Summary:
For this machine, using gobuster command exposed the credentials to access the open FTP port which led to finding out about the vulnerable MySQL database that allows foreign server to import arbitrary data exposing credentials. i.e. you could implement a local database and table giving full privilege and connect it to the vulnerable MYSQL database.
For root, a script was found to execute as root using sudo command. Upon reviewing the script code, the Python Library Hijacking technique was then attempted to escalate privilege to get root.
Tools Used:
Nmapgobustergunzipandtar -xvfmysql -h localhost -u <username> -psudo -lnc- Custom python script exploit
Enumeration
Nmap TCP Output
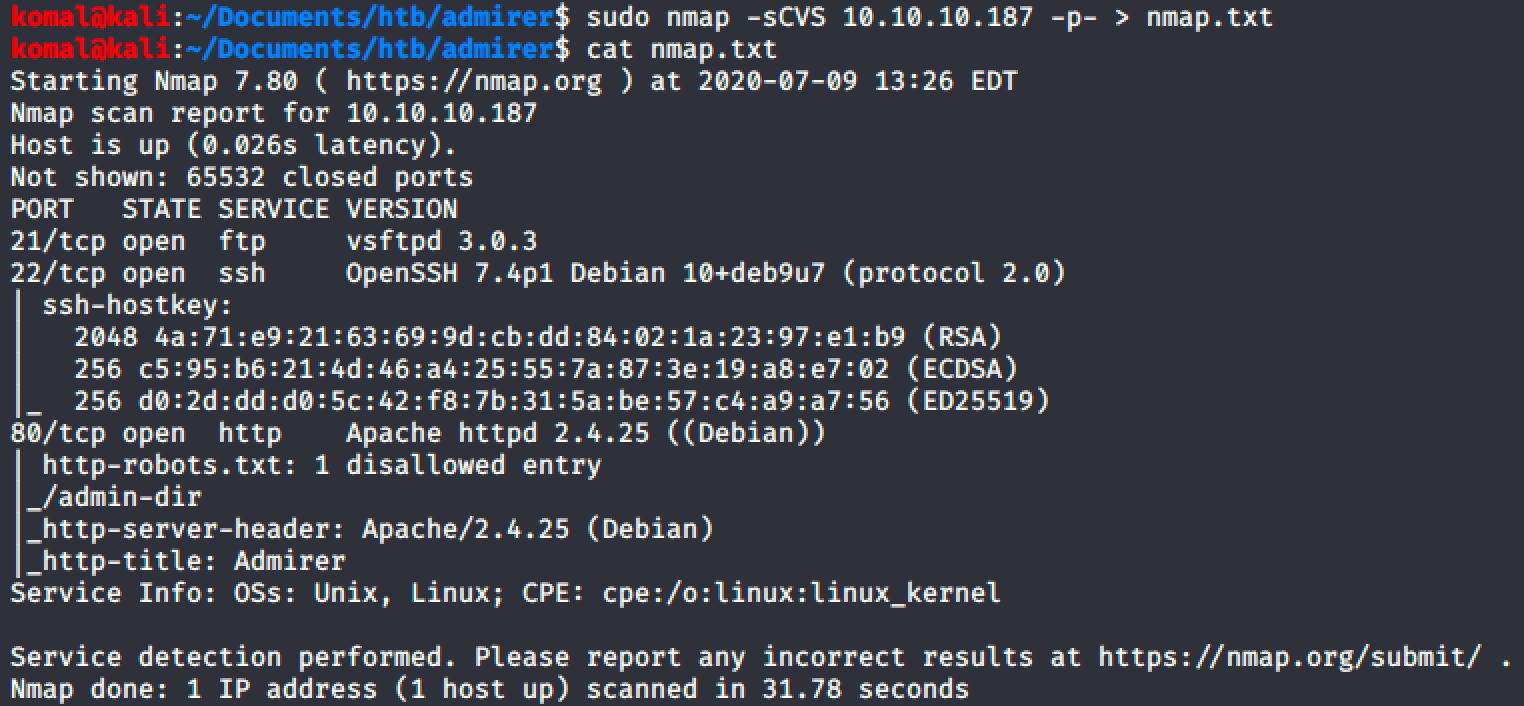
************* PORT 80 HTTP *******************************************
The** /admin-dir** directory was found within the robots.txt file.
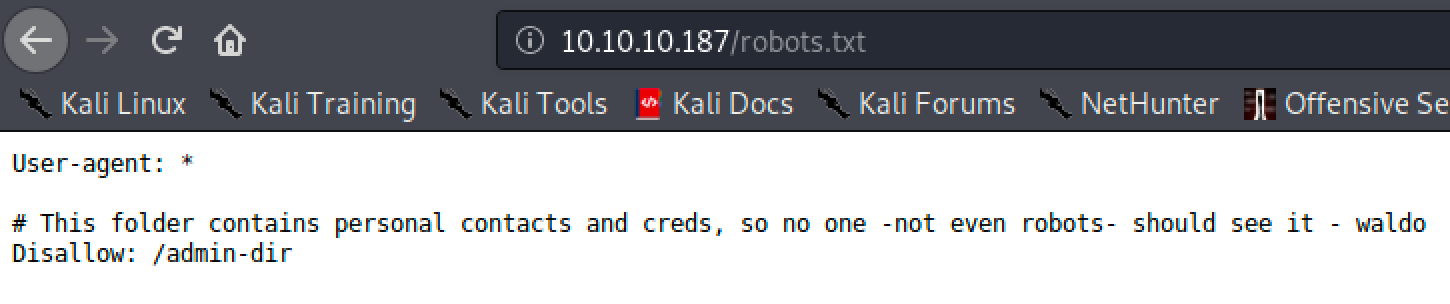
Looks like the /admin-dir has something juicy.
#vulnerability #pentesting #hackthebox #htb #database
![HTB Admirer [Writeup]](https://miro.medium.com/max/586/1*wH-r4b8ianduGWjPucZUpQ.png)