The first thing that will come to your mind, at least it did to ours, is - ‘Doesn’t Microsoft have its own APIs to fetch secrets from Azure Key Vault?’ Well, the answer is Yes, they do. So then, what are we trying to achieve here? We will hopefully address that question during the course of this blog which is going to be slightly long due to the need to explain the setup and architecture along with the API (further blogs will reference this).
Okay, so let’s first visit what Microsoft has to offer. Microsoft has APIs listed for fetching keys, fetching secrets, getting lists etc. for the Azure Key Vault right here. As you notice with the secrets API, all of the calls require - (a) the Key Vault API end-point URL, (b) the secret value name that your looking for © secret version (even if there is only one version) that you need and the most important one which is not listed and is kind of read between the lines (d) a Bearer Token to authenticate to Azure Key Vault.
So, assuming that you would need to do this at more than one place and more than one module/application, all of the modules that will need to fetch anything from the key vault, will need authentication details like application id, application secret and tenant id to be provided. This becomes an overhead in a large solution or the pizza box teams that we work with in the modern environments. Here is where the API that we are trying to build comes into the picture. With this API, we will
- eliminate the need to implement authentication details with all teams/modules
- eliminate the need to provide the secret versions
- provide a simple end-point to get any secret from Azure Key Vault
- remove the need to rewrite logic in every module/functionality
We are going to create an Azure Function to host the API end-point which is then exposed and made available to end users via the Azure API Management Gateway. This provides us with more control on the access with a product-subscription model, implements policies, and also allows us to do any tweaks with end-points or make only a few functions availalbe instead of all via specific product subscriptions. In addition, the hosting end-point on Azure Function also seems a little more cost effective compared to hosting on App Services (due to the fact that we pay only usage with Azure Function versus paying for App Service Plans or App Service Environment costs). The below diagram briefly describes the overall architecture,
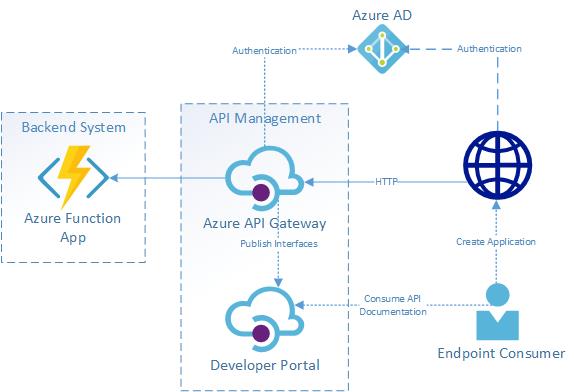

Now that we have covered the overall architecture that will be used in subsequent reusable API endpoints that we will set up, let’s jump right into building this one! So, what do we need before starting to write the code?
- Create an Azure Function resource in Azure
- Configure System Assigned Managed Identity to the created Azure Function resource
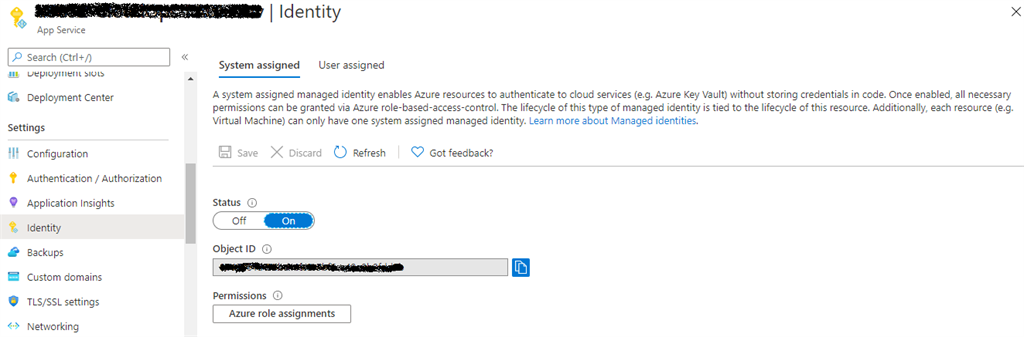
- Provide access to configured System Assigned Managed Identity at the target Key Vault Resource (from where secret is to be fetched) via Access Policies
- Visual Studio Code or Visual Studio (IDE of your choice) setup with Azure Function configurations. If you are using VS Code, install the Azure Functions extension
- Create an Azure API Management Service in Azure
#api #coding #creating #azure api #key vault
