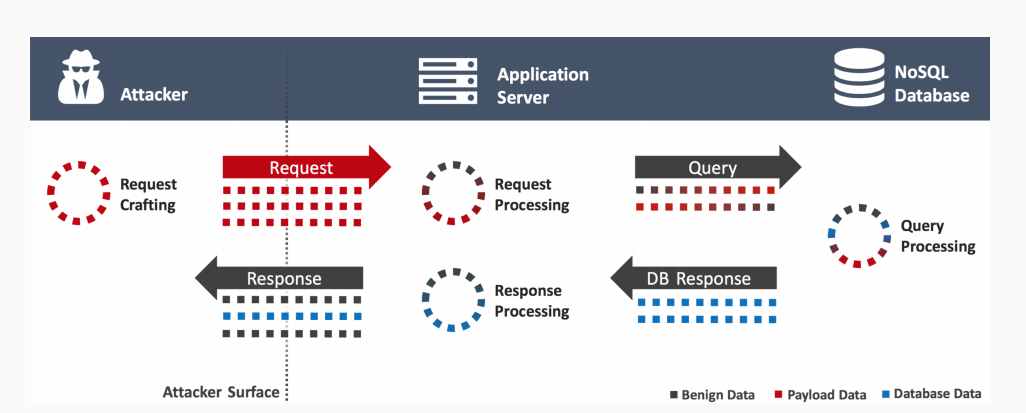
From NoSQL Injection to Serverside Javascript Injection
NoSQL (not only SQL) has disrupted the usage of traditional data stores. It has introduced a new concept of data storage which is non-relational unlike the previous storage mechanisms and thus, provides looser restrictions in consistency. It has a document store, key-value store, and graph. Due to the new requirements of modern-day applications, there has been wide adoption of NoSQL databases which could conveniently facilitate the distribution of data across numerous servers. Nosql databases provide an avenue for wide scalability and they require a single database node to execute all operations of the same transaction
NoSQL models offer a new data model and query formats making the old SQL injection attacks irrelevant. Yet, they give attackers new ways to insert malicious code.
Let’s understand the NoSQL data models in MongoDB:

The following diagram illustrates a query that selects and orders the matching documents using an index:
Read operations retrievesdocuments from acollection i.e. queries a collection for documents. This is how you can read the documents from a collection in MongoDB:
db.items.find(queryObject)
db — current database object
Items — collection names ‘items’ in the current database
find — method to execute on the collection
queryObject — an object used to select data
queryObject = {amount:0}; //items with fixed value ‘amount’ is 0
Before we go any further, let’s quickly analyze the attack mechanism in traditional SQL databases.
#security #vulerability #programming #web