*The importance of risk management is to identify the potential problems before it emerges usually, they occur unconditionally. It helps the IT managers to balance the CAPEX/OPEX costs in the organization and also take protective measures and gains much control power.
Risk management comprises three processes as Risk assessment, Risk Mitigation, and Risk evaluation. Risk Management is a recurrent activity that deals with the analysis, planning, implementation, control, and monitoring of implemented measurements and the enforced security policy. Risk IT provides an end-to-end, comprehensive view of all risks related to the use of information technology (IT) and a similarly thorough treatment of risk management, from the tone and culture at the top to operational issues. **Risk=((VulnerabilityThreat)/CounterMeasure).**

- The standard risk assessment methodologies form part of a risk management and assessment process depicted below in the figure which enables an organization to effectively identify, assess, and treat risks.
the risk is the product of likelihood times impact
The measure of an IT risk can be determined as a product of threat, vulnerability, and asset values:
1. A study of the vulnerabilities, threats, likelihood, loss or impact, and theoretical effectiveness of security measures. Managers use the results of a risk assessment to develop security requirements and specifications.
2. To determine expected loss and establish acceptability to system operations.
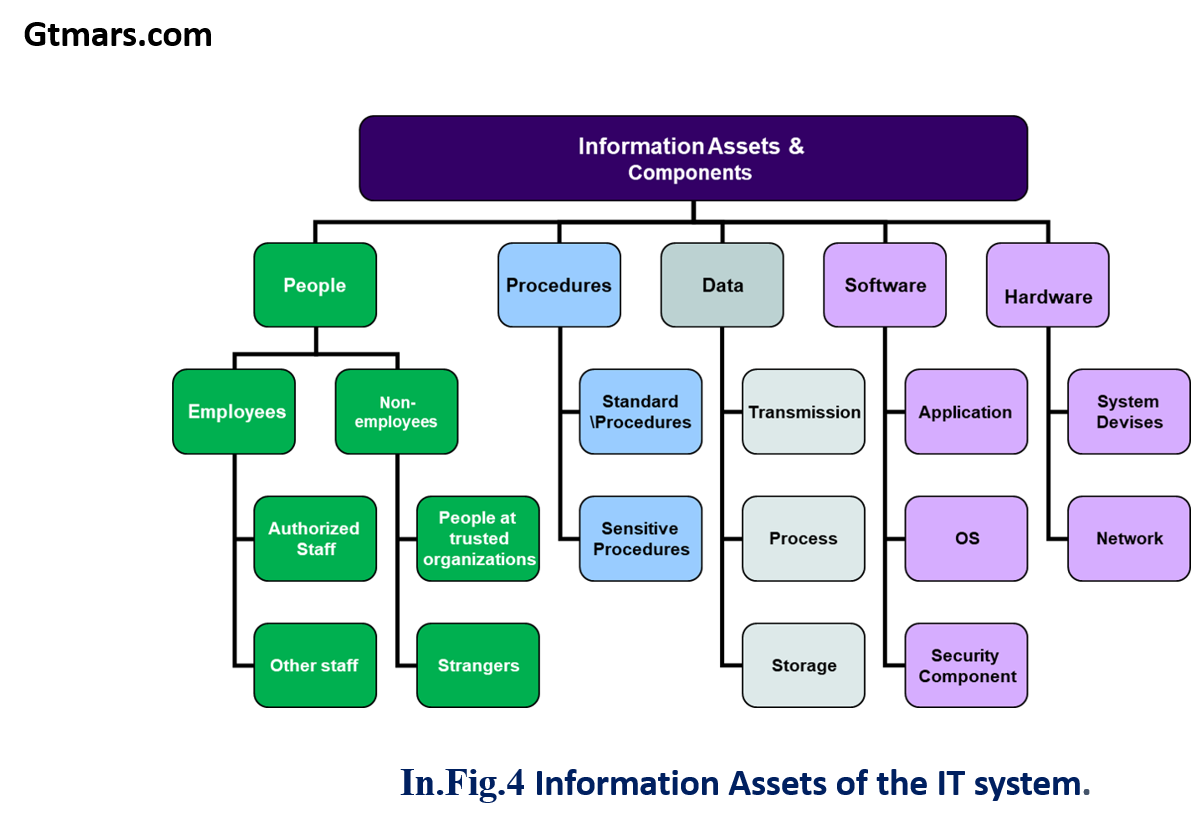
3. Identification of a specific ADP facility’s assets, the threats to these assets, and the ADP facility’s vulnerability to those threats.
4. The purpose of a risk assessment is to determine if countermeasures are adequate to reduce the probability of loss or the impact of loss to an acceptable level.
5. A management tool that provides a systematic approach for determining the relative value and sensitivity of computer installation assets, assessing vulnerabilities, assessing loss expectancy or perceived risk exposure levels, assessing existing protection features and additional protection alternatives or acceptance of risks, and documenting management decisions. The ISO/IEC 27002:2005 Code of practice for information security management recommends the following examined during a risk assessment:

*To determine the likelihood of a future adverse event, threats to an IT system must be analyzed in conjunction with the potential vulnerabilities, and the controls in place for the IT system. Impact refers to the magnitude of harm a threat’s exercise of vulnerability could cause that.
#cloud-computing #organization #security #risk-management #management